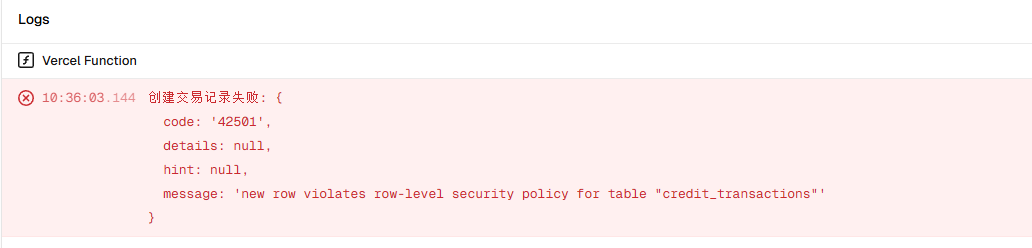
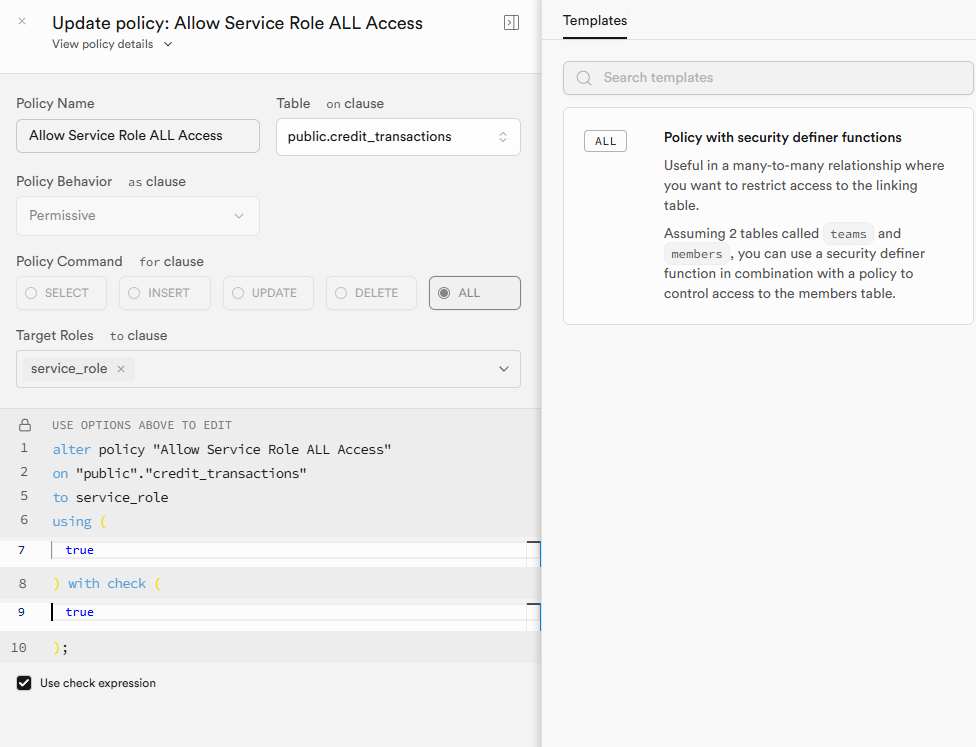
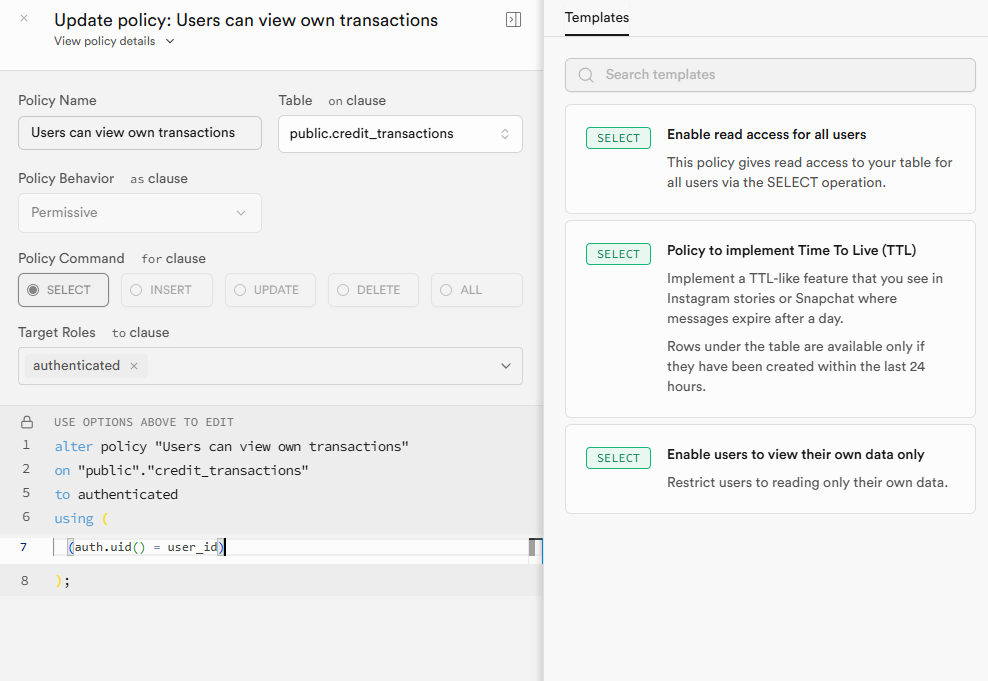
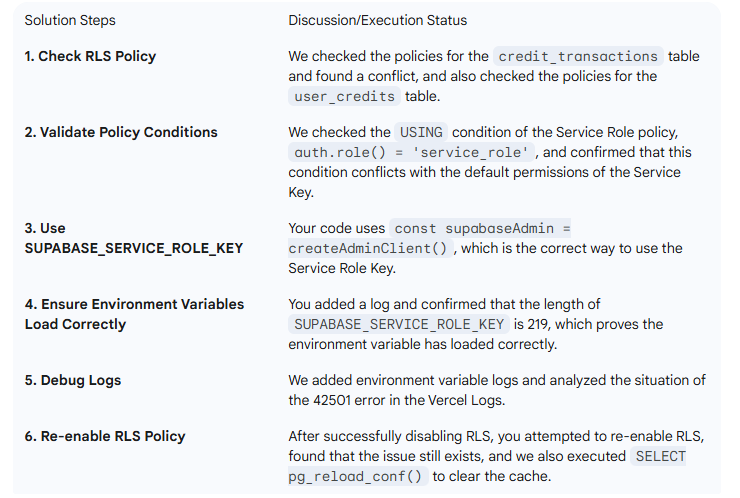
new row violates row-level security policy for table "credit_transactions"
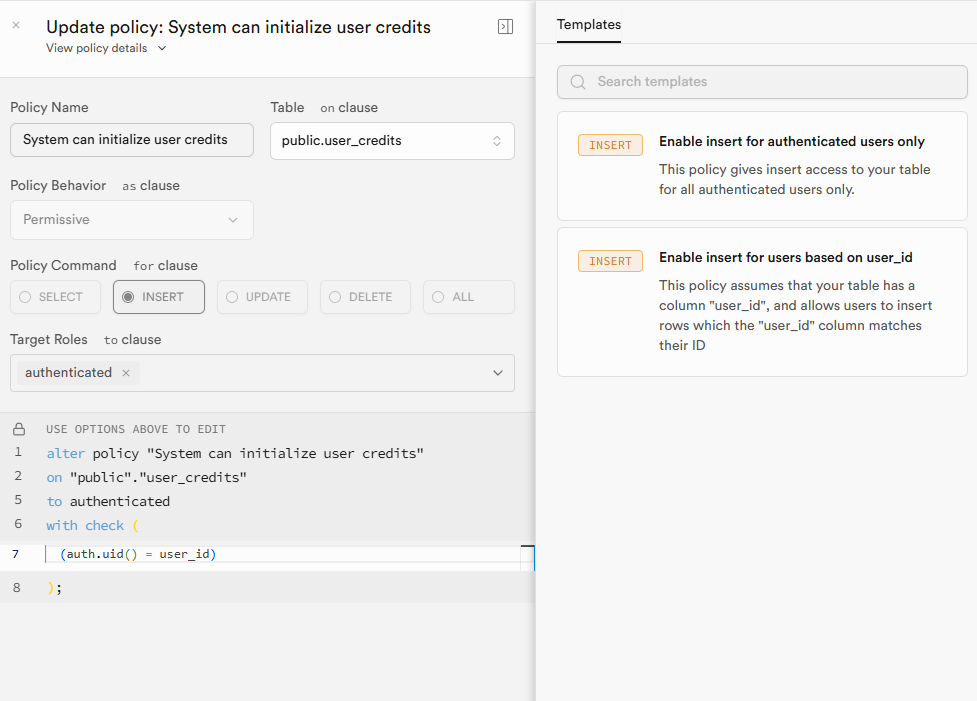
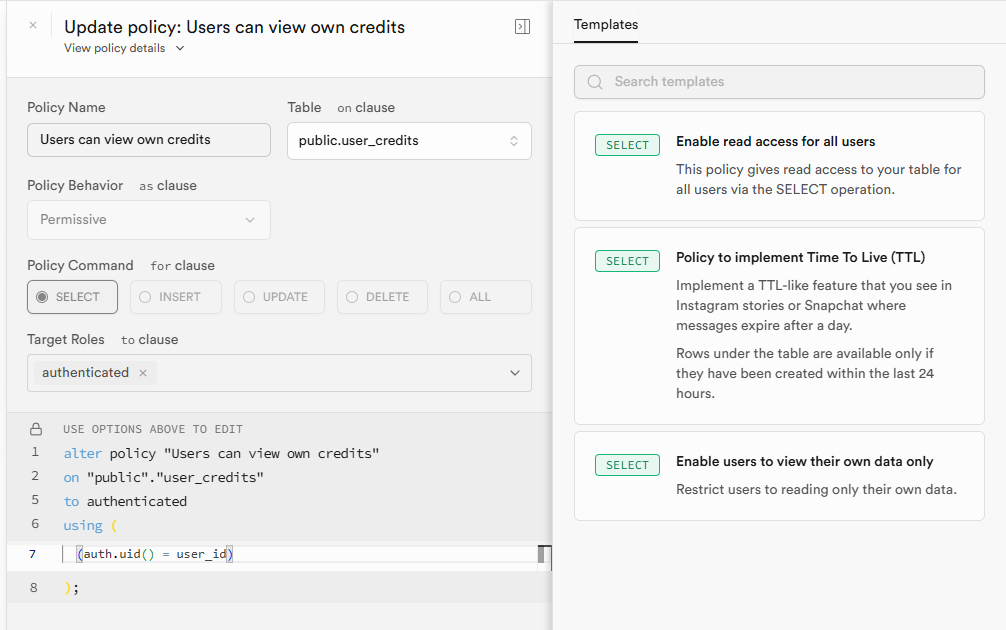
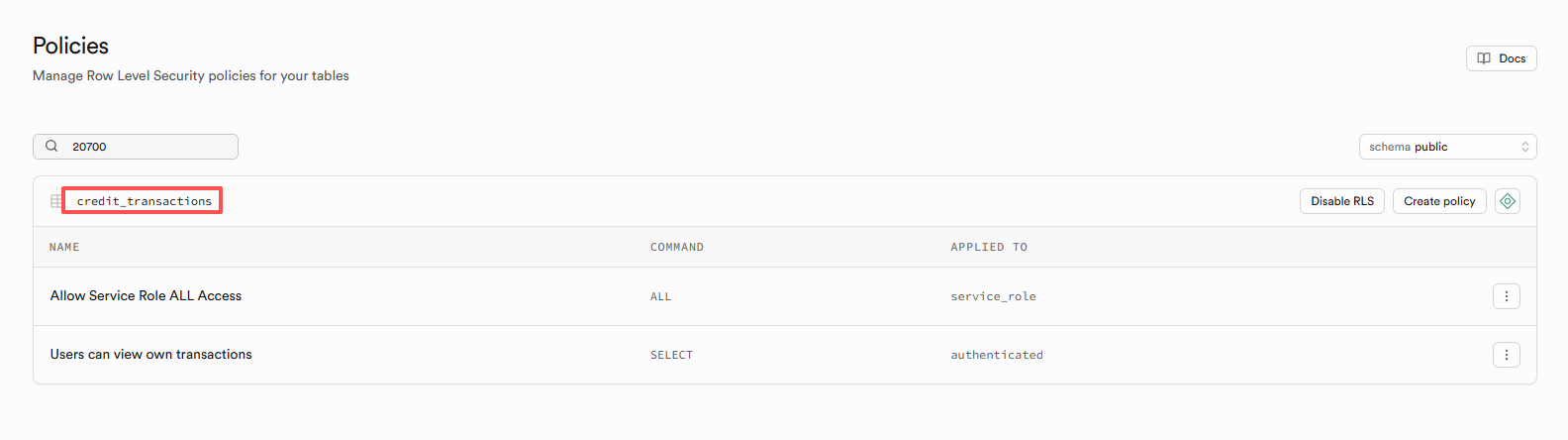
I have been encountering issues with the RLS policy of supabase. My production environment has been reporting this error in vercel. The Policies in my relevant table are as follows. SUPABASE_SERVICE_ROLE_KEY is also correctly configured and loaded, and has been debugged according to different schemes. The result was still the same error.