Mikrotik, 2x Caddy (internal only/ internal + public)
Hi all. I have small homelab where I have Proxmox and few services, NetBird, Keycloak, RustDesk, Pihole, 2x Caddy (one as internal proxy for services that I do not want be on public internet and second for publicly available services), ... As main router I have mikrotik cloud switch CRS125.
What is optimal CrowdSec setup in this env? Only router or router + Caddy (external) or router + 2Caddy or only proxy servers? Where to parse logs and where to block ?
108 Replies
Important Information
This post has been marked as resolved. If this is a mistake please press the red button below or type
/unresolve© Created By WhyAydan for CrowdSec ❤️
Depends what you want, I have similiar setup:
internet ---> mikrotik -> lan which hosts various services.
I forward logs from mikrotik to one of the hosts in lan and do some detections there.
Another hosts are also doing some other checks for other apps (like ssh, nginx, home assistant and so on),
all connected to the single local api.
Then I update firewall rules in the mikrotik, and nothing more - personally I believe dropping traffic as close to the source as possible.
GitHub
GitHub - nvtkaszpir/cs-mikrotik-bouncer-alt: A CrowdSec bouncer for...
A CrowdSec bouncer for MikroTik RouterOS appliance alternative - nvtkaszpir/cs-mikrotik-bouncer-alt
though I have not tested that with this device model
Thank you I will look at that. So blocking only on mikrotik? That sounds good. I will look closely how to parse different logs to contribute 🙂 Thank you a lot.
One more question 🙂 How many fw rules is added to mikrotik? 🙂
In general there are added 8 total:
- IPv4 inbound (src) for input
- IPv4 inbound (src) for forward
- IPv4 outbound (dst) for input
- IPv4 outbound (dst) for forward
- same as above for IPv6
They stay as is and should be as high in the stack as possible (well, almost, except IPv4 for default packet counters).
Only address-lists are most dynamically changed objects, and firewall rules look into the IPs in the lists. Those list updates dependson the subscribed lists and number/frequency of the detections and requests to block the IP.
I will try 🙂 Hopefully I do not roast router 🙂
you can add rules and just disable them
the safest option 🙂
then configure the app/container to connect to the mikrotik and update address-lists, if that does not throw errors just enable rules
or you can add them and just don't drop packets but just do logging or passthrough, and if that works rpoerly (logs generated/coutners increased etc) then change it to drop
I have to wait until sons will not use internet, i think, that when i start playing with that it will be a lot of fun 😄
nah, do it now 😄
you can add rules but without
place-before=xx and thut they will be added at the end, usually meaning they will be after 'drop all' rules anyway
then you can disable them, edit them and move them up@KaszpiR because you are so kind, may I ask you, if there are outboud rules too, does this replace PiHole block lists or outbound blocking rules are for different use case?
there are outbound rules (tcp/udp dst ), so that if the ip is blocked then incoming and outgoing connections to it are not allowed - this is to prevend for example connections to command-and-control servers, such that if you have an infected computer on the network it will not try to contact the control server
PiHole rules are I believe different, they just return 0.0.0.0 or 127.0.0.1 (or other specific address) on dns requeests
Ok, i can understand. It is for yet infected. Thank you a lot
this is also to just drop connections to the banned ip,
hm actually I didnt thought of processing pihole logs and then creating blocking certain addresses, but surely this could be useful, but mainly in very specific situations such as infected hosts in the local network
Do you recommend intall CrowdSec as docker compose or od directly to Proxmox container? I have 4 VM with docker, but CrowdSec will be installed on separate VM so using docker labels or volumes is no possible I supose, for that the crowdsec need to run on same docker or not? I think may be install CrowdSec LAPI on that new VM and then instances of log parsers to those other docker vms
You could install a socket proxy on your docker hosts to expose the docker API over TCP then crowdsec can connect to those exposed sockets to get logs
this is obviously good if your on the same LAN, over WAN this is definately not recommended
Ok so I will try to play with CrowdSec, is it ok to install CrowSec for testing and then redeploy that. I have only community free account.
Course, you can install it as many times just some features of the console are locked not the engine itself
Great 🙂 I hope that my sons will not kill me, they have holidays and they are playing some games upstairs 😄
I've got crowdsec LAPI in a container in kubernetes (k3s), separate agent on other hostst to do local processing of the logs (some hosts send logs there via rsyslog because I cannot run crowdsec agent on them), they communicate with the LAPI container. Mikrotik bouncer is also another container and it talks with that crowdsec LAPI and mikrotik device. Also I have one node asking Loki for logs for parsing. Yeah it's super complex because I'm lazy and mixing bare metals with containers is complex enough and i just don't need vms 😄
I suggest keeping certain components separate, such as dedicated crowdsec lapi as a container or vm (this allows to migrate data or upgrades separate from other components)
So I tried to install CrowdSec on proxmox containter and then on same hoste mikrotik bouncer as docker container. I have problem to connect to crowdsec which is running on host, inside containter I did setup
extra_hosts:
- "host.docker.internal:host-gateway"
but in log i can see that it cannot connect to crowdsec API 😦
So in config of crowdsec I setup listen_uri 0.0.0.0:8080 and it works now 😄 But I do not know if my router can handle that 😄 almost 15000 IPv4 addresses and 220 IPv6 😄
you can look at the stats of the mikrotik device - cpu and memory
yep I'm looking there, when it imports CPU is 100% 😄
but it blocked few packets already 😄
Now I have to do something with mikrotik logs 🙂
ow, and how long does it take to process it?
first one was long, then it was shorter 🙂
it is about 90s
it is a lot 15k IPv4 addresses is a lot 🙂
for processing logs I have to process only those which are not dropped by mikrotik bouncer, or all of them? If I will process all of them then it will report already reported IPs, is that ok?
I suggest processing logs which managed to pass through the firewall, so you will process only new ones, and not the existing ones (a bit less load)
that's a long time, looks like the device wasn't reaally designed for this, so maybe it would be better to have a router between the switch and ISP
if not then I suggest setting TICKER_INTERVAL to
90s or something like it, because default value is 10s and it will wait blocked with updates
or even maybe more, like 300s to trigger update once per 5min
but it depends on if the device gets any other slowdowns when the list is updatedIt looks like it is updated once per hour
I have one mikrotik question. I have rules from bouncer and another drop rule for imput which is behind bouncer rule. In log I can see rows where are prefixes for bouncer rule and for my rule too. Does it mean, that mikrotik firewall does not stop processing on first drop rule?
depends on the action of the rule
also it depends on the fact if this is input or forward rule - they are different conditions
notice routing decision split
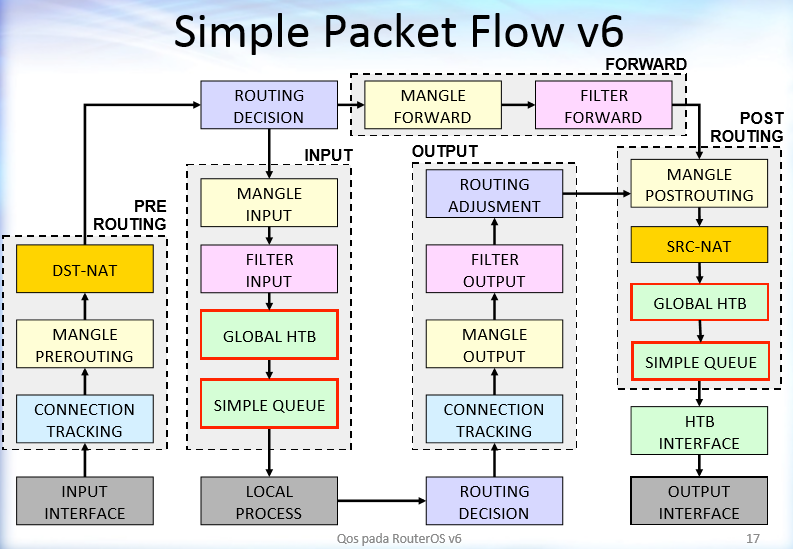
which happens between the fw deciding if the traffic is to the local device (input, such as mikrotik service port) or to forward it o antoher host (such as devicce after NAT to dmz)
2025-07-05T20:03:44.455391+00:00 router firewall,info crowdsec_input_drop: drop_input_no_lan input: in:ether1[INTERNET] out:(unknown 0), connection-state:new src-mac c4:ad:34:16:87:52, proto TCP (SYN), 167.94.138.179:55842->192.168.10.250:25, len 60
crowdsec_input_drop prefix is from crowd sec drop input rule drop_input_no_lan is drop rule which almost at the end of rules drops everything comming from wan.
well, if it is at the end of the firewall list of the rules, then no wonder it's processed at the end
move it as high to the top as possible (except the default rule to count the packets)
ok but crowd sec rule is at the start #2 the second rule is #16 both are input and action is drop. What I do not understand why there are prefixes from both of them. I thought that first drop rule drops packet and it does not go to next rules
is it enabled, is it set to drop?
yes
and prefix from both rules is on same row in log
is the 167.94.138.179 already banned?
I think so, because if not then why will be there prefix from crowdsec rule in log
also, if you have a drop + log on the rule, then it means it works
though a bit late in the processing...
It seems to me that #2 and #16 both input rule and action drop are triggered which is strange
I wanted to parse only logs which are not from crowdsec rules, but if both rules are triggered, then I do not know how to do that 😄
first of all, don't enable logs for the crowdsec rules 🙂
sure, but this packet has to end on crowd sec rule and never made it to my rule #16
frankly speaking I created specific rules for logging (selected port list I know I dont use), to avoid flood from other rules
one more thing, today I added new branch named
raw to allow also dropping rules in ip firewall raw (prerotuing/output), so it should drop i way earlier (to the point of breaking certian things but whaever). No container yet, though
gonna leave it for 24h to see how it goesis there any way how to find if the IP is really blocked by crowdsec? My router is not happy with 15000 IP in IPv4 address list 🙂
yea, get some vps or something like it, check its ip, use
cscli decision add --ip vps-pi --scope ip --reason test --type ban --duration 4h and test on the host connection via nc or curl to the target service
we can test it live tomorronw (i can provide you with my public ip and you could give me some endpoint to test and we can see if it works), but now i'm gonna go to sleep for over 8h, I'm dead tired 😄
unless you have 5minI have 5 min, but I thought about that logged IP 195.154.199.60 i cannot find it in address list, but I do not trust that my router can find that IP in 15000 long list 🙂 so if I can try find 195.154.199.60 in crowdsec if it is blocked
167.94.138.179
what's you public ip and port + service type?
93.99.217.145
try blocking
89.68.252.42 and tell me when the mikrotik gets the update, then I'll try curl again
wee, Czechia, just around the border 😄Update in progress
still working
still updating 😄
How many IPs do you have in list?
234028 (but active address list is way lower)
wow 😄
and what router do you have? 😄
about 15k per update
yep 15k per update and update runs for me 1x for hour
https://mikrotik.com/product/hap_ax3 pretty good price for the wifi AX (Wifi 6, or maybe 7?), 4 cores and high cpu clocks
hAP ax³ | MikroTik
Our top-of-the-line AX home access point. With all the processing power and speed
your household might ever need.
Gen 6 wireless, 2.5 Gigabit Ethernet, PoE, WPA3, and more!
previously hap ac2 but it started to struggle with the up/down link speed from the ISP (1Gbit down/40 down, it got a bit choked by the 1Gbit, and effectively could reach about 600Mbit stable, but 1G was too much)
hm what is difference between ax3 and ac3
ax is a new standard
wifi 6 (ax) works better with multiple wifi devices, so the benefit is much larger over local network (such as laptop - wifi - NAS) than over the internet
ah but AC3 have 5Gbs eth ports 🙂
at first I was thinking about ac, but then looked at the specs and decided to go ax
so AX has better wifi? that is it?
ac has cpu 32bit, IPQ-4019, 448-896 (auto) MHz
update complete
ax has cpu 64bit, IPQ-6010, auto (864 - 1800) MHz
it works (i mean it drops connection)
also ax has a higher router license, more ram etc - bigger faste better 😉
Ok, I will think about it, I thought about som pfsense or opensense and buy some router for it, But I need 24 ports of my switch and to buy 2.5GB switch for 24 lines is expensive
hAP ac³ | MikroTik
A wireless dual-band router with 5 Gigabit Ethernet ports and external high gain antennas for more coverage.
hAP ax³ | MikroTik
Our top-of-the-line AX home access point. With all the processing power and speed
your household might ever need.
Gen 6 wireless, 2.5 Gigabit Ethernet, PoE, WPA3, and more!
ask your ISP if they give something more than 1gibt, if not then there;s no point in fighting it
you can have a router between the isp/lan-switch (i have)
I have not 89.68.252.42 in log 😄
(means it was dropped and not logged)
I know, but I still need to connect 20 devices so I have to live with 1Gbps even for internal network
yep
that is strange too 🙂
I don't know where you read it but in the spec it has just 1gbit ports, while ax3 has 2.5gbit port on wan
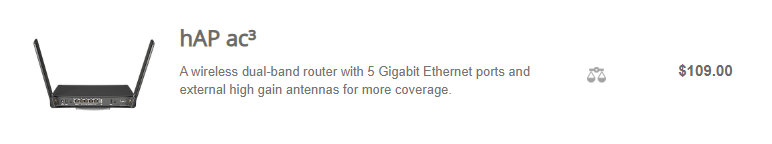
I red that wrong I thought 5Gbps ports and that wa 5x1Gbps 😄
oh lol indeed, looks like a typo
I guess it means five gigabit ports, not a five 5GBit ports 😄, so yeah its 5x1gbit, not 5x5gbit 😄
(frankly speaking it could be a real achievement for that hardware)
thank you, now im confused more 🙂 I works but it was not logged 😄
I think may be logging just drops some messages 😄
I'll leave the curl loop, though I'm not sure when the laptop will go to sleep and may stop trying
now I'm going to sleep, cu tomorrow
Thank you aggain and gn
oh it is in log now, it drops not in input chain, but in forward chain
Cause its nat
Ok im really off now 😆
So now I'm parsing mikrotik log. And I do not know what next 🙂
I'm using your bouncer, but there are no statistics in console from that bouncer.
Since I'm parsing that mikrotik log I do not know if there is anything usefull done based on log informations
But I have one allert in web ui in CrowdSec 🙂
my bouncer does not expose any metrics
actually I was looking at implementation a week ago and seems like there is not much details about it, also device report stats once per 15min
the only metrics which are implemented are exposed by the bouncer and accessible in the prometheus format, by default on port 2112
I subscribed for another blacklist, but then I had to unsubscribe, that was too much for my router 😄
Now I have to find out what I can do with those parsed logs. It has some scenarios when I enabled mikrotik parser a1ad/mikrotik-bf and a1ad/mikrotik-scan-multi_ports but I do not know if I can add another scenarios or that is it 🙂 anyway really thank you for help
Now I have working something 🙂 it was fun . Now I know that I need better router 🙂 And I have to decide if it will be Mikrotik again or something else 🙂
Arent decisions something what have to be made from log parsing or from alerts?
a1ad/mikrotik-bf and a1ad/mikrotik-scan-multi_ports are very trigger happy even for valid connections - to the point I had legit connections to github being marged as multiport scans, so I disabled them and use something different
decisions are from various sources:
- subscribed blocklists
- scanned logs and if certain lines match then it generates action for example to block the address
- manual adding ip to block via cscli/web
And what is something different 🙂 I have only those two 🙂
I wrote my own rules
otherwise I mainly depend on processing logs from specific ports accessed on mikrotik (such as 3389 RDP which I do not use), failed ssh logins, http logs , and some other things
Ok, so you are getting logs from other places like proxies and so on. 🙂 I have not enabled SSH from wan no RDP, everything like this I'm using over NetBird
ngix logs, linux, sshd, http-cve, home-assistant, and some other collections from the hub
and do you watching logs for say ssh or other services which are not accesible from WAN because it can be triggered if some one somehow gets into your lan?
no
On mikrotik I use NAT to ssh and web server (and other services) and thus I forward logs from multiple sources (log files) and machines/vms/container/whatever into two hosts that process those logs and do decisions
for example I scan ssh invalig logins and run decision to block it in mikrotik - similiar to fail2ban but instead of firewall block on the host or calling custom script I can send decision to crowdsec, the mikrotik boucner gets it and updates the ban, so it drops everything, not just ssh
Resolving Mikrotik, 2x Caddy (internal only/ internal + public)
This has now been resolved. If you think this is a mistake please run
/unresolveI updated docker image for boucer and it logs this :
bouncer-mikrotik-dev | {"level":"fatal","func":"config","ip_firewall_raw_rules_src":"","time":"2025-07-08T15:22:07Z","message":"ip_firewall_raw_rules_src cannot be empty"}
Unresolving Mikrotik, 2x Caddy (internal only/ internal + public)
This has now been unresolved.
Ok I did not catch that MIKROTIK_FIREWALL_RAW_ENABLE must be set to false 🙂 default is true and I had working config from before, so I did rename filter rules bud did not realize that raw rules are enabled by default 🙂
GitHub
Release v0.7.0 Breaking: Support Firewall Raw · nvtkaszpir/cs-mikr...
Previously only firewall filter was available and used, now this version allows to use firewall raw, which helps to reduce load of cpu/memory, especially on low resource devices. It implements #2
B...
yean 0.7.0 has some env var name changes and new raw rules
Today I bought ax3 🙂 now I have max 20% CPU so what are env settings recommended for that beast 🙂 I had almost everything setup for old router 🙂
MIKROTIK_IPV6=false if you dont use IPv6
MIKROTIK_FIREWALL_FILTER_ENABLE=true
MIKROTIK_FIREWALL_RAW_ENABLE=true
MIKROTIK_UPDATE_FREQUENCY=1h
USE_MAX_TTL=true
DEFAULT_TTL_MAX=4h
TRIGGER_ON_UPDATE=true
TICKER_INTERVAL=20s
If you have a stable internet then you can set default max ttl to 2h
Also if the blocklists are small ( under 20k enteies) then ticker interval can be lowered to 15s or 10s, but check how frequently the lock wait raises, and if it raises in seconds ( which is what you do not want to see more often than once per few hours, generally lock wait should take nano/microseconds)
Generally you need really fast hardware to be able to insert over 20 thousand addresses under 10s, so going with ticker interval lower than 10s usually is not worth it.
I guess I need to add additional pages with recommended settings for certain devices and a short guide how to tune the setup
So you are using both raw and filter rules?
Resolving Mikrotik, 2x Caddy (internal only/ internal + public)
This has now been resolved. If you think this is a mistake please run
/unresolveyes
What is benefit to use them both? It is somehow splited to use some IPs on filtered and som on raw rules?
they all use the same address list, raw and filter work in different packet flow processors
GitHub
Maybe drop at "Raw" is better? · Issue #2 · nvtkaszpir/cs-mikroti...
Isn't Raw have better performance? And you only need two rules Both are prerouting, and one put the Dst blocklist, the other put Src. blocklist.
so then filter rules can be disabled then?
depends on your setup, probably yes
but if the raw drops most of it maybe filter would catch something 😉