Tracking nginx host not being banned
I’m trying too figure out why host 62 isn’t banning from failed login attempts this host does not fall under my Authentik. Here is the acquisition metrics
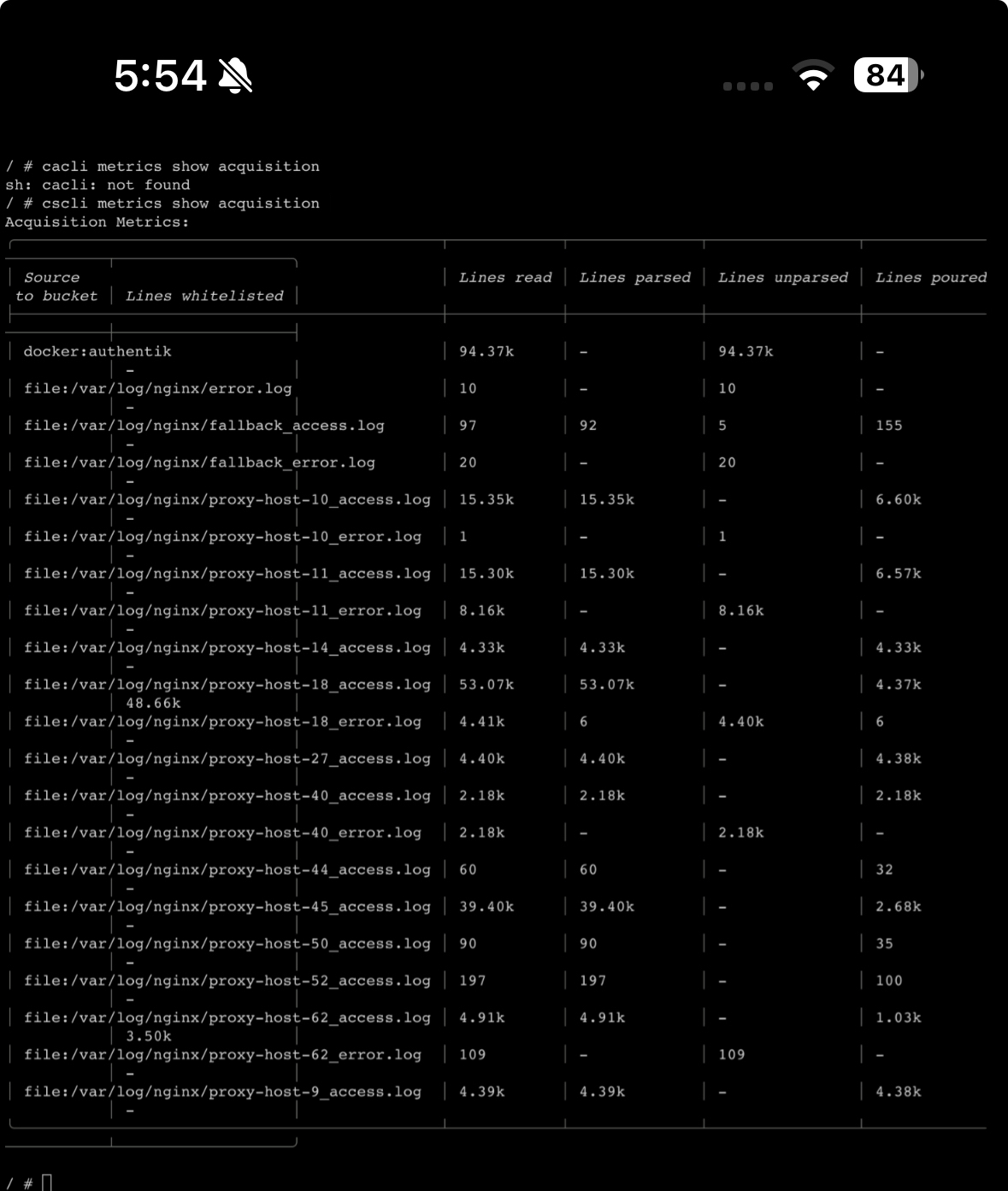
29 Replies
Important Information
This post has been marked as resolved. If this is a mistake please press the red button below or type
/unresolve© Created By WhyAydan for CrowdSec ❤️
So when you mean failing to login, which application is host 62 proxying too?
So I’m saying when I access the domain “host 62” and put a bogus password multiple times it never bans me.
It’s proxying too stash
Witch isn’t under Authentik, when under Authentik the ban works
and if you
grep "login" from that proxy host you see the 401 status returned? cause at the moment we dont detect basic auth failures from a downstream applicationAhh so I’d need to wait until someone makes a parser for that application
well does it log the failed authentication if so yeah we can make one
I’m not sure how to use Grep. Can this be done on unraid? Would it be grep login ip:port?
I do see
ERRO[2025-02-04 05:40:58] Error logging in: invalid credentials in the applications logs itselfbut as far as I can see there no IP and there an open issue for them to add it
You can just write you own custom scenario instead
Can you help with this? And no I don’t see the ip listed in the logs during the failures
Yeah source so I suggest to do something like
You have to check the proxy logs if its 401 or 403
then you need to add this scenario to a file under
/etc/crowdsec/scenarios/ it has to be named .yaml so stash-bf.yaml for example
if your in a container you need to check if you are persisting the above folder EG /etc/crowdsec most likelyLike so?
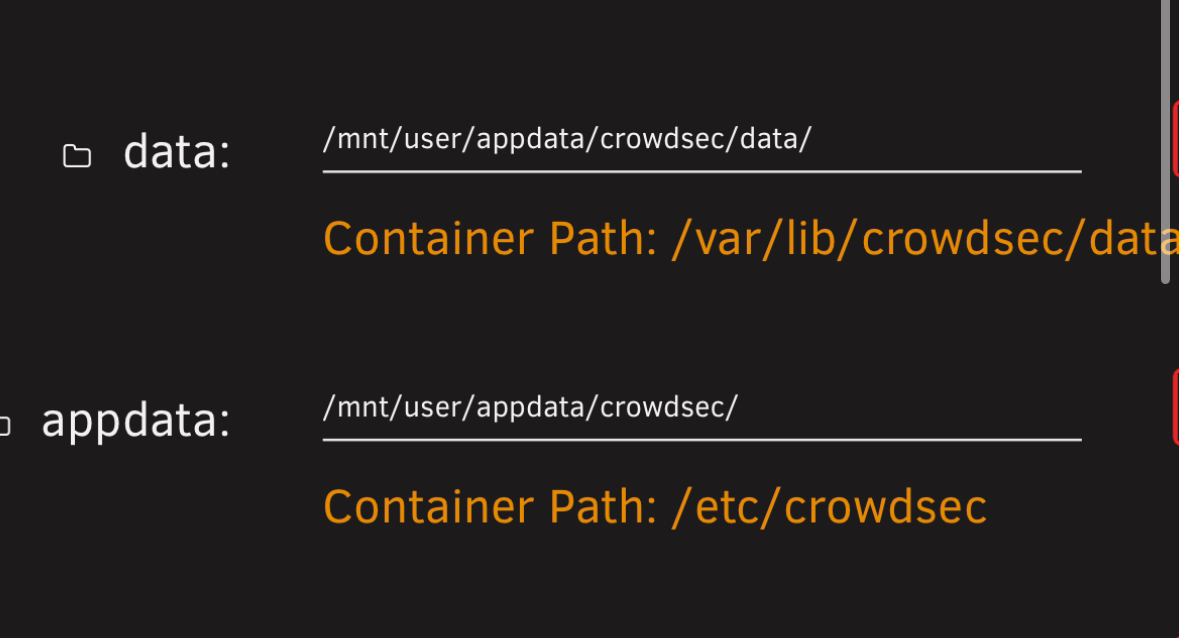
Yeah so within
/mnt/user/appdata/crowdsec/ you will find the sceanarios folder where you need to create the yaml fileAnd it’ll either be 401 or 403. What if it’s showing neither? Or is that not possible
not possible, there has to be a status code
Do I need to put it in its own folder or just add it to the crowdsecsecurity folder?
You add it to
/etc/crowdsec/scenarios
didnt say add it to the hub
for official ones they get symlinked to the hub, for local one you place the file directly into the scenarios folderThat did it 🔥 thank you for all the help. So is it always applicationname-bf.yaml? And the above snippet with the correct name?
it can be whatever you want to call it
as long as its a yaml file
for local files we dont validate the names in anything, so as long as its unique and doesnt clash with any other stuff then your good
What how does the scenario know to target host 62 then? Sorry just trying to pick your brain and learn
I’m an idiot I have to add the stash host.. which would be ip:port or would I put the domain?
Where it says “your stash host here” in the snippet
yeah that how it knows to only target that fqdn
I don’t see a 401 or 403 in the nginx access log for that application
it should be in the error log though?
I see a a few 404 errors from 1/29 but I don’t see anything from the manual failed attempts today?
404 auth request unexpected status
So I’m still trying to figure this out the error log for this host shows no auth errors also the error log isn’t listed under
cscli metrics show acquisitionsDoes this mean I’m SOL for now?
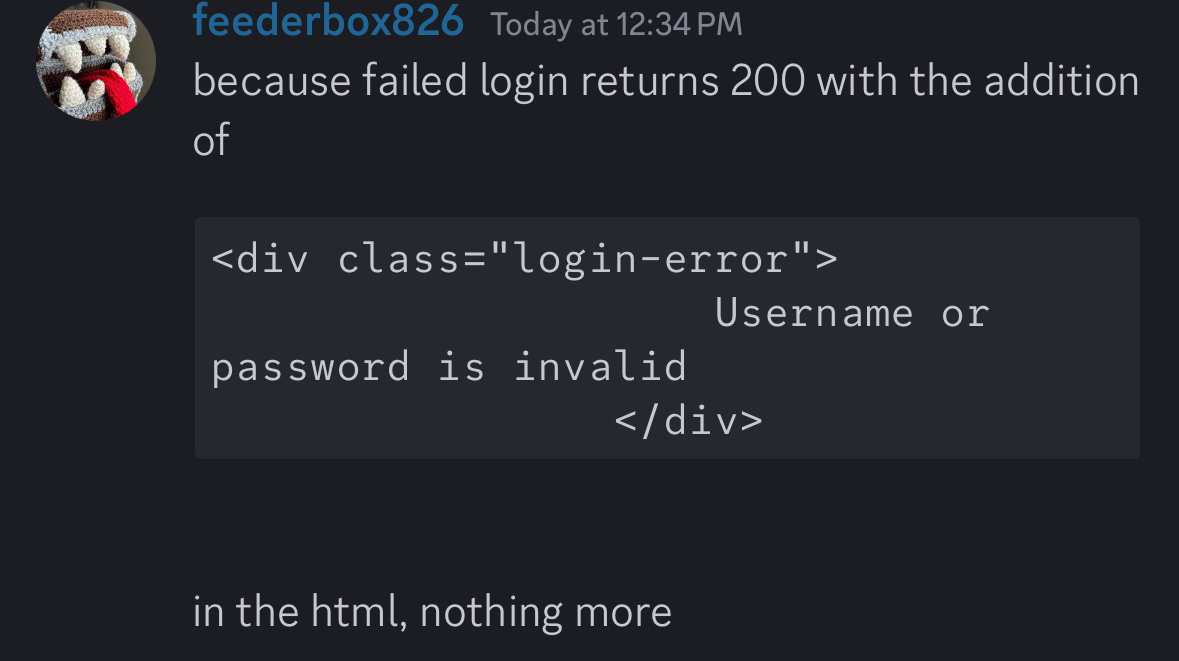
this means you can still detect "bruteforce" but you cant detect if it was a failed login or someone just refreshing the login page multiple times
very odd that they choose 200 status code for a failed login, maybe they should use a different code 😄
Resolving Tracking nginx host not being banned
This has now been resolved. If you think this is a mistake please run
/unresolveWould I need too use code 200? Isn’t code 200 used for successful connections?
Yes exactly, thats why I said you can detect a "bruteforce" but not a failed authentication as they should be returning a 401 code
Yeah that’s definitely not good security practice. Thanks again for the help.