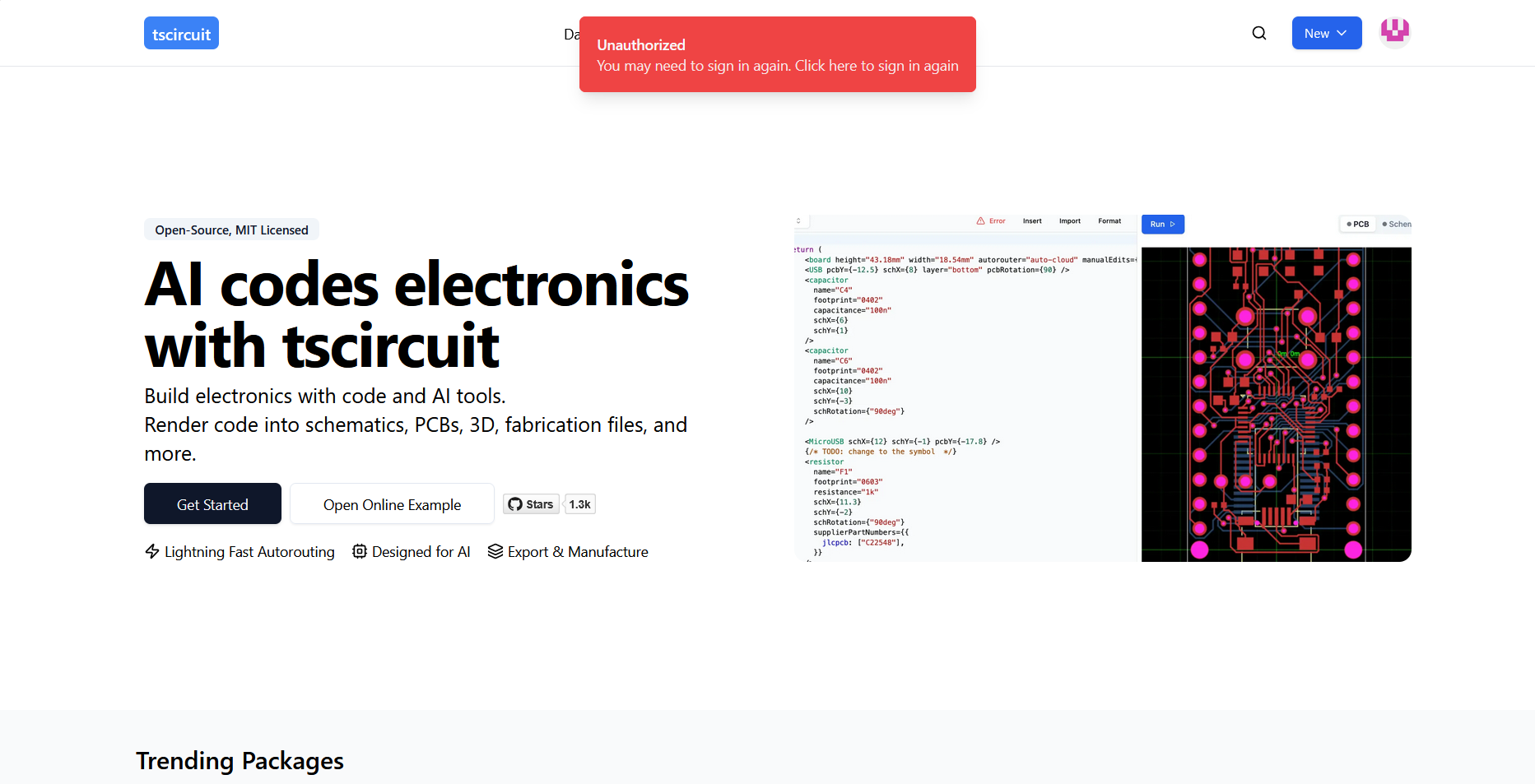
Commandar Rick - Hey @shibo , I tried working o...
Hey @shibo , I tried working on issue #1933 and was able to reproduce it on production tscircuit.com by manually invalidating the session token. The bug reproduced perfectly - the UI still showed me as logged in (profile picture visible) but all API calls failed with 401 errors and multiple toast notifications about being unauthenticated.