Authorize Mastra cloud user for using the agent
Hi, I have setup Mastra auth by extending MastraAuthProvider, so now Mastra cloud can not access my Mastra agents.
What's the best way to authorize Mastra cloud user?
10 Replies
📝 Created GitHub issue: https://github.com/mastra-ai/mastra/issues/10397
🔍 If you're experiencing an error, please provide a minimal reproducible example whenever possible to help us resolve it quickly.
🙏 Thank you for helping us improve Mastra!
Hi @Yannick can you show me your
FrontofficeMastraJwtAuth ?
In Cloud we do inject a studio token so that cloud wont be locked out!Hi @Abhi Aiyer
Sure, here it is:
I guess I need to authorize Mastra cloud too. How can I reference the studio token?
Hi @Yannick mastra cloud should automatically authenticate the injected studio token
Can you please share your cloud project slug so we can trace the auth request?
Hi @rph my cloud project slug is future-quiet-autumn
Note: I was not able to set the correct Mastra API URL as path ´/´ is protected. I have set path ‘/api’ which is public.
I had the error Unable to reach Mastra instance. Status: 401 in the UI form
Hey @Yannick ! Thanks for sharing the project slug and details.
We have a PR in progress to add SimpleAuth to core (#10490: https://github.com/mastra-ai/mastra/pull/10490), but didn't want to leave you hanging until that lands.
In the meantime, here's a workaround — you can wrap your existing JWT auth with a simple token fallback:
Then update your config:
Set these env vars on your deployed instance:
Then in Cloud Studio, when connecting your instance, add the Authorization header with your token value (see attached screenshot).
Once the PR lands you won't need the wrapper class anymore. Let us know if you hit any snags!
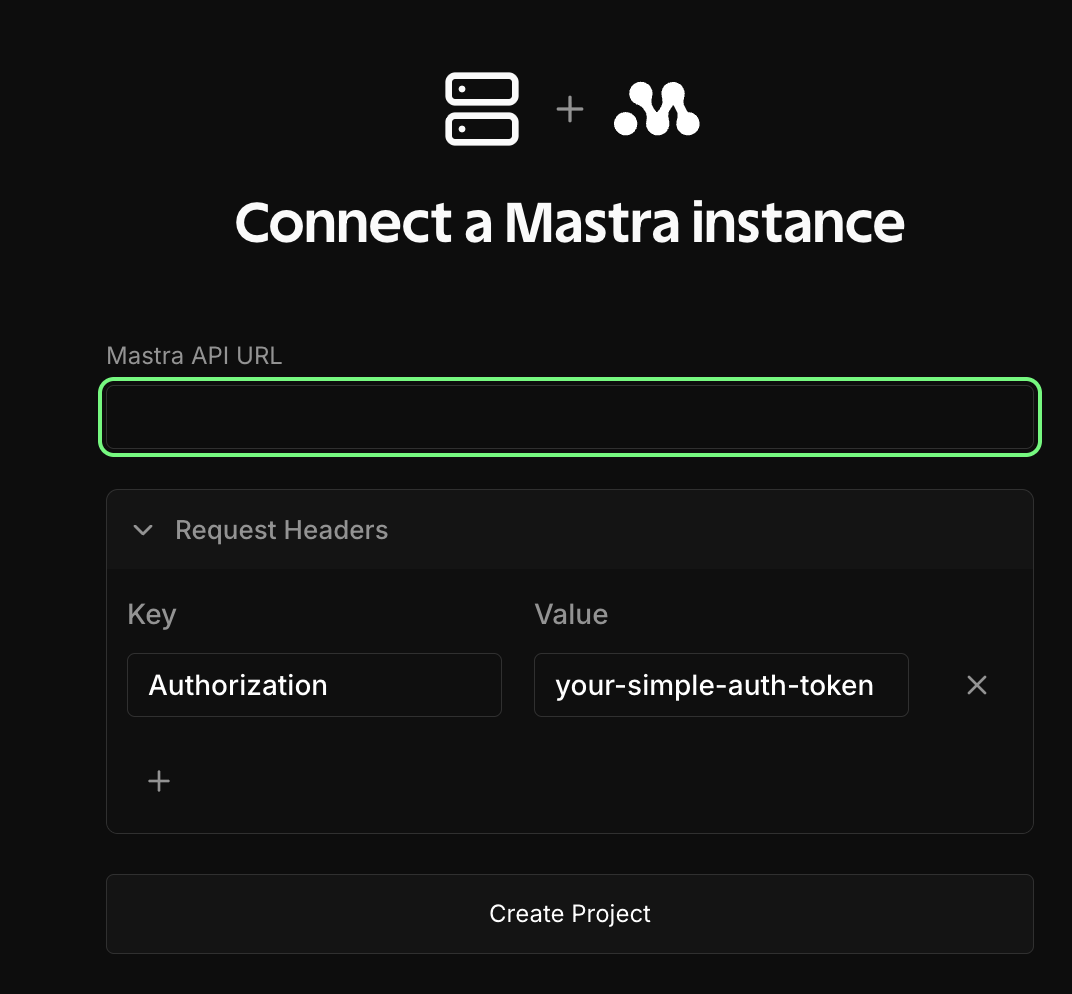
Perfect I’ll give it a try!
Thanks 🙏
Hey @Yannick ! Just wondering if you had the chance to try the workaround Ryan shared? Let us know how it goes 😉
Thank you everything is working well with Mastra Cloud now 😉
Awesome! Thanks for checking and getting back to us!