crowdsec-haproxy-bouncer is failing to spot attempted intrusions. Parser failures maybe.
Hello. I installed the crowdsec-haproxy bouncer on OPNSense using both the docs and the blog about it. I did adjust the instructions on the docs to the file locations for freeBSD. It appears operational, sometimes but rarely there are bans appearing. I have set up for turnstile captcha and bans although I think is only triggering bans.
I however see a lot of intrusion attempts on the haproxy logs that seem to NOT have triggered any action from crowdsec. Digging into it as far as I am able to, it appears to me that the included haproxy parser is failing most of the time.
I've done a 'cscli explain --file /var/log/haproxy/latest.log --type haproxy' and please see the examples:
line: <134>1 2025-02-21T19:26:40+00:00 OPNsense.moomooland haproxy 70406 - [meta sequenceId="1071"] 18.97.5.91:33064 [21/Feb/2025:19:26:40.414] 0_SNI_frontend SSL_backend/SSL_server 1/0/90 7 -- 2/2/1/1/0 0/0
├ s00-raw
| ├ 🔴 crowdsecurity/syslog-logs
| └ 🟢 crowdsecurity/non-syslog (+5 ~8)
├ s01-parse
| ├ 🔴 crowdsecurity/haproxy-logs
| ├ 🔴 crowdsecurity/opnsense-gui-logs
| ├ 🔴 firewallservices/pf-logs
| ├ 🔴 firewallservices/pf-logs-drop
| └ 🔴 crowdsecurity/sshd-logs
└-------- parser failure 🔴
More on file attached.
And a successful one also on the file.
Can someone please let me know how can I begin to diagnose appropriately as it feels crowdsec is missing some signals. Luckily for me these are not breaking through.
22 Replies
Important Information
Thank you for getting in touch with your support request. To expedite a swift resolution, could you kindly provide the following information? Rest assured, we will respond promptly, and we greatly appreciate your patience. While you wait, please check the links below to see if this issue has been previously addressed. If you have managed to resolve it, please use run the command
/resolve or press the green resolve button below.Log Files
If you possess any log files that you believe could be beneficial, please include them at this time. By default, CrowdSec logs to /var/log/, where you will discover a corresponding log file for each component.
Guide Followed (CrowdSec Official)
If you have diligently followed one of our guides and hit a roadblock, please share the guide with us. This will help us assess if any adjustments are necessary to assist you further.
Screenshots
Please forward any screenshots depicting errors you encounter. Your visuals will provide us with a clear view of the issues you are facing.
© Created By WhyAydan for CrowdSec ❤️
additionally in an attempt to see if I can diagnose the parser, I followed the docs https://docs.crowdsec.net/docs/next/log_processor/parsers/create to install a testing environment. It failed. ~/applications/crowdsec-v1.6.4/tests/hub$ ../cscli -c ../dev.yaml hubtest run --all
FATA unable to load hubtest: path to crowdsec binary 'crowdsec' doesn't exist or is not in $PATH, can't run
Creating parsers | CrowdSec
Foreword
~/applications/crowdsec-v1.6.4/tests$ ../cscli -c ../dev.yaml hubtest run --all
bash: ../cscli: No such file or directory
~/applications/crowdsec-v1.6.4/tests$ ./cscli -c ./dev.yaml hubtest run --all
FATA unable to load hubtest: failed to load hub index: unable to read index file: open /home/penguin/applications/crowdsec-v1.6.4/tests/.index.json: no such file or directory
I couldn't find a way to tell where the .index.json is explicitly so whether from tests or hub directories, in both cases I can tell it the relative path to cscli and the yaml file no problem, but it is looking for the .index.json in the current directory but then fails with the binary not in the $PATH. Is the documentation correct?
@cookiemonster5680 it seems the logs is
syslog format instead of reading from haproxy log files can you confirm?
However, it seems that log format is not compatible with our haproxy parsers so have you altered the default format in any way?
this is format we expect
so I believe it this part that is failing firstly
as I only see 3 slashes@iiamloz very grateful for you having a look at this. I am using the logging format out of the box from the os-haproxy opnsense plugin. I have not altered that there but I could have made a mistake somewhere else when setting this up, so if that's OK, I'll show you what I have in the various places.
these are the logging settings for ha-proxy. I have removed everything else so it fits
global
log /var/run/log local0 info
defaults
log global
frontend 1_HTTPS_frontend
mode http
option http-keep-alive
option httplog
backend crowdsec
# health checking is DISABLED
mode http
balance source
# stickiness
stick-table type ip size 50k expire 30m
stick on src http-reuse safe server crowdsec 192.168.5.1:8081 backend captcha_verifier # health checking is DISABLED mode http balance source # stickiness stick-table type ip size 50k expire 30m
stick on src http-reuse safe server turnstile_verifier challenges.cloudflare.com:443 Actually that is for the SNI frontend. There are another two frontends in behind it. The SNI is in TCP mode to look at the SNI. It will default to an SSL_backend where the TLS connections are terminated. Then any http requests are redirected to https. So we have external-client -> SNI front-end -> https_frontend -> backend . I had to decide where to place the crowdsec protections in this chain and I have put it in the https one. Therefore I have this there (which is more complete than above - a struggle with character limits here):
stick on src http-reuse safe server crowdsec 192.168.5.1:8081 backend captcha_verifier # health checking is DISABLED mode http balance source # stickiness stick-table type ip size 50k expire 30m
stick on src http-reuse safe server turnstile_verifier challenges.cloudflare.com:443 Actually that is for the SNI frontend. There are another two frontends in behind it. The SNI is in TCP mode to look at the SNI. It will default to an SSL_backend where the TLS connections are terminated. Then any http requests are redirected to https. So we have external-client -> SNI front-end -> https_frontend -> backend . I had to decide where to place the crowdsec protections in this chain and I have put it in the https one. Therefore I have this there (which is more complete than above - a struggle with character limits here):
frontend 1_HTTPS_frontend
http-response set-header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
bind 192.168.5.100:5000 name 192.168.5.100:5000 accept-proxy ssl curves {list of curves} alpn h2,http/1.1 crt-list /tmp/haproxy/ssl/648b26ac6f5421.99835538.certlist
bind 192.168.5.100:443 name 192.168.5.100:443 accept-proxy ssl curves secp384r1 no-sslv3 no-tlsv10 no-tlsv11 no-tls-tickets ciphers {ciphers list } alpn h2,http/1.1 crt-list /tmp/haproxy/ssl/648b26ac6f5421.99835538.certlist
mode http
option http-keep-alive
# logging options
option httplog
# ACTION: PUBLIC_SUBDOMAINS_map-rule
# NOTE: actions with no ACLs/conditions will always match
use_backend %[req.hdr(host),lower,map_dom(/tmp/haproxy/mapfiles/619521e7265391.88020289.txt)]
# WARNING: pass through options below this line
stick-table type ip size 10k expire 30m # declare a stick table to cache captcha verifications
http-request lua.crowdsec_allow # action to identify crowdsec remediation
http-request track-sc0 src if { var(req.remediation) -m str "captcha-allow" } # cache captcha allow decision
http-request redirect location %[var(req.redirect_uri)] if { var(req.remediation) -m str "captcha-allow" } # redirect to initial url
http-request use-service lua.reply_captcha if { var(req.remediation) -m str "captcha" } # serve captcha template if remediation is captcha
http-request use-service lua.reply_ban if { var(req.remediation) -m str "ban" } # serve ban template if remediation is ban
Nothing for logging in profiles.yaml , my /usr/local/etc/crowdsec/acquis.d/haproxy.yaml contains:
filenames:
- /var/log/haproxy/*.log
force_inotify: true
poll_without_inotify: true
labels:
type: haproxy . Could it be possible then that the plugin is not logging as "standard"? I did think of that but then I saw the logging settings in the config, which I haven't altered the logging parts, and compared with haproxy's docs which say their formats are httplog for http and tcplog for tcp, so they looked standard. Have I got that wrong?hmm maybe the issue is more we havent really tested parsing TCP logs only http so maybe thats the difference?
do you have multiple logs for tcp and http frontends?
Hi. Sorry for the delays. Whilst I'm in office hours, from my work computer we can not reach discord. It is a banned site. I'll look shortly
It appears there is a single log by haproxy. I'm happy to share it somehow. In light of this it seems that the way the plugin in OPN uses only one and perhaps puts all tcp and http logs entries in the same file Edit: thinking about it a little. If both tcp and http log entries are in the same file, should the parser not have parsed those, and leaving the tcp ones as unparsed?
any further thoughts @iiamloz ? I also asked about the logging by the plugin. I'm told that it is standard with the way syslog-ng does logging. If you also give me a hand -please- with the question about the setup of a test environment, I hopefully can make more diagnostics on my side.
Setting up a test environment most likely wont replicate it unless you setting up another opnsense box. FYI if you install the crowdsec plugin then you dont need to setup any test environment and can just use the command as normal, the test environment is only if you dont want crowdsec/cscli within your PATH
We need to find the http logs thats all cause we dont parse TCP logs as there is 0 information, so what does
option httplog actually do?Hi. According to the haproxy documentation is similar but more basic. Some fields are different http://docs.haproxy.org/2.8/configuration.html#8.2.2
By the way, the log file seems to include both tcp and http logs. That is to say, the haproxy plugin sends all logs to the same file. For instance, see these entries. TCP on the front end that we seem to know the parser is currently not made to parse it. Then some http that it can parse some entries and others that wit doesn't.
line: <134>1 2025-02-28T15:22:12+00:00 OPNsense.moomooland haproxy 27719 - [meta sequenceId="2944"] 142.93.113.156:53402 [28/Feb/2025:15:22:12.752] 1_HTTPS_frontend/192.168.5.100:443: SSL handshake failure (error:0A0000C1:SSL routines::no shared cipher)
├ s00-raw
| ├ 🔴 crowdsecurity/syslog-logs
| └ 🟢 crowdsecurity/non-syslog (+5 ~8)
├ s01-parse
| ├ 🔴 crowdsecurity/haproxy-logs
| ├ 🔴 crowdsecurity/opnsense-gui-logs
| ├ 🔴 firewallservices/pf-logs
| ├ 🔴 firewallservices/pf-logs-drop
| └ 🔴 crowdsecurity/sshd-logs
└-------- parser failure 🔴
line: <134>1 2025-02-28T05:23:19+00:00 OPNsense.moomooland haproxy 27719 - [meta sequenceId="1547"] 91.196.152.25:53745 [28/Feb/2025:05:23:09.589] 0_SNI_frontend SSL_backend/SSL_server 1/0/9823 3078 -- 1/1/0/0/0 0/0
├ s00-raw
| ├ 🔴 crowdsecurity/syslog-logs
| └ 🟢 crowdsecurity/non-syslog (+5 ~8)
├ s01-parse
| ├ 🔴 crowdsecurity/haproxy-logs
| ├ 🔴 crowdsecurity/opnsense-gui-logs
| ├ 🔴 firewallservices/pf-logs
| ├ 🔴 firewallservices/pf-logs-drop
| └ 🔴 crowdsecurity/sshd-logs
└-------- parser failure 🔴
line: <134>1 2025-02-28T02:07:51+00:00 OPNsense.moomooland haproxy 27719 - [meta sequenceId="418"] 185.242.226.166:33283 [28/Feb/2025:02:07:51.623] 1_HTTPS_frontend/192.168.5.100:443: SSL handshake failure (error:0A0000C1:SSL routines::no shared cipher)
├ s00-raw
| ├ 🔴 crowdsecurity/syslog-logs
| └ 🟢 crowdsecurity/non-syslog (+5 ~8)
├ s01-parse
| ├ 🔴 crowdsecurity/haproxy-logs
| ├ 🔴 crowdsecurity/opnsense-gui-logs
| ├ 🔴 firewallservices/pf-logs
| ├ 🔴 firewallservices/pf-logs-drop
| └ 🔴 crowdsecurity/sshd-logs
└-------- parser failure 🔴
line: <134>1 2025-02-28T09:38:28+00:00 OPNsense.moomooland haproxy 27719 - [meta sequenceId="899"] 143.198.121.184:48476 [28/Feb/2025:09:38:26.925] 1_HTTPS_frontend~ 1_HTTPS_frontend/<NOSRV> -1/-1/-1/-1/1110 400 0 - - CR-- 2/1/0/0/0 0/0 "<BADREQ>"
├ s00-raw
| ├ 🔴 crowdsecurity/syslog-logs
| └ 🟢 crowdsecurity/non-syslog (+5 ~8)
├ s01-parse
| ├ 🟢 crowdsecurity/haproxy-logs (+44 ~2)
| ├ 🔴 crowdsecurity/opnsense-gui-logs
| ├ 🔴 firewallservices/pf-logs
| ├ 🔴 firewallservices/pf-logs-drop
| └ 🔴 crowdsecurity/sshd-logs
├ s02-enrich
| ├ 🟢 crowdsecurity/dateparse-enrich (+2 ~2)
| ├ 🟢 crowdsecurity/geoip-enrich (+13)
| ├ 🔴 crowdsecurity/http-logs
| └ 🟢 crowdsecurity/whitelists (+2)
├-------- parser success 🟢
├ Scenarios
└ 🟢 crowdsecurity/http-probingssl handshake errors are not parsed cause there nothing we could we do with the information? and the ones that do get http sent as you can see from the last explain it does parse.
I thought you'd be interested in these signals? I certainly am, as I want to block them with a temp ban or a captcha. So, do you see it as crowdsec is doing all it can do?
Yeah we will be able to see things via the http frontend it just depends on how much traffic you are getting g
but you don't, that's what I've been trying to explain.
Ok you know what, fine. You're not interested.
Okay for the ssl handshake we have to update the parser as it currently doesnt parse them, ill open an issue on github
GitHub
[HAProxy] SSL handshake fail to parse · Issue #1262 · crowdsecurity...
Currently the HAProxy parser only parses successful proxied requests, however, a user may also want to create a custom scenario if SSL handshake fails 192.168.1.1:33283 [28/Feb/2025:02:07:51.623] 1...
So that is what I should have done! Thank you sir. Much obliged
Hi the spam is real XD
Don't see the point trying to help you setup a dev environment in a github issue
but by the look at what you posted, you didn't checkout the hub in the setup local dev configuration
you need to run
cscli hubtest run haproxy-logs in the hub folder itself
@cookiemonster5680
I have the above working my end if you want me to create a PR, but you did want to learn so held off on that@Lepresidente Hi. I am sorry for the spam.
- I started this engagement on the 21st of Feb. As you can see from the coming and going it eventually Loz seems to have been persuaded to have it looked at and logged it himself in git hub 3 weeks ago on the 6th of March.
- A week later on the 16th of March I asked for the help with the hub so I could try myself.
- I then due to no action there asked and pinged you on and two others on the 25th of March.
- Then asked again on the 28th of March. So yes it was too close 3 days apart. That can be spamming but the thread has been there since the 6th of March. Other issues haven been started later and have had more attention so mine felt ignored.
>If asking for help without response for 6 weeks is spamming, I apologise.
For clarity there are two items here:
- The actual issue with the haproxy parser
- My problem setting up the development environment to try and test the parser. I'd also like to ask for a hand with this, even if is for expanding my understanding of crowdsec.
I have written more but I am limited here with the message length, I'll try multiple but this medium is just not suitable IMHO.
Following the documentation:
penguin@saturn:~/applications/crowdsec-v1.6.4/tests$ ./crowdsec -c dev.yaml
WARN[2025-03-30T00:19:40Z] can't load CAPI credentials from './config/online_api_credentials.yaml' (missing login field)
INFO[2025-03-30T00:19:40Z] push and pull to Central API disabled
INFO[2025-03-30T00:19:40Z] Enabled feature flags: <none>
Good so far, I then cloned the hub, cd to hub and with
INFO[2025-03-30T00:19:40Z] Enabled feature flags: <none>
Good so far, I then cloned the hub, cd to hub and with
../cscli -c ../dev.yaml hubtest run --all
I get:
penguin@saturn:~/applications/crowdsec-v1.6.4/tests/hub$ ../cscli -c ../dev.yaml hubtest run --all
FATA unable to load hubtest: path to crowdsec binary 'crowdsec' doesn't exist or is not in $PATH, can't run
So I am stuck despite -I think- following the documentation.
I am familiar with the *nix filesystems and can not understand why the utility can be called from /path/to/tests/.cscli but calling it from the directory below I can't, when calling it with the appropriate relative path i.e. /path/to/tests/hub/..cscli
But look at this:
penguin@saturn:~/applications/crowdsec-v1.6.4/tests/hub$ ../cscli
cscli is the main command to interact with your crowdsec service, scenarios & db.
I can call it fine. As soon as I try with/from the hub, it can't:
penguin@saturn:~/applications/crowdsec-v1.6.4/tests/hub$ ../cscli -c ../dev.yaml hubtest run --all
FATA unable to load hubtest: path to crowdsec binary 'crowdsec' doesn't exist or is not in $PATH, can't run
And the referenced files (dev.yaml) is present:
penguin@saturn:~/applications/crowdsec-v1.6.4/tests/hub$ ls -alh ..
total 104M
drwxrwxr-x 7 penguin penguin 4.0K Feb 22 22:39 .
drwxr-xr-x 5 penguin penguin 4.0K Feb 22 22:35 ..
drwxrwxr-x 11 penguin penguin 4.0K Feb 22 22:35 config
-rwxr-xr-x 1 penguin penguin 52M Feb 22 22:35 crowdsec
-rwxr-xr-x 1 penguin penguin 52M Feb 22 22:35 cscli
drwxrwxr-x 3 penguin penguin 4.0K Feb 22 22:37 data
-rw-rw-r-- 1 penguin penguin 1.2K Feb 22 22:35 dev.yaml
drwxrwxr-x 21 penguin penguin 4.0K Feb 22 22:45 hub
drwxrwxr-x 2 penguin penguin 4.0K Feb 22 22:35 logs
drwxrwxr-x 2 penguin penguin 4.0K Feb 22 22:35 plugins
Are you able to spot my problem with the dev setup?
And, yes please to the PR. Is that to provide a "fix" for the parser?
I'm grateful.
p.s. -- hard to follow this here. I've copied it to github and made it more readable. Unable here.Ok i don't use the above method, I just installed crowdsec on a Linux vm following the normal install procedure and then checked out the hub, then ran the above commands to hubtest ill do the pr today
it is the documented method i.e. what is the only available normal install procedure available. ! Thanks for the PR.
Hi. I wanted to share with you @Lepresidente @iiamloz that the work that you have done for this has worked wonderfully. My scans are being blocked and crowdsec is getting these signals that should help the community. I upgraded OPNSense to 25.1 last week and with it came the newer version of crowdsec with this improvement. I used the example scenario you gave me on github and that has made all the difference. All these attempts have no business with my services at all.
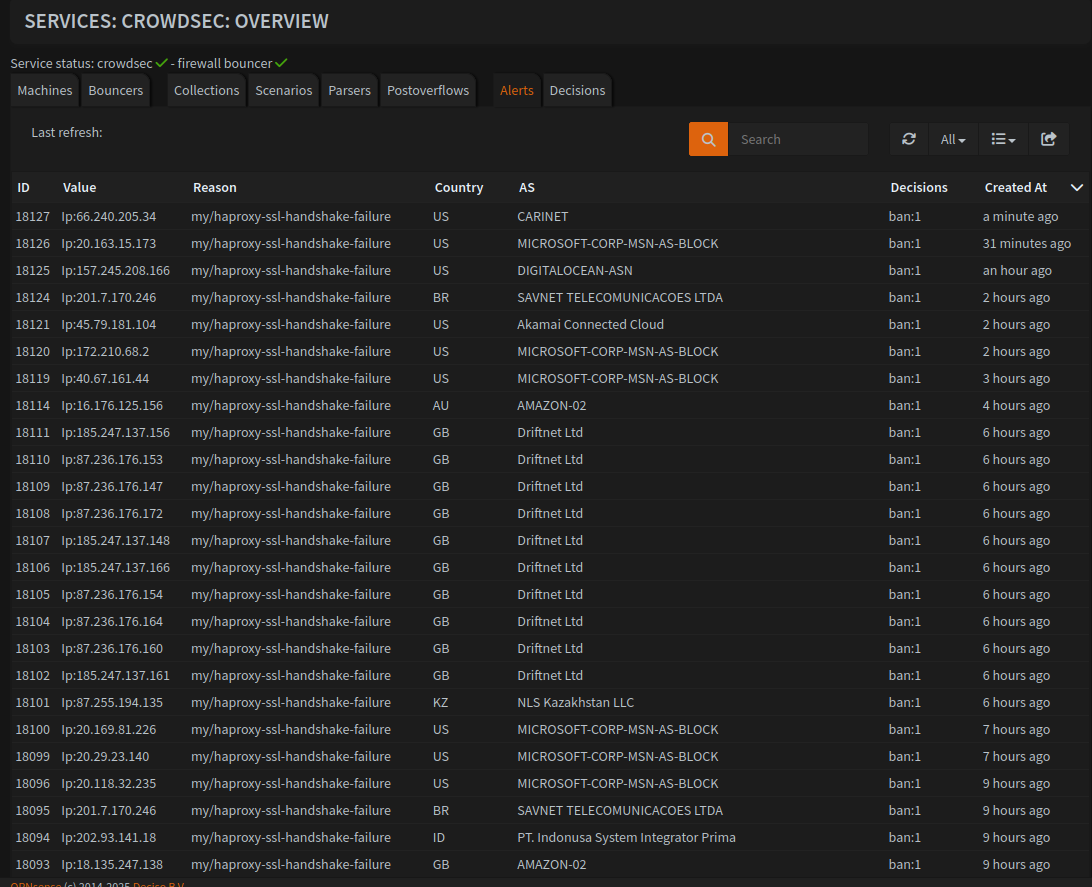
thank you