NPMplus won’t connect to api
I have an unraid server with a reverse proxy setup with NPMplus, a fork of NPM with a built in bouncer. I have a custom docker network setup and I’ve generated an api key and put it in the crowdsec.conf file within the app data of npmplus. It’s also worth noting I’m using cloudflare proxy with real ip passthrough setup in nginx. The ports are all right from what I can see and so is the api key. Blocked IPs still connect and the bouncer metrics list never updates. Trying to curl from the npmplus container to the crowdsec container gives me an error 401… I see a similar 401 error in the crowdsec container log coming from the correct ip.
I’m a bit stumped on what to try next
81 Replies
Important Information
Thank you for getting in touch with your support request. To expedite a swift resolution, could you kindly provide the following information? Rest assured, we will respond promptly, and we greatly appreciate your patience. While you wait, please check the links below to see if this issue has been previously addressed. If you have managed to resolve it, please use run the command
/resolve or press the green resolve button below.Log Files
If you possess any log files that you believe could be beneficial, please include them at this time. By default, CrowdSec logs to /var/log/, where you will discover a corresponding log file for each component.
Guide Followed (CrowdSec Official)
If you have diligently followed one of our guides and hit a roadblock, please share the guide with us. This will help us assess if any adjustments are necessary to assist you further.
Screenshots
Please forward any screenshots depicting errors you encounter. Your visuals will provide us with a clear view of the issues you are facing.
© Created By WhyAydan for CrowdSec ❤️
If any logs or config files are needed ping me
I haven’t seen any related to api in either npmplus logs or crowdsec logs. I followed the guide on npmplus git and adapted the paths to support unraid and opted to use a docker network instead of host networking
I changed the ip in the crowdsec.conf file to the static docker i assigned the crowdsec container
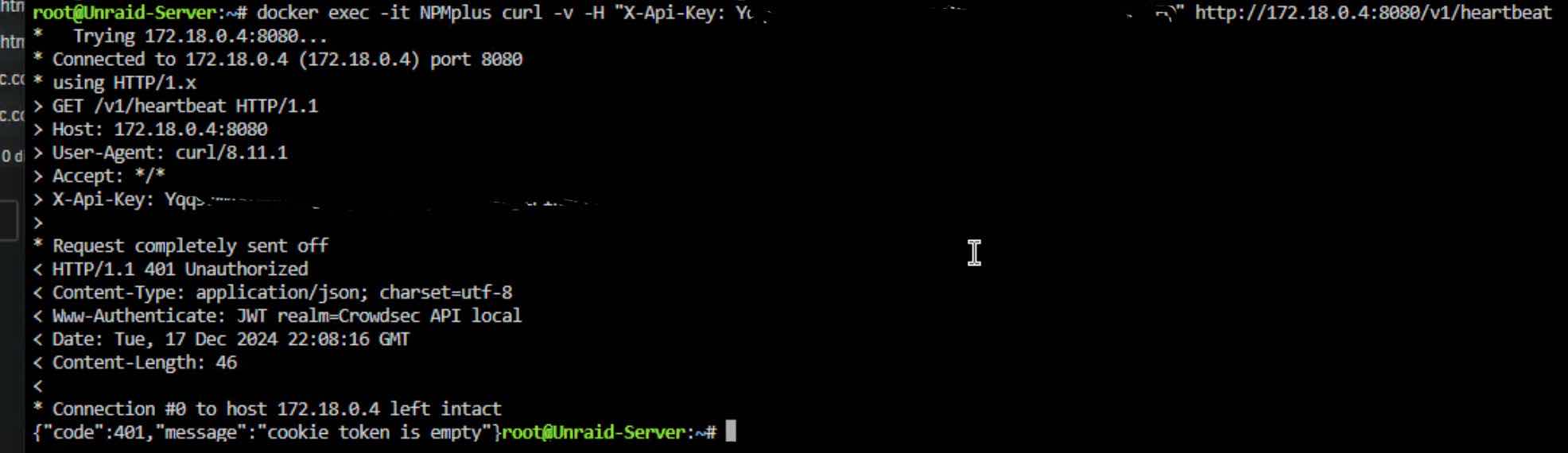
You can see here that the containers can connect to each other. It just doesn’t work for some reason
This means the api key you using is not valid and is returning a 401 response code because of it.
See ive deleted the bouncer multiple times and recreated the api key and it doesn’t make a difference. Ofc i update the api key and reload the npmplus container too
And unless I do a curl I don’t have any logs in CrowdSec that shows NPMPlus even tries to connect to CrowdSec’s api
It does read logs from docker tho
I just realized, the endpoint you are requesting via curl is not allowed for api key
Is there one I can test with?
can you can sending a head request to
/v1/decisions/stream
curl -X HEAD -H "X-Api-Key: 123456" ......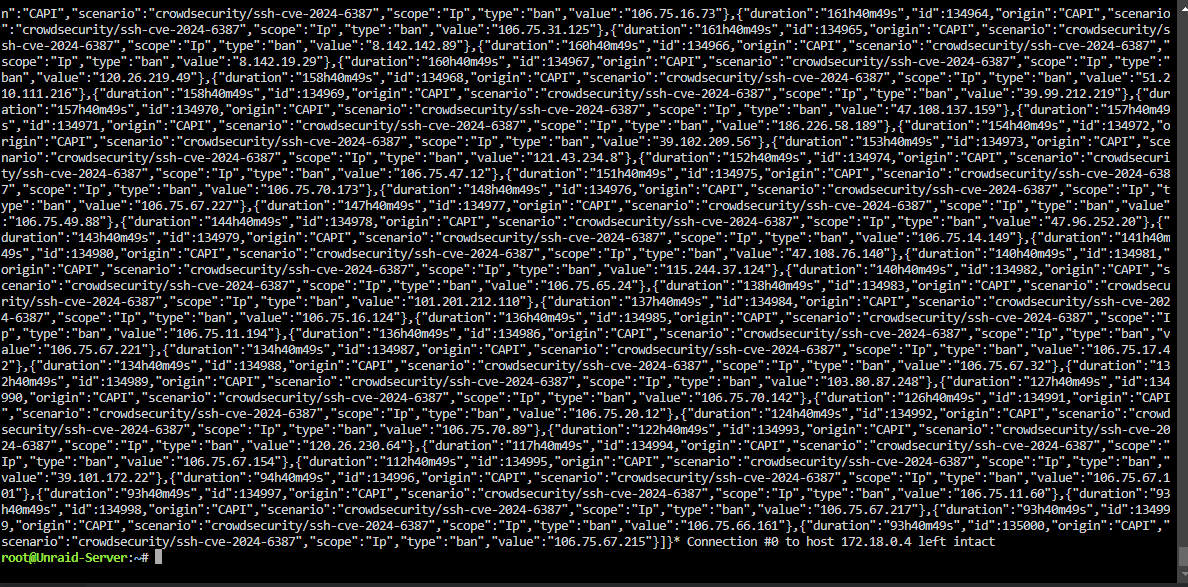
Yeah so that key worked
yup, that works
so, its not a networking related error docker network wise? let me grab my crowdsec.conf in npmplus
crowdsec - config.yaml
everything I see so far, seems right. The only thing to note your
mode is set to live so it only calls the crowdsec LAPI when a request comes into the webservernpmplus.yaml in acquis.d
is stream recommended?
typically we recommend it as it more performant than live (depends on how many RPS your setup gets)
ill set that and see if it makes a difference
it will only start pulling from LAPI once a single requests hits the server so make sure to call one of your sites before checking logs
any request or one with a detection?
no dice
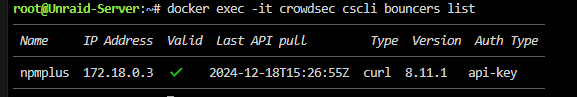
do you have access to npmplus error logs? (nginx error logs)?
cause we log to those files
something i did when troubleshooting was enable ipv6 for the docker network. does that need to be on?
live logs like this?
docker logs -f NPMplusI dont know if npmplus logs all logs to stdout? they might be within the
/opt/npm/nginx/
and within any of those folders is not an
error.log?GitHub
GitHub - ZoeyVid/NPMplus: Docker container for managing Nginx proxy...
Docker container for managing Nginx proxy hosts with a simple, powerful interface - ZoeyVid/NPMplus
I already had
LOGROTATE set to trueso from the configuration I see this https://github.com/ZoeyVid/NPMplus/blob/652fd0b94e29dd3b1449fadef7b5a038186019c7/rootfs/usr/local/nginx/conf/nginx.conf#L4
GitHub
NPMplus/rootfs/usr/local/nginx/conf/nginx.conf at 652fd0b94e29dd3b1...
Docker container for managing Nginx proxy hosts with a simple, powerful interface - ZoeyVid/NPMplus
so it should be going to stderr, however, I dont know if this would be stder of the container
do i need modsecurity enabled for my proxy hosts by chance? im assuming not?
Not that shouldnt have an impact
found this within the container but its useless
its an error.log
yeah the container stdout will be just the proxy manager logs rather than nginx
and this is
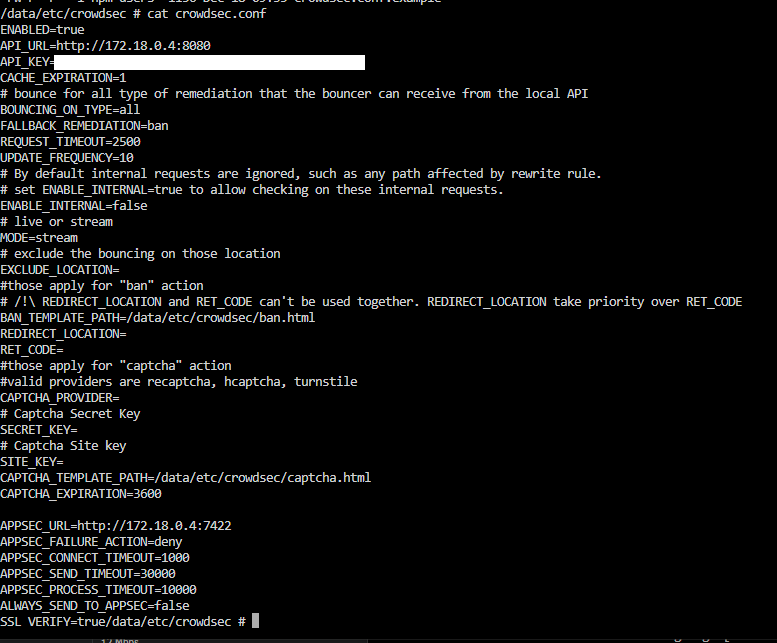
/opt/npm/etc/crowdsec/crowdsec.conf?for me its
/data/etc/crowdsec in the container
but yeabut you are persisting this directory on the host?
the file is the same when i cat it within the container console as on the host
Okay and since doing this did you destroy and recreate the container so it loads everything again?
like delete it and rerun my docker template (basically compose file)?
Yeah as typically you have to redeploy after changes as per npmplus instructions
just did that and no dice
i dont see anything in the crowdsec logs about connections from
172.18.0.3 which is the npmplus containerits reading the logs tho?
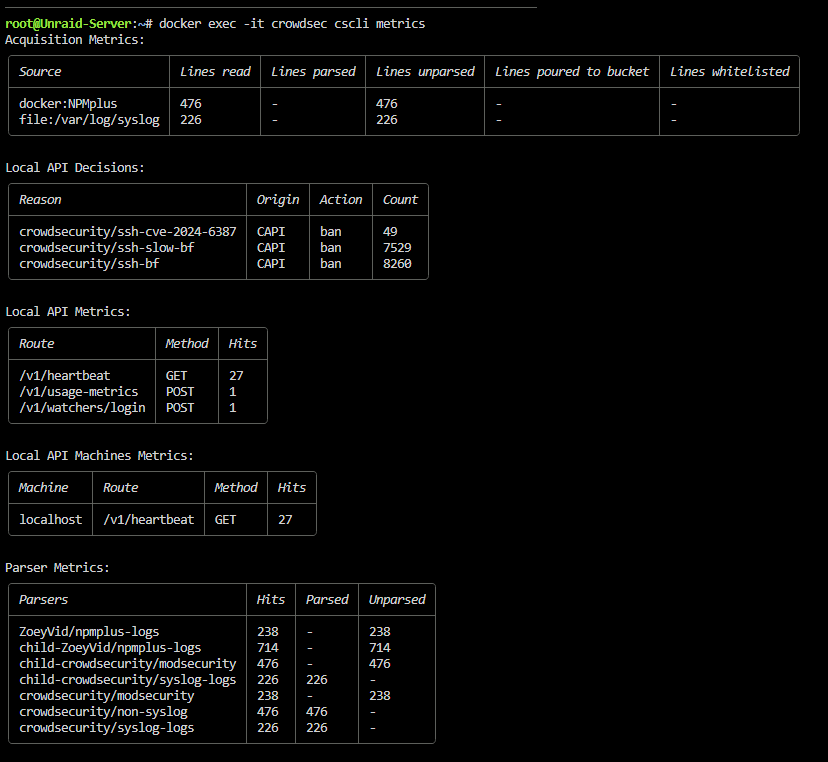
I can dm you the crowdsec logs if needed
I did read a couple discussions about this on the git https://github.com/ZoeyVid/NPMplus/discussions/691
https://github.com/ZoeyVid/NPMplus/discussions/961#discussioncomment-10113769
GitHub
Why network_mode: host? · ZoeyVid NPMplus · Discussion #691
Can you elaborate on why you say "this fork has a dependency on network_mode: host" and similar in the readme? I'd like to avoid using network_mode: host for security and maintainabil...
GitHub
crowdsec config · ZoeyVid NPMplus · Discussion #961
Hello, i've setup npmplus and crowdsec according to the docs, ... i think im not sure its OK, changing mode from bridge to host doesnt seem to have an effect, so i'm not quite sure its effi...
i already did the ip changes and enabled ipv6 as they recommended before i came here
ok, what the fuck
i think i got it solved, or at least made some progress
it seems if you use the unraid web ui text editor it encodes the npmplus crowdsec.conf incorrectly. after editing it in vim within the container i saw that it was adding
^M at the end of each line... deleting those and restarting the containers has it communicating with the api
now i gotta see if its blocking properly
it seems to work now api wise. I want to leave this open for a bit while i try to get extra parsers setup
@iiamloz I got it working with the jellyfin collection and it successfully blocks ips. How can i test that it will block ips based on nginx docker integration/ logs? i tried doing some curl commands but it didnt pick up on it
I just got 404 errors in the console
is there any reason to have ipv6 enabled?You can check
cscli metrics and if it seems to be parsing and you see buckets stats then this is okay, if you see nothing then there probably an issue,.@iiamloz
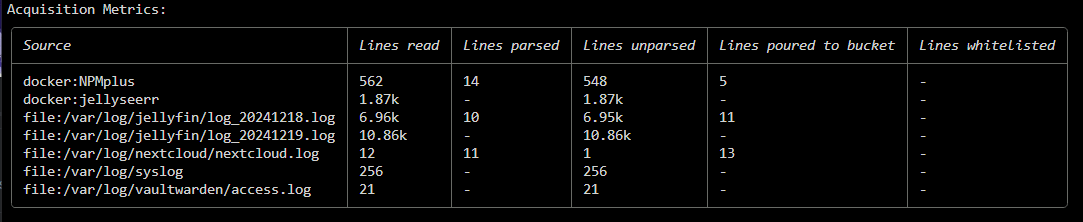
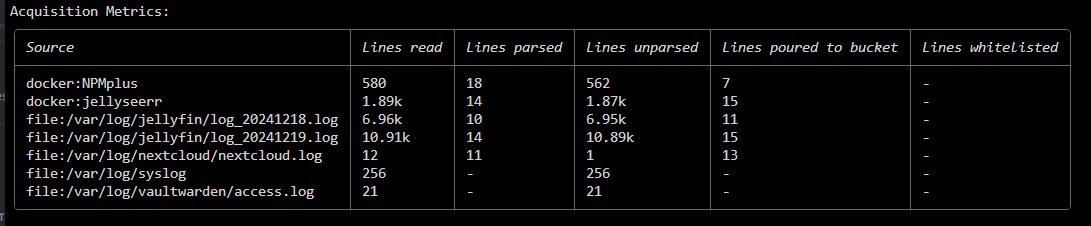
I am completely stuck getting it to parse nginx access.log. It works perfectly when using the explain command but fails to even show the log file in the Source sections of metrics
Did you mount the log files to the crowdsec container?
i did and im able to view them from within the crowdsec container
the strangest thing to me is when using the explain command it seems to detect the test traffic?
cscli explain --file /var/log/npmplus/access.log --type npmplus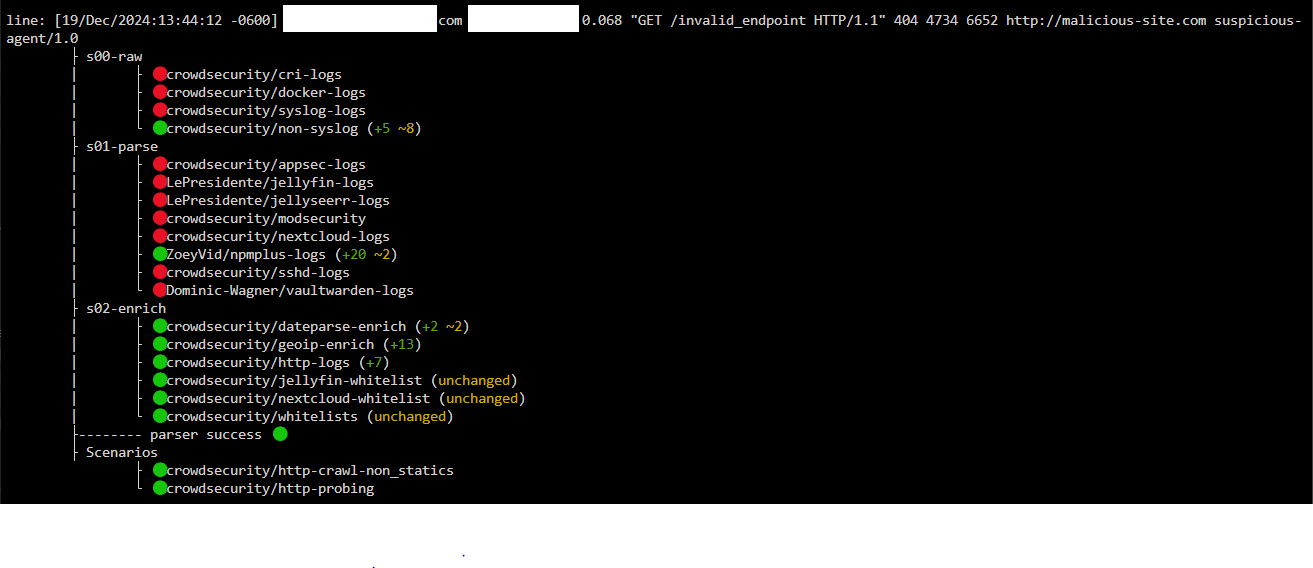
but when i run metrics
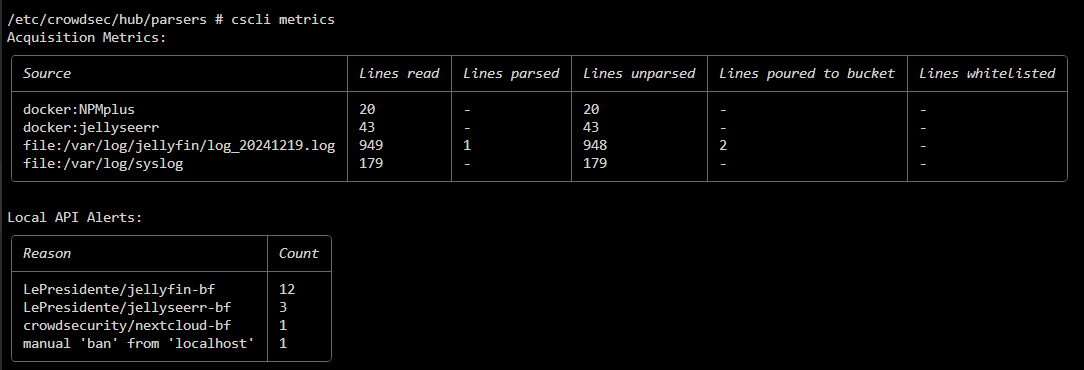
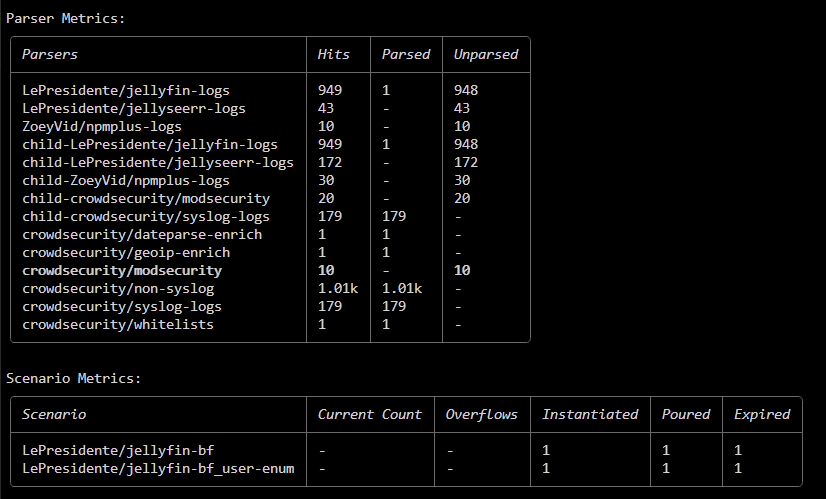
i was reading some posts on git where you were helping people with a similar issue but im not sure that advice applied to my situation
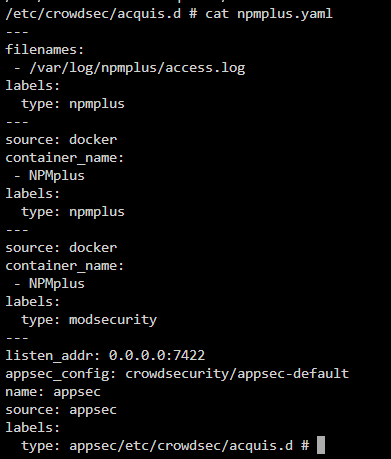
the strangest thing to me is it says its loaded
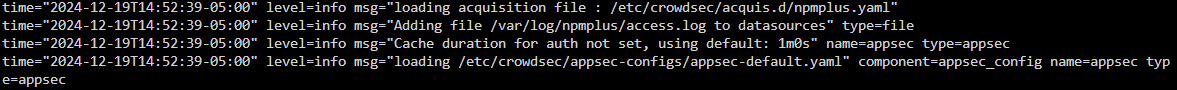
ive tried this with and without the header
---
any other files that would be helpful to see? @iiamlozHmmm, if you
cat the file does it have entries that are added since crowdsec was running?the file updates live with a
tail -f access.log from within the crowdsec containerOkay within your
acquis.yaml file, where you defined filesnames can you add this key to yaml
https://docs.crowdsec.net/docs/next/log_processor/data_sources/file#poll_without_inotify
as exampleFile(s) | CrowdSec
This module allows the Security Engine to acquire logs from text files (in one-shot and streaming mode), and GZ files in one-shot mode.
I think that might have fixed it!
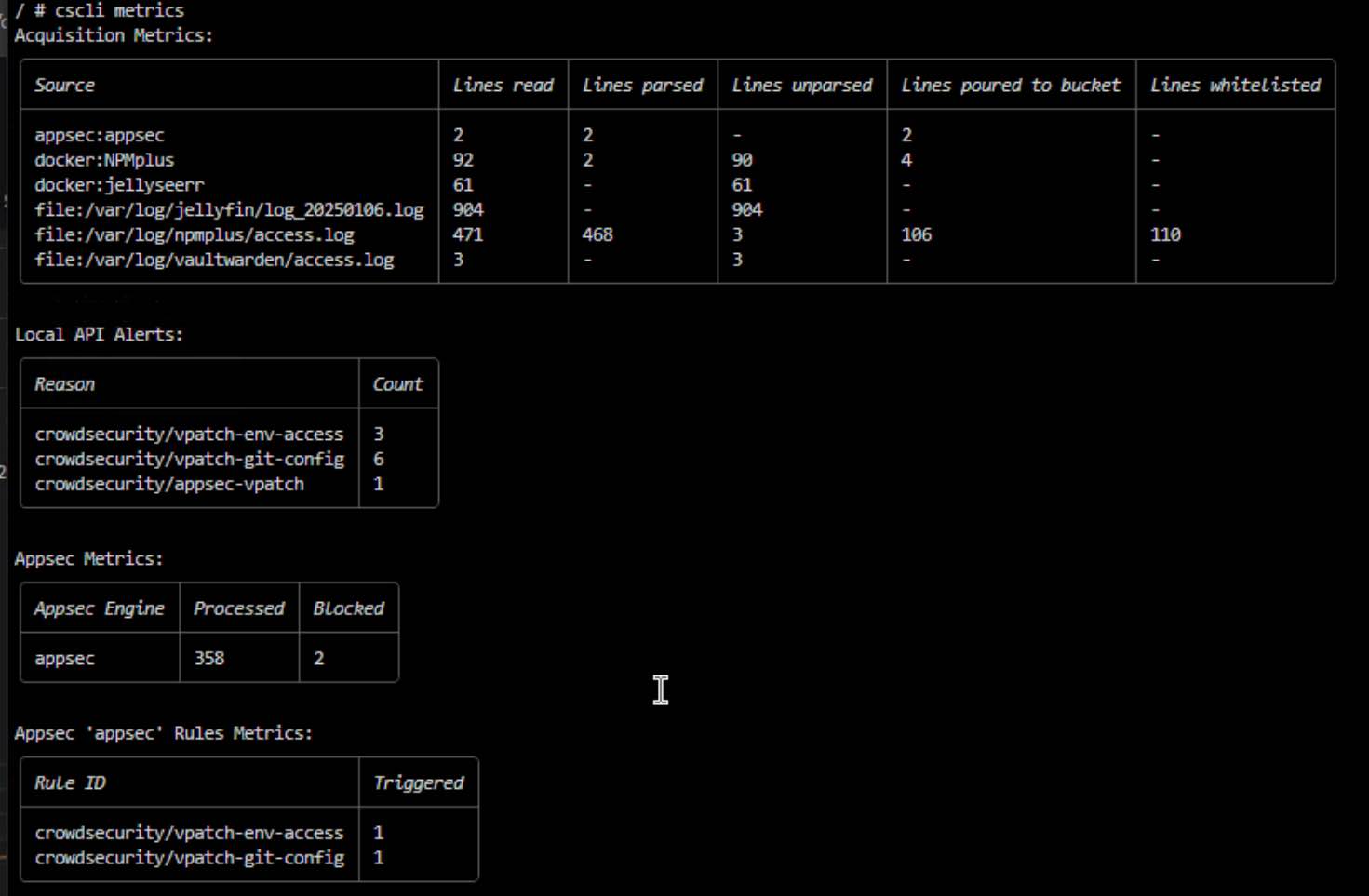
Running this triggered an appsec ban so I’d assume that used nginx logs?
for endpoint in admin login.php wp-login.php .env .git/config; do
curl -s "https://subdomain.domain.com/$endpoint" > /dev/null &
done
wait
@iiamloz
this would of most likely triggered a normal ban, cause of
.git/config and .env and then this would of triggered appsec scenario since it trigger 2 distinct appsec rulesWhat would be a good way to try and trigger a ban based off the nginx logs then? The line you told me to add definitely made a difference because before it wouldn’t show that file at all under source
It is also parsing
Thanks
should trigger at least http probing
however, make sure to run this on a machine you dont mind getting ban decisions
I’m doing it over vpn on another machine offsite. Not worried about that
The top is what triggered from that script
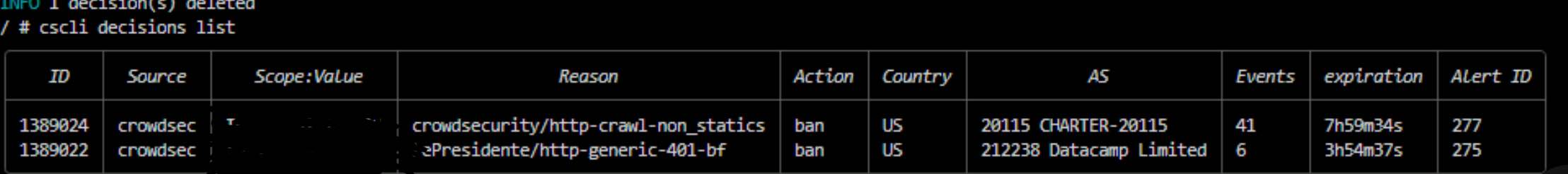
I’m assuming it’s all working now. Thanks a lot man!
Yep that worked!
It took a lot of figuring out but I’m glad I finally got it lol
well at least your name is true 💪 😄
@iiamloz How can I setup discord notifications for CAPI sourced denials/blocks? I have it working for bans based on sources (logs and dockers). I was watching the logs for npmplus (ngnix proxy manager) and saw an ip was blocked that i didnt get a notification for (first screenshot). after looking into it a bit, it was sourced from the CAPI and only shows up in decisions with the command above. running just
cscli decisions list doesnt show it