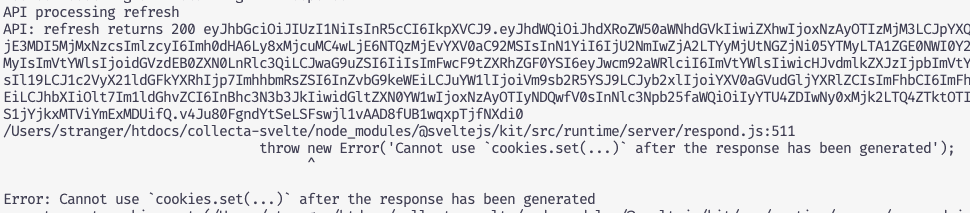
Issuing a JWT via SvelteKit API route throws `Cannot use `cookies.set(...)`...`
Cannot use cookies.set(...) after the response has been generatedIn my SvelteKit (
1.29.1.) I have an API endpoint that's used by the companion Chrome extension.Extension grabs the cookie and sends it as a bearer in a fetch chain:
- first to
/api/refreshthat's checking whether the token is still valid, resigns it if it's outdated, and returns it; - then
/api/uploadusing the returned token attaches it again to the header, along with thebody.
60 while reproducing the bug) (see the screenshot).My
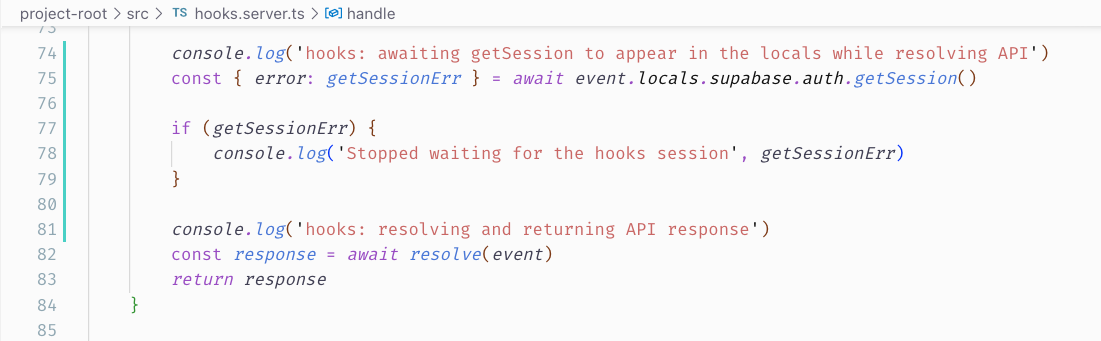
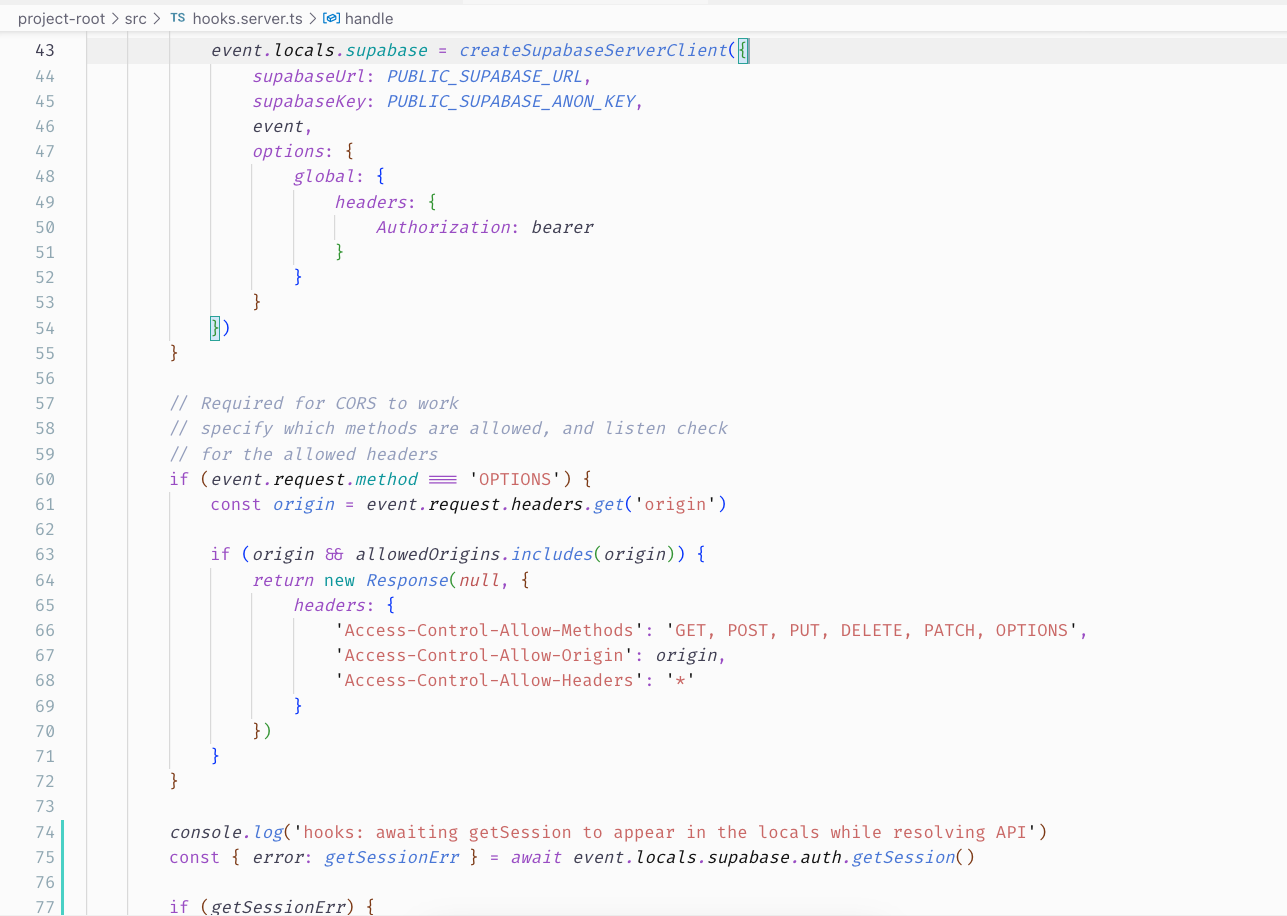
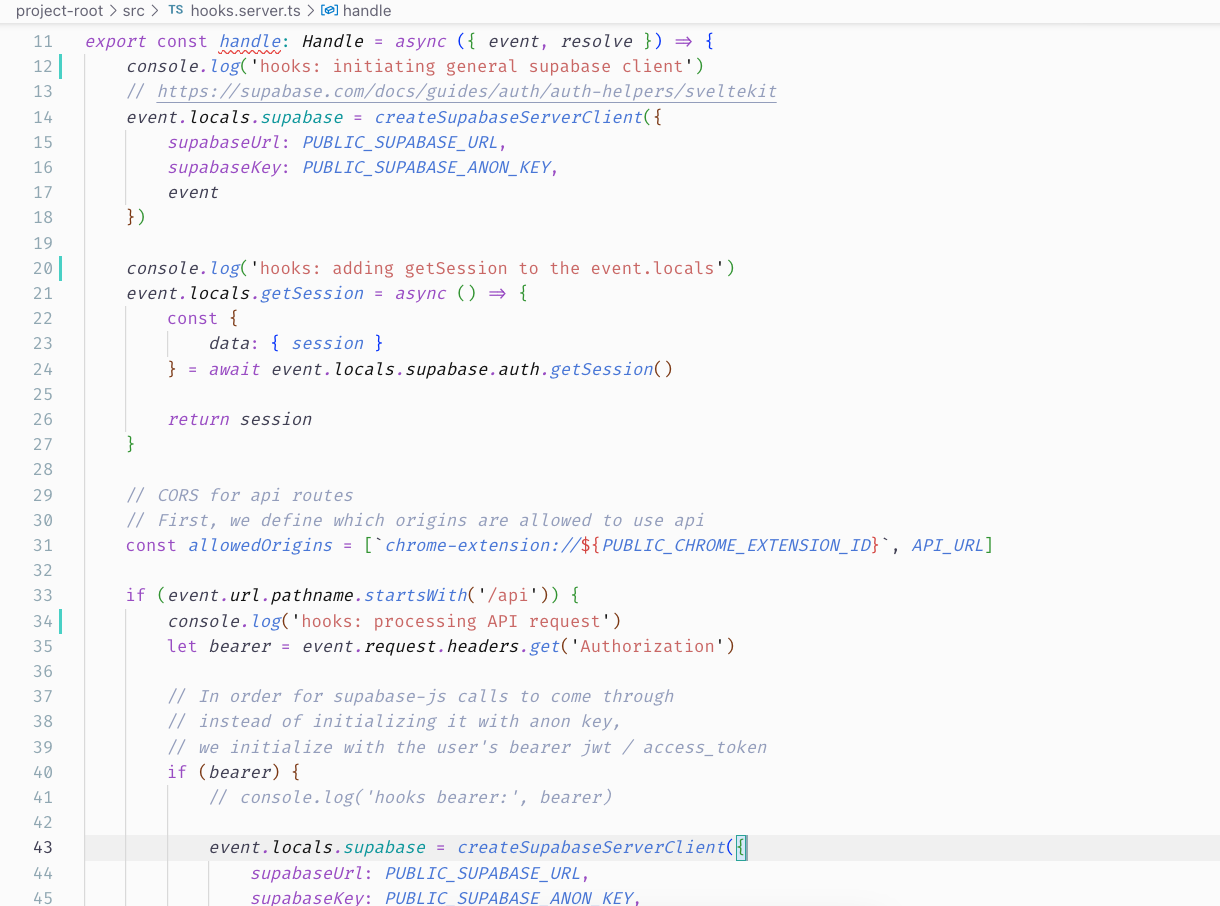
hooks.server.ts implementation is based on the tutorials, minus the api route interception to catch the bearer.I'm clueless. Any advice please? :)