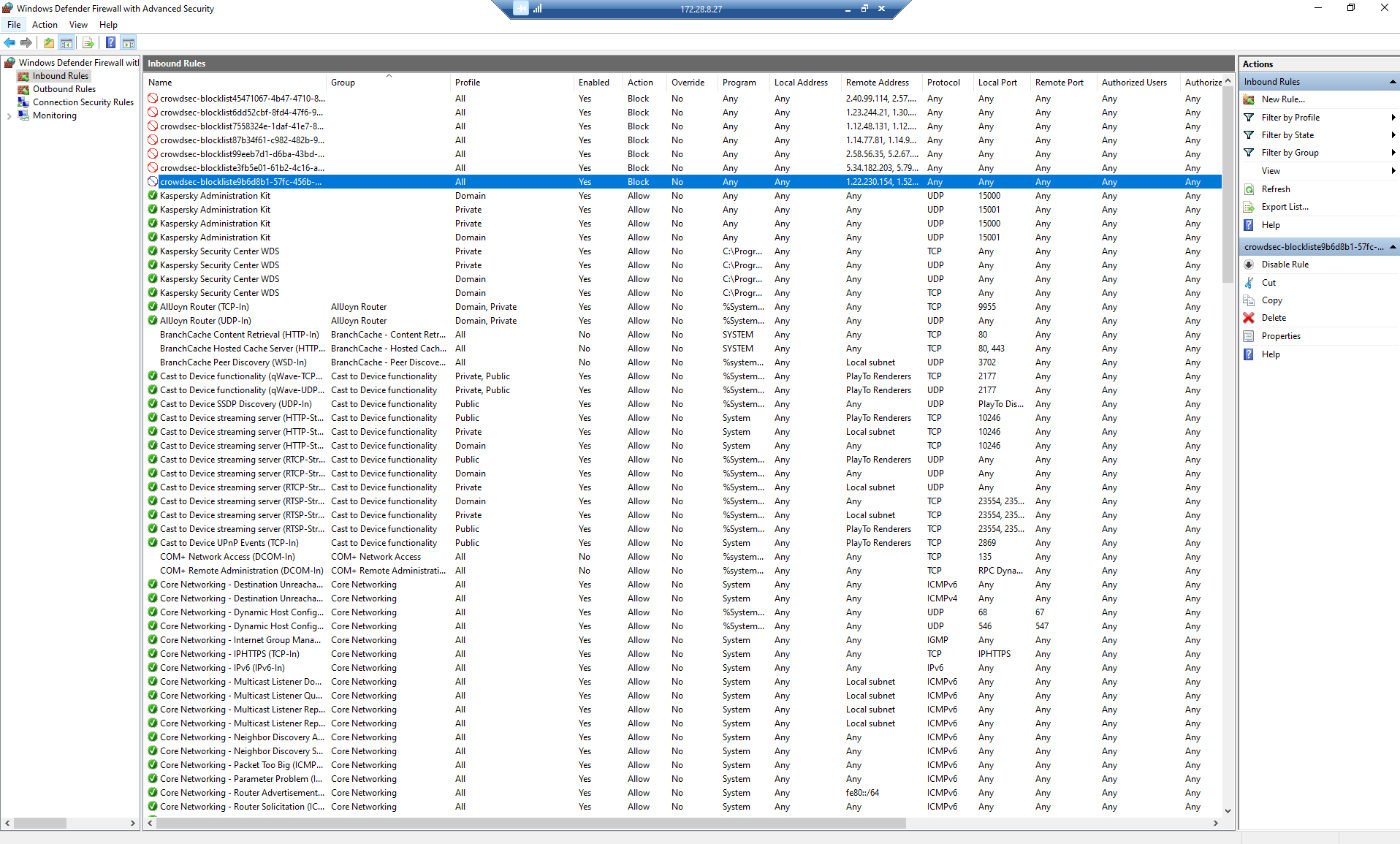
Window Block Decision Activated but Not Working
I am currently testing CrowdSec’s capabilities and have noticed that the blocking mechanism does not seem to be functioning as expected.
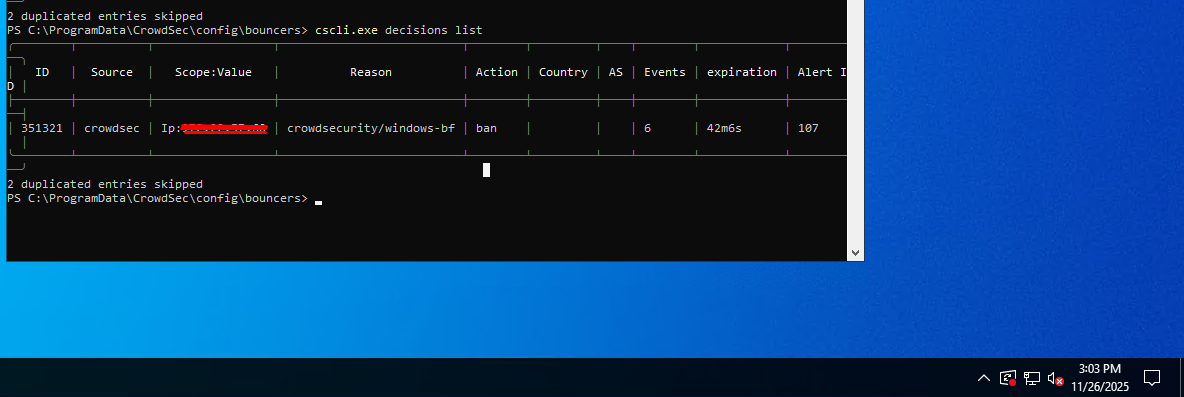
Specifically, I attempted a brute-force attack on a Windows target. After running cscli.exe decisions list, the bouncer should have successfully banned the source IP. However, we are still able to initiate RDP sessions from the source to the Windows Server.
Has anyone encountered this issue before? What steps can we take to diagnose and resolve it?
Thank you for your support.
8 Replies
Important Information
Thank you for getting in touch with your support request. To expedite a swift resolution, could you kindly provide the following information? Rest assured, we will respond promptly, and we greatly appreciate your patience. While you wait, please check the links below to see if this issue has been previously addressed. If you have managed to resolve it, please use run the command
/resolve or press the green resolve button below.Log Files
If you possess any log files that you believe could be beneficial, please include them at this time. By default, CrowdSec logs to /var/log/, where you will discover a corresponding log file for each component.
Guide Followed (CrowdSec Official)
If you have diligently followed one of our guides and hit a roadblock, please share the guide with us. This will help us assess if any adjustments are necessary to assist you further.
Screenshots
Please forward any screenshots depicting errors you encounter. Your visuals will provide us with a clear view of the issues you are facing.
© Created By WhyAydan for CrowdSec ❤️
The decision list show that the IP has been blocked
Is there any additional information or item we may check? Thank you
So you have the windows firewall bouncer installed, and you configure all the zones that are appropriate such as public?
Windows Firewall | CrowdSec
📚 Documentation
Yes, that is correct, I believe the bouncer has been well-configured, the only issue now is it fail to block a source host which performed Brute Force
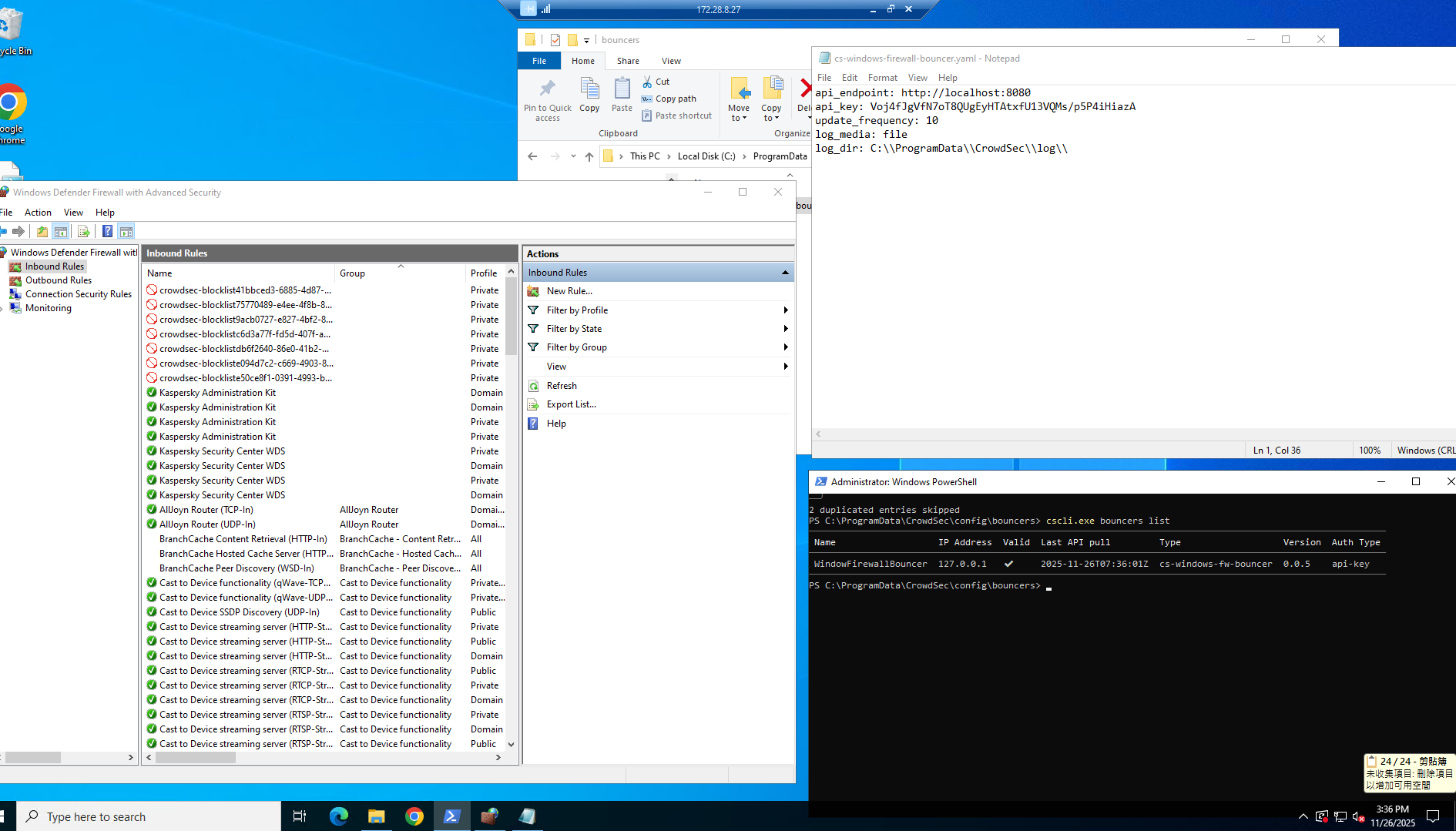
So the rules are only made for the "private" profile
if you accept incomign request from the WAN, it would be public profile profile afaik
but this depends on what profile you assigned to the wan interface
Thanks alot. The displayed Blocked IP should be from the subscribed blocklist from CrowdSec Community, while we would like to check how to block an internal IP (Which we tested to perform Brute Force) and based on the "cscli.exe decisions list" command, it should be activating. Thank you