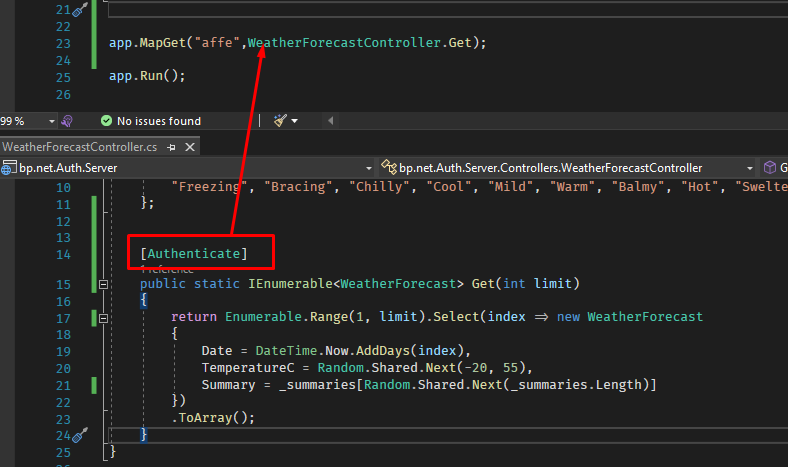
Minimal Api Attributes
The testcode in my screenshot doesnt call the IAuthorizationFilter implementing attribute on my method head. when i use a inline delegate in programm.cs i loose DI(afaik).
i am sure there is a correct way, but for minimal apis i cant find it. Some tipps?
ps: in a controller api all works fina as expected.
i am sure there is a correct way, but for minimal apis i cant find it. Some tipps?
ps: in a controller api all works fina as expected.