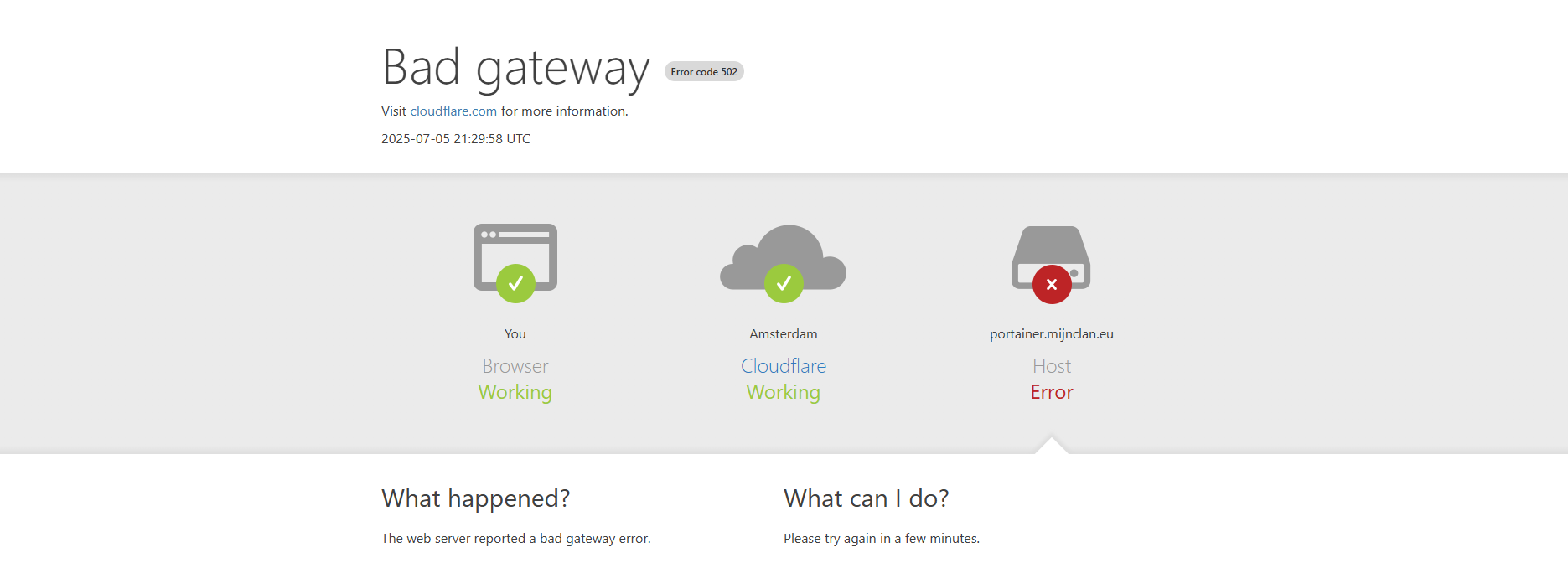
Hey, im using a cloudflare tunnel to proxy my local portainer server. But its not working
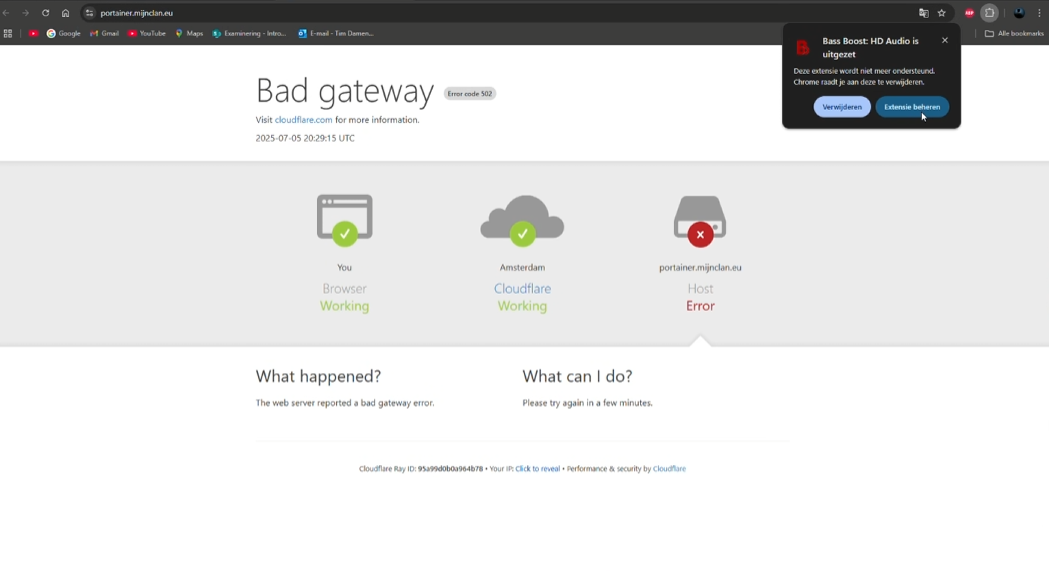
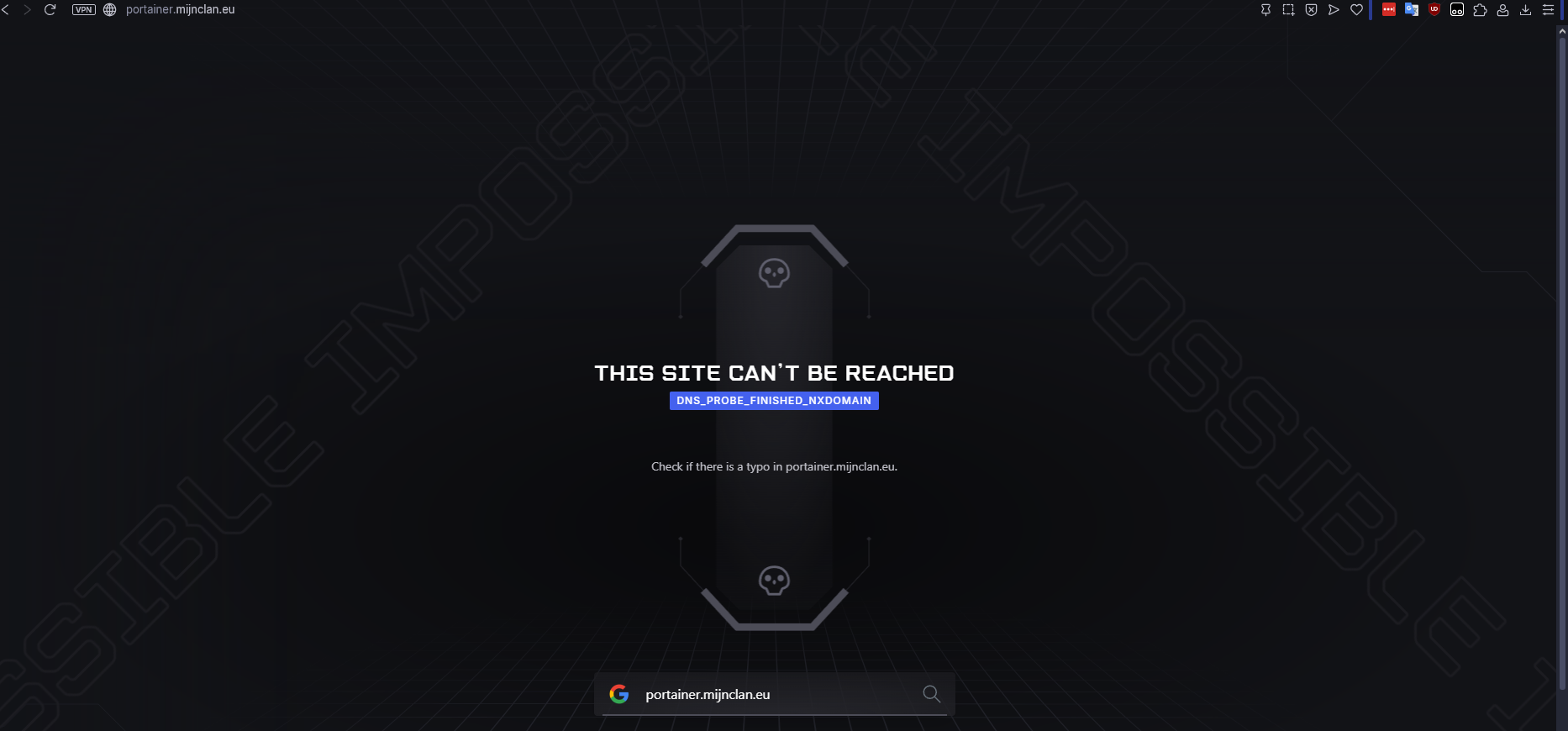
Hi, I’m using a Cloudflare Tunnel to expose my local VM. The tunnel status shows as healthy, but when I visit the domain, I get the error: DNS_PROBE_FINISHED_NXDOMAIN — the site can’t be reached.
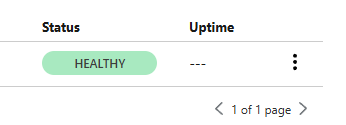
I attached a screenshot from a friend who can access the Cloudflare dashboard but not the routed tunnel itself, which should lead to the VM.
Checking the tunnel logs, I sometimes see these errors:
And after some time:
Also, when the Docker container running the tunnel is active, I can no longer connect to the local IP address 192.168.1.100:9334, and the SSL secured domain doesn’t work either.
What could be causing these issues?
I attached a screenshot from a friend who can access the Cloudflare dashboard but not the routed tunnel itself, which should lead to the VM.
Checking the tunnel logs, I sometimes see these errors:
And after some time:
Also, when the Docker container running the tunnel is active, I can no longer connect to the local IP address 192.168.1.100:9334, and the SSL secured domain doesn’t work either.
What could be causing these issues?