Immich, Authentik, Caddy with Docker
Hi, I have all three running and functioning in Docker containers. They're all able to communicate with each other. I also have dnsmasq setup to redirect traffic from Immich to Caddy. Caddy is then configure to redirect the traffic to Authentik.
Immich - > Caddy - HTTPS
Caddy -> Authentik - No HTTPS
Immich is configured to issuer URL:
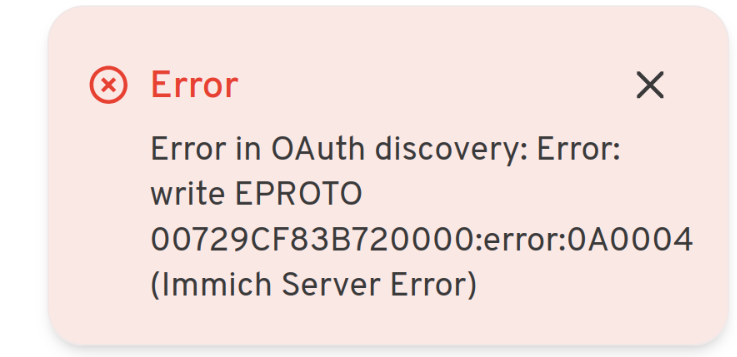
Also, I have that Immich error I shared when clicking
Containers are able to communicate with each and via Caddy. The error I'm getting appeared to be something to do with HTTP or HTTPS protocol error maybe?
Immich - > Caddy - HTTPS
Caddy -> Authentik - No HTTPS
Immich is configured to issuer URL:
https://authentik.local/application/o/immich/Also, I have that Immich error I shared when clicking
Login with OAuthContainers are able to communicate with each and via Caddy. The error I'm getting appeared to be something to do with HTTP or HTTPS protocol error maybe?