Unexpected SSL Certificate Behavior and Switching Between Certificates Without Change
I'm experiencing a strange issue with my domain. The Cloudflare proxy is currently disabled, and the SSL/TLS setting is configured to Full (strict).
However, I’m encountering the following behavior:
DNS is set to “DNS only” (gray cloud) for all records, and the domain resolves properly from external locations.
The correct Let’s Encrypt certificates are still installed and active in Plesk for all relevant subdomains.
Locally, a request with curl -v mydomain.tld shows renegotiation attempts and sometimes switches between certs.
The server itself occasionally cannot resolve the domain due to Temporary failure in name resolution, although this seems to be a local DNS config issue.
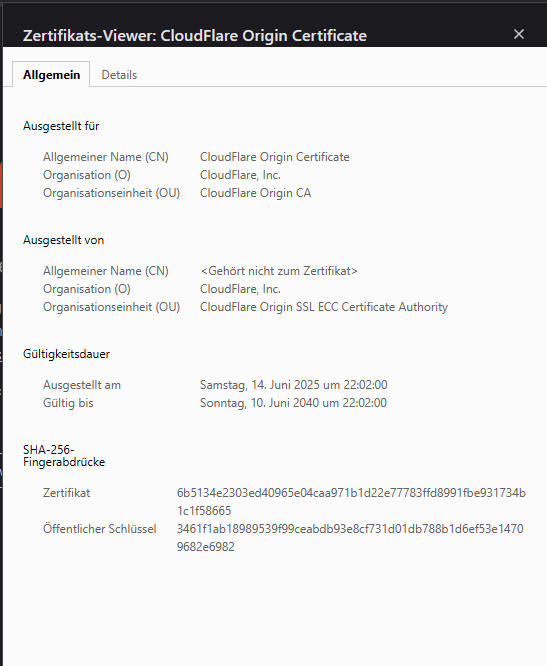
To my knowledge, no one has changed or imported certificates, and yet the cert behavior is inconsistent and unpredictable.
However, I’m encountering the following behavior:
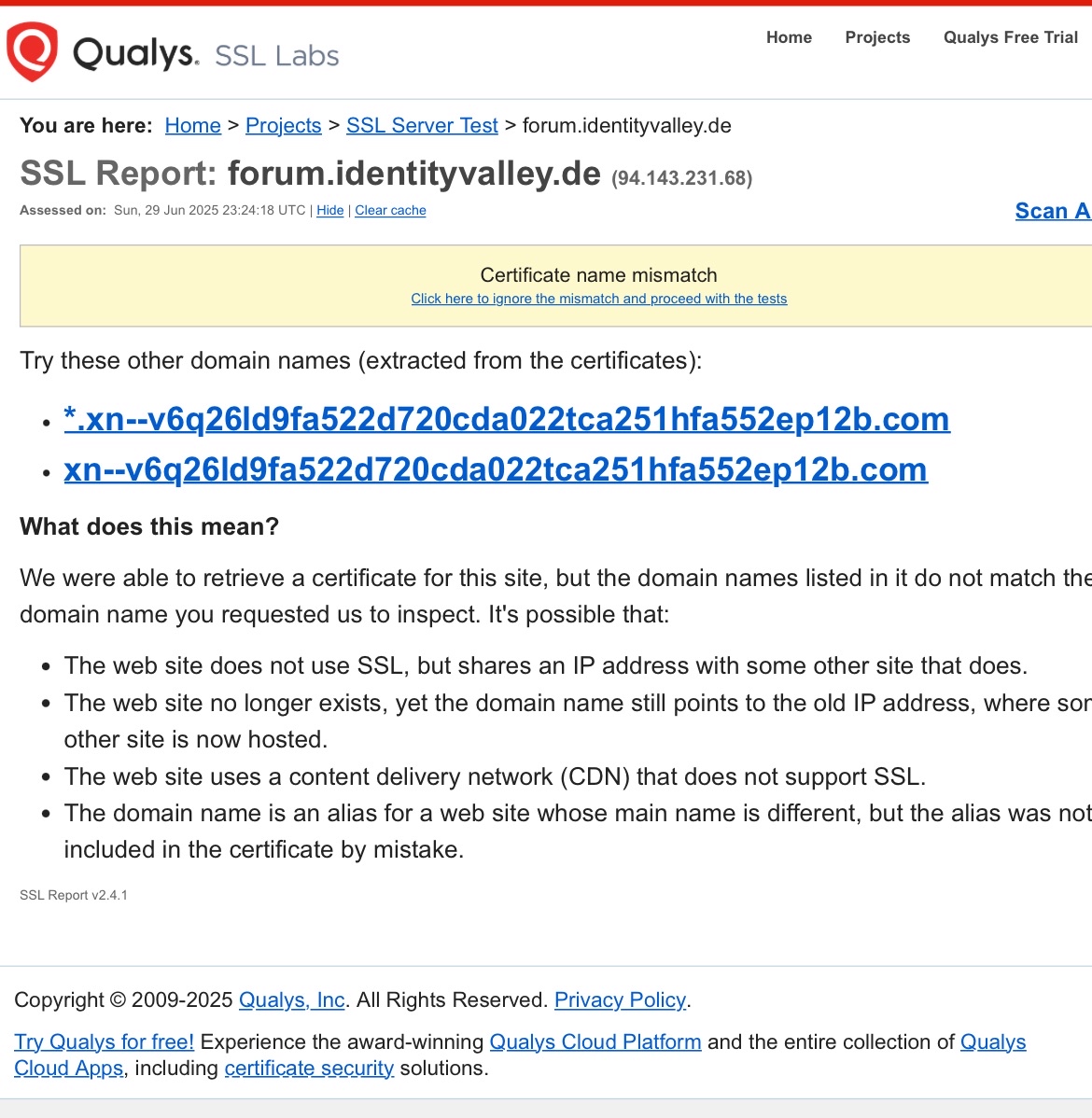
- When the proxy is enabled, visitors receive an invalid SSL certificate, which does not match the domain or expected Let’s Encrypt cert.
- When the proxy is disabled, the correct Let’s Encrypt certificate appears intermittently, but sometimes a Cloudflare-branded certificate is presented instead.
DNS is set to “DNS only” (gray cloud) for all records, and the domain resolves properly from external locations.
The correct Let’s Encrypt certificates are still installed and active in Plesk for all relevant subdomains.
Locally, a request with curl -v mydomain.tld shows renegotiation attempts and sometimes switches between certs.
The server itself occasionally cannot resolve the domain due to Temporary failure in name resolution, although this seems to be a local DNS config issue.
To my knowledge, no one has changed or imported certificates, and yet the cert behavior is inconsistent and unpredictable.