Overriding TOTP Period Causes Unauthorized / Invalid Two-Factor Cookie Error
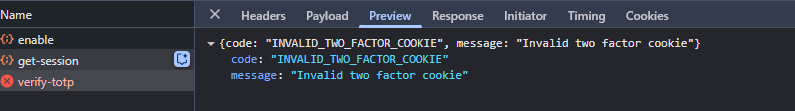
When I override the default TOTP period (e.g. from 30 seconds to 60 seconds) in the Better Auth 2FA TOTP plugin configuration. The attempt to verify totp code end up in resulting in Unauthorized response and an Invalid two-factor cookie message. If you dont override the default period. The code works fine.
I was using Sveltekit when i encountered this error
To Reproduce
I was using Sveltekit when i encountered this error