✅ Prevent unauthorized access to WEB API folders and files within the folder.
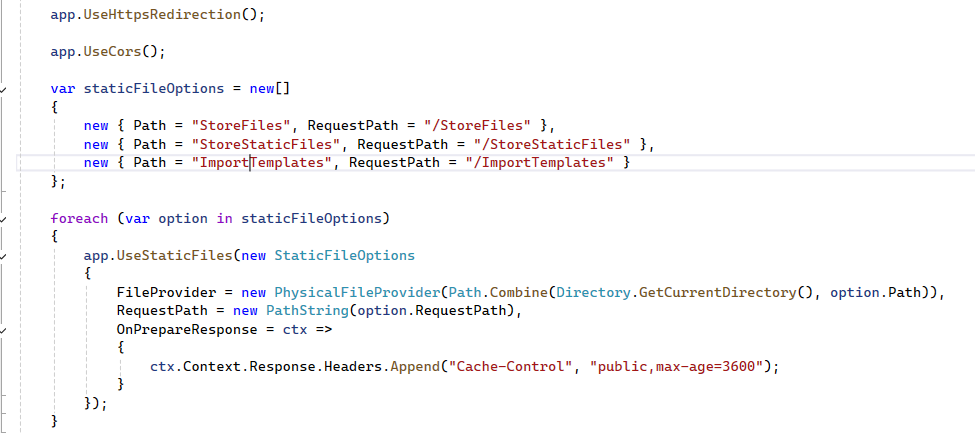
In my .NET 6 Web API project, I have an UploadFiles folder where user-uploaded files are stored. Currently, anyone who knows the folder path or file URL can directly access the files in the browser, since static file middleware serves them without authentication or authorization.
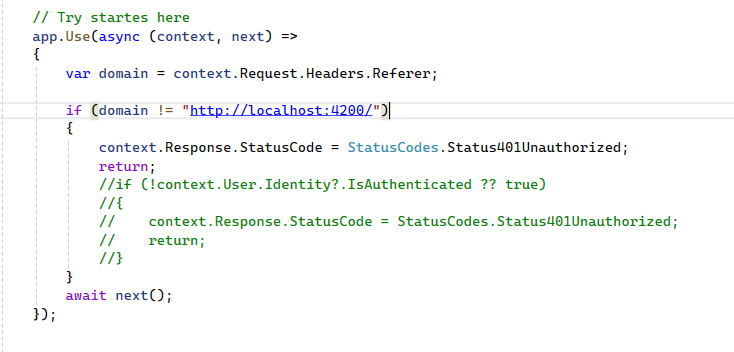
I want to restrict access so that only authenticated users (or users with a signed/secure link) can download these files. Middleware like UseAuthentication and UseAuthorization doesn’t protect static file requests by default.
I want to restrict access so that only authenticated users (or users with a signed/secure link) can download these files. Middleware like UseAuthentication and UseAuthorization doesn’t protect static file requests by default.