detect ddos attack
Hello, is there a way to detect DDoS attacks with CrowdSec? I was attacked, but there was no detection on the CrowdSec side.
13 Replies
Important Information
Thank you for getting in touch with your support request. To expedite a swift resolution, could you kindly provide the following information? Rest assured, we will respond promptly, and we greatly appreciate your patience. While you wait, please check the links below to see if this issue has been previously addressed. If you have managed to resolve it, please use run the command
/resolve or press the green resolve button below.Log Files
If you possess any log files that you believe could be beneficial, please include them at this time. By default, CrowdSec logs to /var/log/, where you will discover a corresponding log file for each component.
Guide Followed (CrowdSec Official)
If you have diligently followed one of our guides and hit a roadblock, please share the guide with us. This will help us assess if any adjustments are necessary to assist you further.
Screenshots
Please forward any screenshots depicting errors you encounter. Your visuals will provide us with a clear view of the issues you are facing.
© Created By WhyAydan for CrowdSec ❤️
did you install the http dos collection?
Yes. Just to clarify, it's a web application in Python with Caddy as a reverse proxy and mariadb for db.
command dos : sudo hping3 -S --flood -V -p 443 1.2.3.4
That might be the issue, CrowdSec can only detect HTTP based DoS attacks.
unless you want to create a custom parser and scenario
Hmmmm, that's what I was afraid of. I'll see how to do it differently or, as you said, create a specific scenario parser.
When I go to the metrics, I can see that a DoS scenario is being triggered, but it doesn't seem to be enough. Do you know why? @GNU Plus Windows User
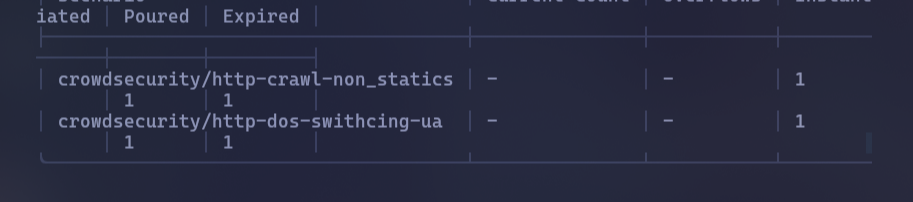
can you share the top row? I can't see exactly what's what, or even better if you can copy-paste the output with the top row preserved.
remember that hping is just a syn flood attack and we rely on something to log these events as we are HIDS, not NIDS. So if traefik reporting anything in logs when the hping comes in?
cause trafeik might not be reporting anything unless your using their TCP modules, cause it not directly sending http data
^ pretty much if it's not in a log then CrowdSec can't detect it
might be useful, typically syn floods are hard to get overcome by: https://www.cyberciti.biz/tips/howto-limit-linux-syn-attacks.html
but you can use the iptables example to do some logging instead of return and you can then use iptables parser and craft your own scenario to block if they repeatly go over the limit.
I might have found something—either way, it stopped me in my tracks. What do you think? @iiamloz
I don't know if it's really good
Maybe add more conditions, I don't know.
It looks like your trying to detect a portscan rather than a DoS attack
Yeah, I thought the same thing — I relied too much on the other iptables parser. I redid it, and I think it's better like this. What do you think?