Recursion errors?
im usddenly having errors on my upsert to profiles table? I had the AI make the policies.
an example of one of the policies it made:
18 Replies
the AS uid seems to break it. and causes the recursion
Your error is likely on a select policy where you are trying to look at the same table. You can't select from the table in the select policy as you have to meet the policy. So recursion.
One way to solve is to put the select on the table in a security definer function so it bypasses RLS. Just make sure to use auth.uid() in the function and not pass it for security.
The insert policy you show will not cause recursion.
i have 4 simple policies. they are all the same. the select, insert, delete, update are all the same to allow current user to edit their own row
i was able to fix it by removing the SELECT inside and just do (id = auth.uid())
is that bad?
Maybe show your select policy currently. You should wrap auth.uid() with select for performance. That is not the same as selecting from the profile table itself in the select policy.
That policy used for USING in select policy is correct to allow user to see their own row. It will not cause recursion.
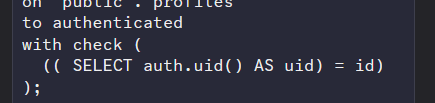
well... it is :/
I highly doubt it.
then what is causing the error? it went away by removing the select
my select on profiles table was public before. i now have it set to be seen only by the current id
Please show your original policy that was failing.
i dont know exactly which one i just know it was one of the 5 i had.
ill show u the last one i have which is unique
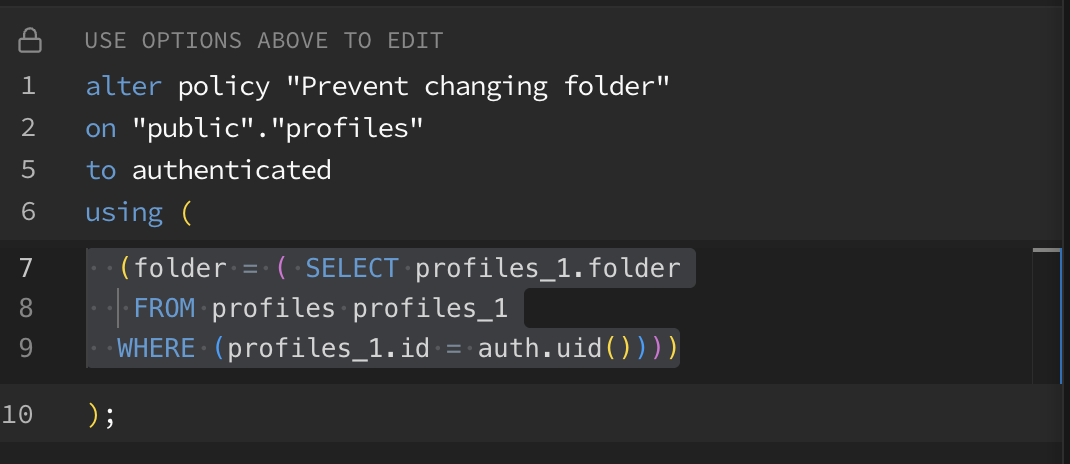
i dont want a user updating the folder column
For performance you want to wrap auth.uid() in a select...https://supabase.com/docs/guides/database/postgres/row-level-security#call-functions-with-select
The policy you just showed will not work as you are selecting profiles.
That will cause recursion.
so its the folder one huh?
i wanted to stop them from editing that colymn once its made
If you need to do that then you have to move the code in that to a security definer function and return folder to compare.
its where i store there images
You can't use RLS to protect columns normally.
You can use an update trigger.
And block column changes by setting new.col = old.col or raise error if it is changing.
Typically I see users using a folder name with the user UUID so you automatically know their folder or even using a bucket per user with the UUID as the name of the bucket.
i made a nanoid for the folder column and used that
i guess i could use the user id... this was back when i felt scared to revela that id in a url