Schema adjustment not being reflected.
Hi guys,
I'm hoping someone may be able to give me hand with this, I'm 90% confident I'm missing an extra step here or something.
I have a
Inside my
One of the schemas I have defined is named under
After making these changes, I have ran
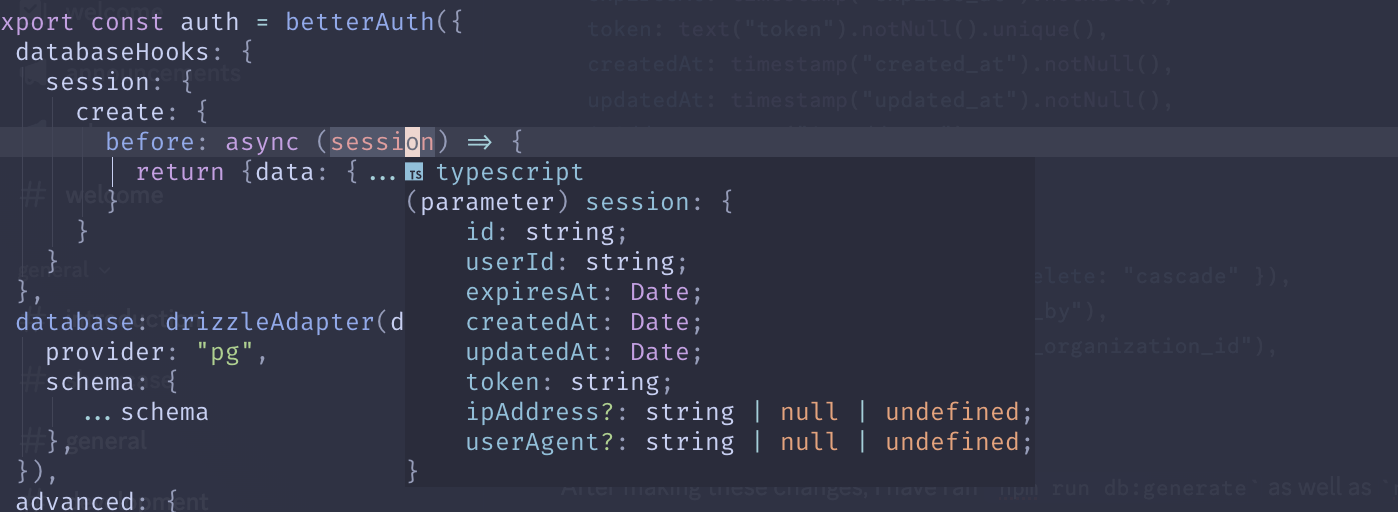
When navigating to
However, when I use
Does anyone know how I should go about aligning the better auth types with my DB structs? Thanks
I'm hoping someone may be able to give me hand with this, I'm 90% confident I'm missing an extra step here or something.
I have a
/schemas/index.tsInside my
auth.tsOne of the schemas I have defined is named under
auth.tsusersessionAfter making these changes, I have ran
npm run db:generatenpm run db:pushWhen navigating to
local.drizzle.studiosessionHowever, when I use
getSessionDoes anyone know how I should go about aligning the better auth types with my DB structs? Thanks