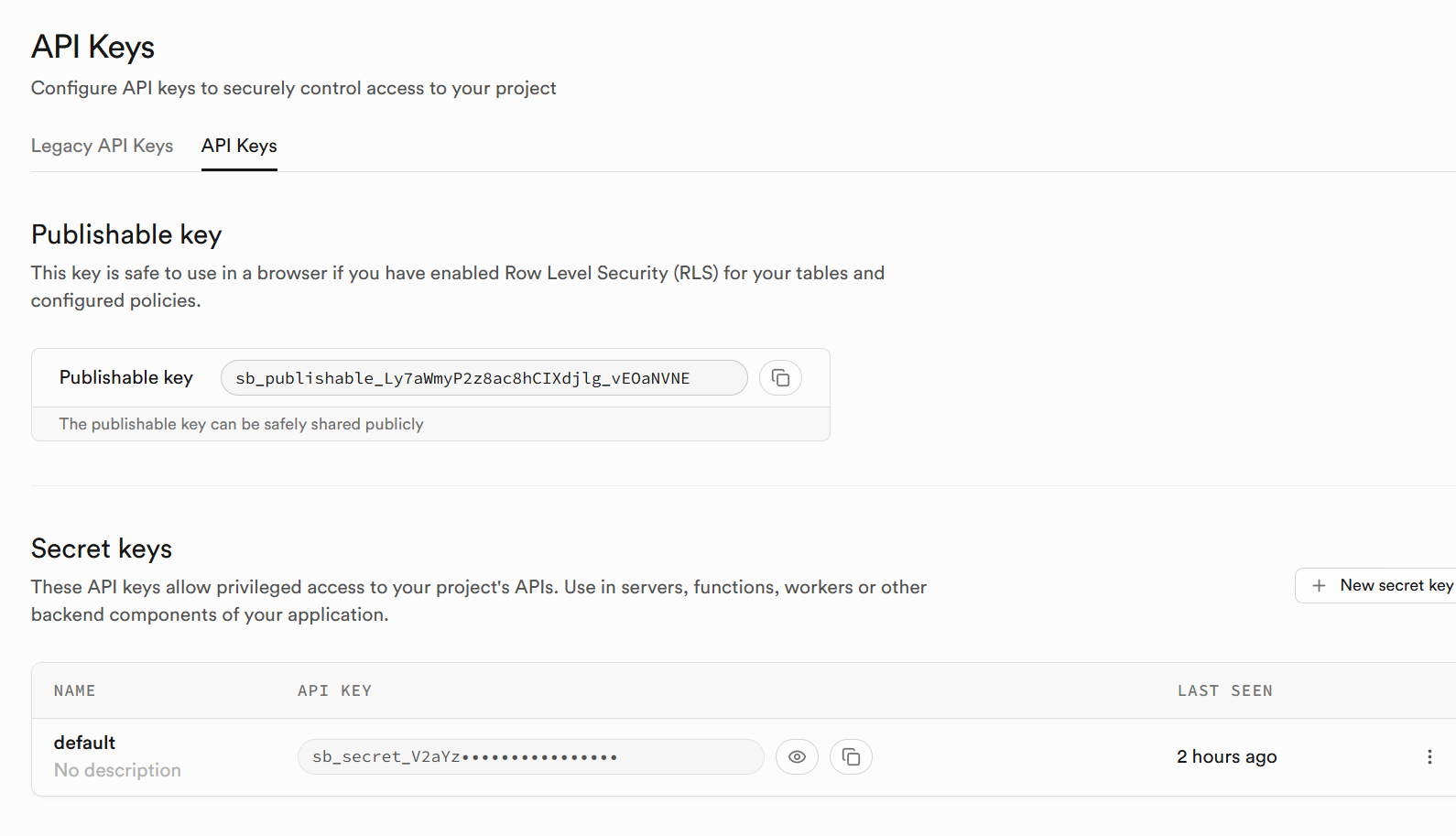
Legacy api keys used even if disabled?
 edge functions
edge functionsI have disabled legacy api keys and enabled the new keys. now I call an edge function and I get this error: Authentication error: Legacy API keys are disabled
could it be that the edge function secrets have not been updated? because I created the branch then disabled legacy keys
could it be that the edge function secrets have not been updated? because I created the branch then disabled legacy keys
import { createClient } from 'npm:@supabase/supabase-js@2';
const corsHeaders = {
'Access-Control-Allow-Origin': '*',
'Access-Control-Allow-Headers': 'authorization, x-client-info, apikey, content-type'
};
const supabaseServiceRoleKey = Deno.env.get('SUPABASE_SERVICE_ROLE_KEY');
if (!supabaseUrl || !supabaseAnonKey || !supabaseServiceRoleKey) {
console.error('Server configuration error: Missing Supabase environment variables.');
return new Response(JSON.stringify({
error: 'Server configuration error.'
}), {
status: 500,
headers: {
...corsHeaders,
'Content-Type': 'application/json'
}
});
}
const authHeader = req.headers.get('Authorization');
if (!authHeader) {
return new Response(JSON.stringify({
error: 'Missing Authorization header.'
}), {
status: 401,
headers: {
...corsHeaders,
'Content-Type': 'application/json'
}
});
}
const supabase = createClient(supabaseUrl, supabaseAnonKey, {
global: {
headers: {
Authorization: authHeader
}
}
});
const supabaseAdmin = createClient(supabaseUrl, supabaseServiceRoleKey, {
auth: {
autoRefreshToken: false,
persistSession: false,
detectSessionInUrl: false
}
});
console.log("Authenticating user...");
const { data: { user: authUser }, error: authError } = await supabase.auth.getUser();
if (authError || !authUser) {
console.error('Authentication error:', authError?.message || 'No user found.');
return new Response(JSON.stringify({
error: 'User not authenticated.'