CrowdSec for CloudPanel/WordPress websites
NPMplus won’t connect to api
how to get notification variables
"title": "{{.Type }} {{ .Value }} for {{.Duration}}",
I was reading this documentation but I do not understand how to map the parsed values to the notification variables, in order to create custom messages, can someone please show me some example?...Ban all IPs parsed from a specific acquisition
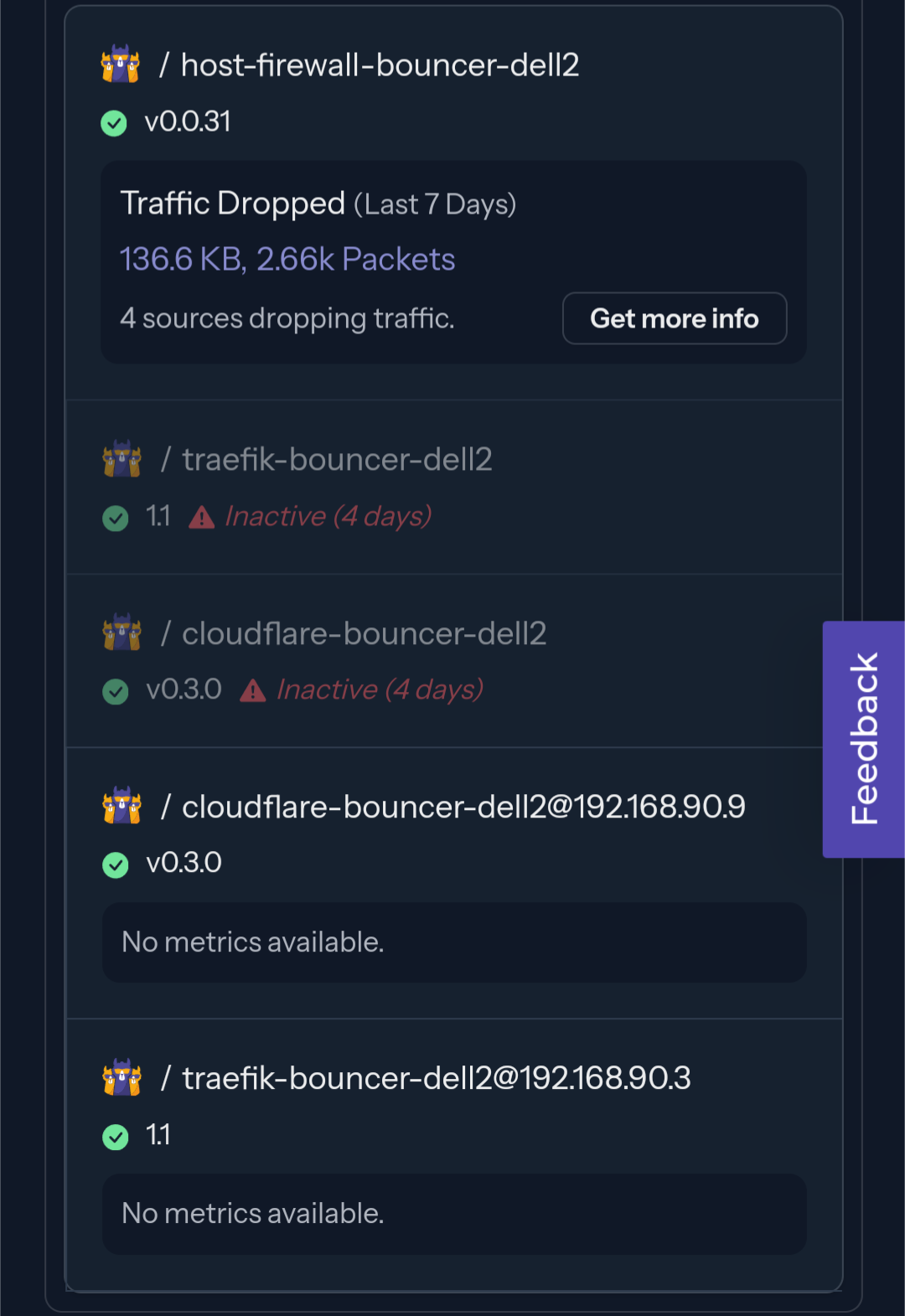
Inactive bouncers
Instant attack notification stays disabled
Max number of machines a LAPI can handle
Query local api for scenario containing http
Docker Compose Crowdsec Cloudflare Bouncer on Free Cloudflare account
docker compose exec crowdsec-cloudflare-bouncer crowdsec-cloudflare-bouncer -d
docker compose exec crowdsec-cloudflare-bouncer crowdsec-cloudflare-bouncer -d
docker compose exec crowdsec-cloudflare-bouncer crowdsec-cloudflare-bouncer -s
docker compose exec crowdsec-cloudflare-bouncer crowdsec-cloudflare-bouncer -s
Seafile Creating Http-probing
Enable appsec only for specific NGINX locations
Multi-server setup, database, should we comment out the db config for all the nodes
Cloudflare Worker : error 1001
Help me update my possibly outdated crowdsec setup.
LePresidente/authelia
...
Bad IP lists in open source (free) version
cloudflare worker & pricing
Need an insight for cloudflare tunnels --->> Nginx ---->> Website
Testing AppSec rules with POST body contents
/wsstatusevents/eventhandler.asmx and containing xp_cmdshell should trigger the rule. When I'm simulating such a request, it's not blocked, though.
As far as I know this is an in-band rule, so it should react immediately. I have successfully tested with GET /rpc2, so the AppSec component itself seems to be functioning. POST requests that only consider headers being set seem to be result in the expected response too.
When I check the (debug) logs I see this:...file.yaml doesn't work
Permanent ban for IPs and ASNs