Parser failures with NPMplus logs
Let's Encrypt IPs Blocked by CAPI – Need Whitelisting Guidance
Enroll command bug ?
Decisions not displaying on browser page.
does installed Crowdsec packages smoothly transition to the PfSense upgrade to 2.8.0 release?
Error 500 connecting to app.crowdsec.net
opnsense bombarded with blocks coming OUT of the LAN
docs about running tests are incorrect
../cscli -c ../dev.yaml hubtest run --all is not working as expected...Deploy CrowdSec in agent mode with docker-compose
PSA: Installing crowdsec on ancient Debian 8 can trigger systemd segfault
systemctl --force --force reboot but it will trigger reboot IMMEDIATELY)
crowdsec version 1.6.9 on amd64
```text...Traefik Bouncer not pulling from CrowdSec API
crowdsec-firewall-bouncer and crowdsec-traefik-bouncer. While the firewall bouncer is working fine and regularly pulling decisions, the Traefik bouncer is listed in cscli bouncers list but shows no IP address or last API pull timestamp:
It seems the Traefik bouncer isn't communicating with the CrowdSec API. Any idea how to troubleshoot or resolve this?...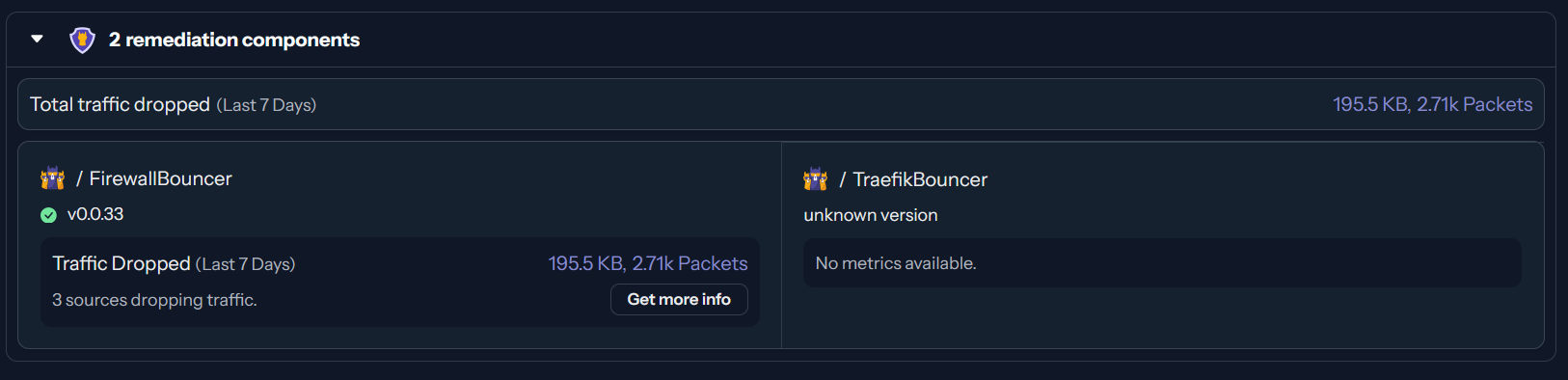
Possible bug in cscli decisions list
Anyone know how to setup Notifications in a Multiserver Architecture?
Scenario is not banning IP
Question creating Postoverflow Whitelist
Direct manipulation of the allowlist in the database.
allow_list_items table directly in the DB, is it going to be picked up by the LAPI immediately or on a restart of the LAPI only?Manual decision disappear before expiration
cscli decision list -s "Massive Leech" but passing some minutes, the decisions disappears, far before the expiration. How is it possible?Apache parser failure
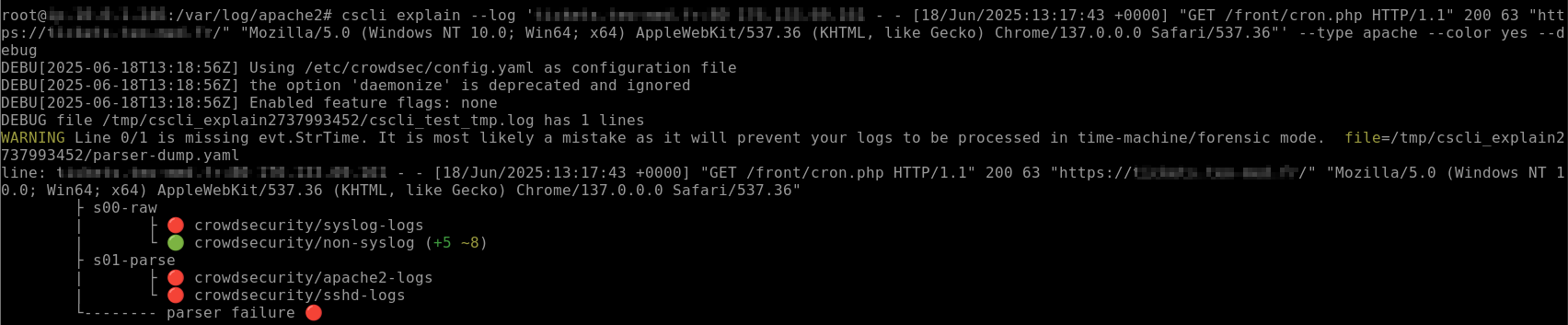
Docker infrastructure with multiple services and host strategy
Crowdsec log questions.