CrowdSec Windows Exchange
Hi folks. I would like to secure my Exchange Server with Crowdsec. Crowdsec is already installed and configured.
I have a Sophos Firewall in front of my Exchange Server which acts as a WAF.
When I tested CrowdSec with a few failed logins, it blocked the IP from my Sophos (my internal IP from the gateway - 10.102.225.1) instead of the public IP from the “attacker” (94.237.100.231).
I have also configured X-Forwarded-For.
In the IIS logs the public IP can also be found (94.237.100.231), but CrowdSec doesn't seem to parse it properly or something.
I followed the official Crowdsec guide to securing the exchange, but it seems to be a bit outdated and no longer works. (https://www.crowdsec.net/blog/how-to-protect-microsoft-exchange-server-crowdsec)
Some IIS logs: https://pastebin.com/nuX111RY
Thank you very much in advance.
How to Protect Your Microsoft Exchange 2019 Server with CrowdSec
Follow this step-by-step guide on installing CrowdSec on a Microsoft Exchange server to better protect against common cyberattacks and new threats.
Pastebin
#Fields: date time s-ip cs-method cs-uri-stem cs-uri-query s-port c...
Pastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time.
8 Replies
Important Information
This post has been marked as resolved. If this is a mistake please press the red button below or type
/unresolve© Created By WhyAydan for CrowdSec ❤️
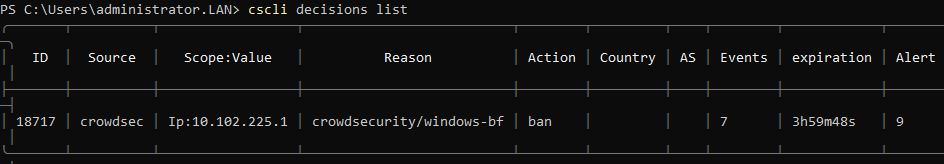
Hello,
Crowdsec is not looking at the IIS logs to detect a BF on Exchange, but directly at the windows authentication logs (in the event log) as IIRC there's not enough information in the IIS logs to determine if the request was a failed login attempt or not.
Can you look in the event log at events with id 4625 in the Security channel and see if the proper IP is present in the event ? (unfortunately, i think it's unlikely but we may get lucky).
If the IP is present, it should just be a matter of updating the parser to get it from the correct field
and you also probably want to install the default whitelist for local IPs to avoid banning them (https://app.crowdsec.net/hub/author/crowdsecurity/log-parsers/whitelists)
Collections, AppSec Rules & Configurations | CrowdSec Hub
Manage collections, configurations, remediation components, and AppSec rules with CrowdSec Hub. Streamline security with tools and integrations for enhanced protection.
Hi blotus,
thank you for your answer.
Unfortunately, the public IP is not included in the event log. So there is nothing that can be done?
And you meant Crowdsec does not look in the IIS logs. But the official guide from you refers to the IIS logs. Is that wrong in the guide then?
I'm not sure, I'd have to dig into this, but I'm far from an exchange expert.
The IIS logs are included in the guide in order to detect more generic scanning against OWA (eg, bots randomly scanning the internet)
Ah okay, thanks.
I will tinker a bit and will try if I can fix it somehow. Thanks for your input! :)
Resolving CrowdSec Windows Exchange
This has now been resolved. If you think this is a mistake please run
/unresolve