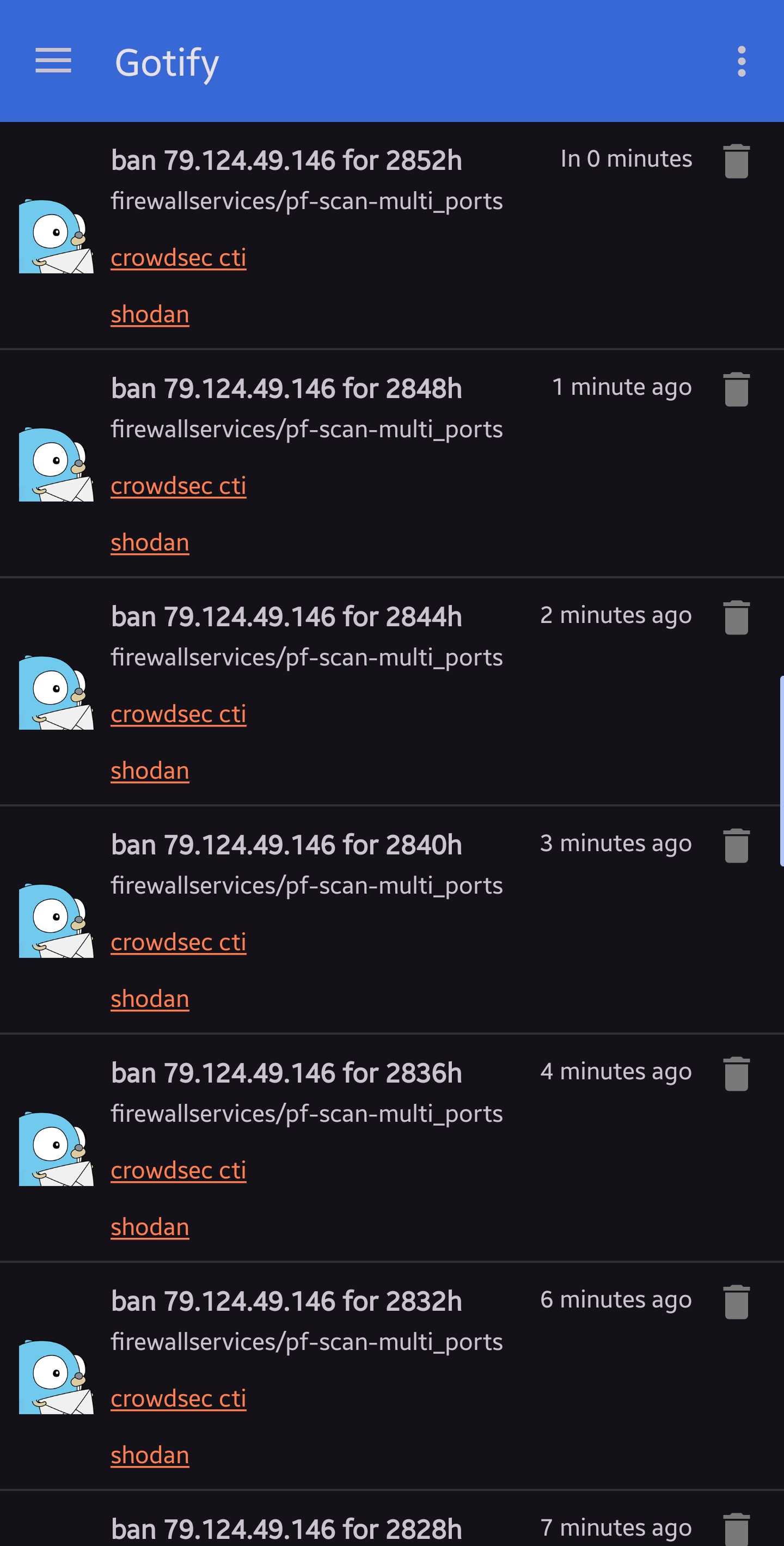
What to do in this scenario..?
I run Crowdsec inside OPNsense in my homelab and it's been working great as far as I can tell, with occasional frequent bursts of bans on several IPs over the last few months.
This week I'm travelling to Dubai and am experiencing multiple bans occurring almost every minute from 79.124.49.146 which is worrying me.
How to i find out what is triggering this..? I have a few honelab services I use like Immich and Dawarich which "phone home" via cloudflare tunnels from my phone/laptop and also run Tailscale... could it be them..?
It's a fair amount of notifications I'm logging via Gotify and best case is just annoying, worst case some bad actor doing constant port scans... any ideas guys..?
This week I'm travelling to Dubai and am experiencing multiple bans occurring almost every minute from 79.124.49.146 which is worrying me.
How to i find out what is triggering this..? I have a few honelab services I use like Immich and Dawarich which "phone home" via cloudflare tunnels from my phone/laptop and also run Tailscale... could it be them..?
It's a fair amount of notifications I'm logging via Gotify and best case is just annoying, worst case some bad actor doing constant port scans... any ideas guys..?