How does push notification and VAPID keys work?
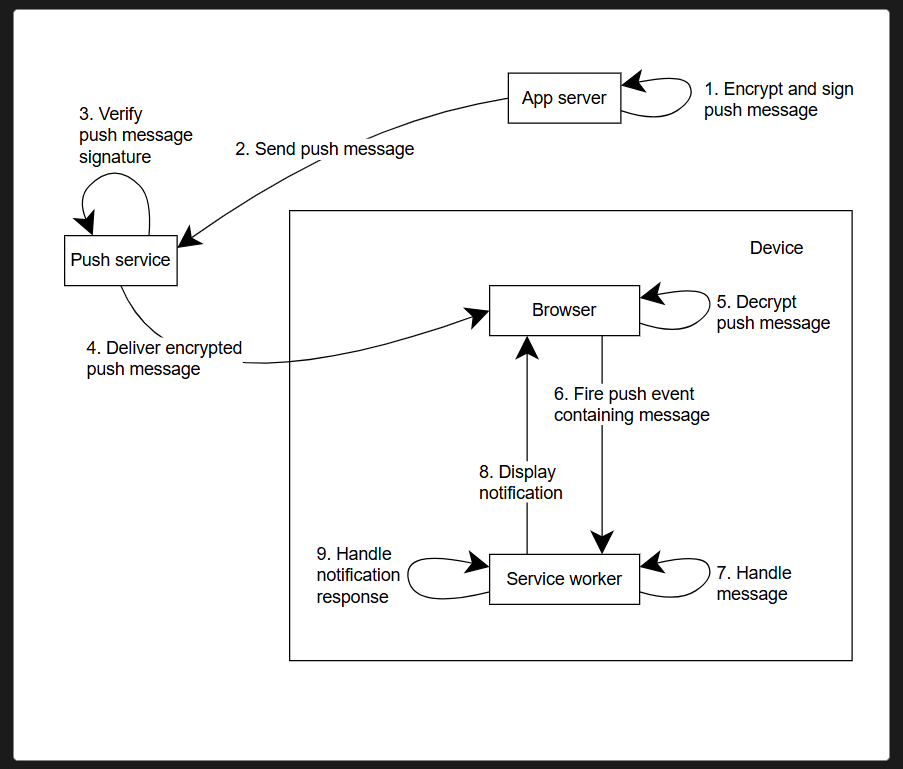
Hello, was reading a bit about push notification on PWA. From what I've understood, our browser never sends push notification directly to our app. The idea is, our browser sends it to a push service and then the push service delivers it to a server that will then delivers it back to us?
Can someone confirm if the flow I gave is correct please.
I also read that during the exchange between browser to push service and push service to web server, we have the signing of keys, public and private VAPID keys.
From what I've understood, our browser tells the push service who we are. Then server side, the server signs back with its private keys to make sure that we are the one who we claim to be and sends the message.
This is where I'm a bit confused.
Why can't we use just a single public key? What's the job of the private key here?
43 Replies
found that on mdn, one thing I'm confused, when we send push notifications, like say we need to inform all the registered users that an event is going to take place on a specific date, how do we create the message/push notification?
pub/private keypairs are an important part of online security. When you sign or encrypt something with a public key, you can verify or decrypt it with the private key. If I have the private key and you have the public key, you can send me messages and I can both verify that you (or at least someone in possession of the public key) sent it, and decrypt it. It works the same the other way around, I can send you a message that you can then verify is mine and read
the public key is something which can be easily accessible?
yeah
we've got a system in place (the trusted root certificate authorities) which lets people verify that the public key they got belongs to a person that was trusted by the certificate authorities, so that it's verifyable that say... the message you got from google.com is actually sent from a server owned and operated by google.com
but in essence that's added onto the pure form of public/private keypair encryption
the idea is simply that you can sign/encrypt something and the other party can verify/decrypt without you two having to exchange all the tools necessary to do both over a potentially unsecure connection
yeah I see, I understood the idea of the key, but why one is public and one private, this is what confuses me
I'm not entirely sure there's a significant difference between the two, if I'm honest... but my understanding of the topic isn't that deep
the private one is for the entity trying to prove its validity though, so the http server that's serving your website will keep the private key safe and send out the public key to end users
public/private keypair encryption goes way beyond just HTTPS though
oh ok
it's used almost everywhere that you have to have private communication over open networks, including e2e encryption in chat apps, VPNs, and lots of stuff like that
yep I see, will read a bit about the public/private key but I have an overview of how it works now, thanks !
there is a difference between the public and private key
i can't explain it properly, but there is
I know they're in a different file format, but I didn't think that purely cryptographically there was a difference in the actual key itself
I think the public key file has information in it on the certificate chain, where for the private key that is generally unnecessary and not done
im not talking about the file format, but the huge prime number
and I think the private key is more likely to be encrypted itself (with simple encryption) and require a password/decryption key to unlock, though it's also common for that to be skipped
it's skipped because its inconvenient
it's a huge pita to always type the password
usually yeah
I've used a few systems that keep the private key locked with a password
they should
depending on how secure you want it
https://www.quora.com/Could-you-switch-the-public-keys-place-with-the-private-key-in-the-RSA-algorithm
that makes absolute sense to me
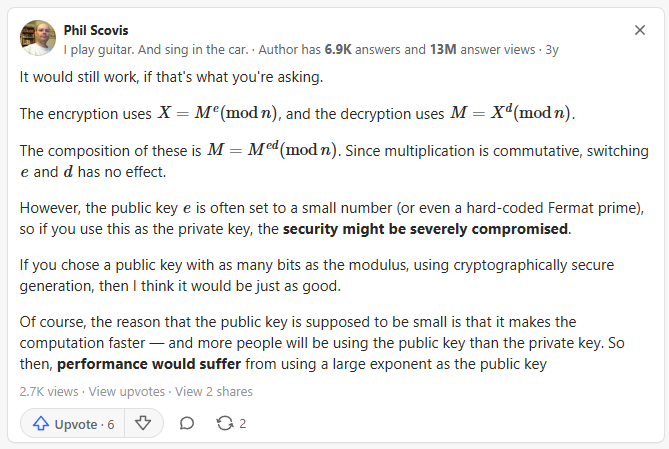
about this
I don't quite agree with performance suffering because of a larger public key because more people use it. Each individual use comes with its own computing power. The private key is the one where each subsequent use is stressing the same set of CPU cores. But yeah, basically they're the same except in practice they're not quite
server cpu have instructions/acceleration to reduce the load of these operations
they even have instructions to accelerate the routing operations
This is not quite right. Public key cryptography—also called asymmetric cryptography—is where you have a public and private key. As opposed to symmetric cryptography where there is only one key.
Anyway, with public key cryptography you keep the private key private and share the public key. The private key can generate a new public key and can be used to cryptographically sign something. The public key is what is used to encrypt data.
Say I make a pub/priv key pair and I put the public key on the internet for others to get. I write a program and sign it with my private key. You can then use the public key to verify the signature. But the public key cannot sign anything, only verify a signature.
Say you then want to send me something encrypted. You encrypt the file using the public key and I can use the private key to decrypt the file.
Summary:
You use the private key to:
* Cryptographically sign a file
* Decrypt a file
* Create a new public key
You use the public key to:
* Verify a cryptographic signature
* Encrypt a file
NEVER SHARE THE PRIVATE KEY! That's what is used to prove your "identity"
my understanding is that the public key is still used to encrypt traffic originating from the end-user in HTTPS, right?
like, the server encrypts with the private key, the public key is used to decrypt, but when I send things to a server over HTTPS, my data is encrypted with the public key (in such a way that it requires the other key to decrypt)
HTTPS uses elliptic curve cryptography to dynamically agree on a symmetric key. Which is kinda like pub/priv but not
hmmm
Asymmetric cryptography has a limit on the size of data that can be encrypted while symmetric has no theoretical limit. So for HTTPS and the like they use a form of asymmetric cryptography to create a symmetric key
Sorry to jump in :c, I think we hash the data first, then we encrypt data using our private key
the signature is verified by a CA I think
No, private keys don't encrypt, they decrypt. Private keys are used to sign a file
hmm, okay. It's been a while, sorry for the misinformation
there's a bunch of stuff I forgot too :c, need to refresh
we always make use of the user's public key to encrypt things?
Yes
See the bullet lists ☝️
yeah I see, I guess that's how the maths work, public key is to encrypt, private key is to decrypt.
One thing though, when we sign the message/file, we encrypt that together with the message?
No, signing only says that "this data hasn't been tampered with". It has no encryption by default. Of course, you could sign something with your private key and then use my public key to encrypt it.
ahh ok I see
No, signing only says that "this data hasn't been tampered with"that's why we still need CA, because the data might be intact/not modified but we don't really know who send what (we can't be sure) ? like a man in the middle can intercept, write its own msg and send back to recipient the recipient has no idea of what happen
The CA (Certificate Authority) is basically a central repository of public keys. It has nothing to do with the data, as that's the purview of cryptography.
When you try to access discord.com, for instance, your web browser hits up the CA to get a trusted public key that is then used to verify that the web site the browser visits is indeed discord.com—the public key you got from the CA is used to encrypt some data that discord.com decrypts and then responds to start the TLS handshake).
yeahh I see
Thanks !
I have one question
when we need to send a push notification
what is the process?
I mean
we intereact directly with the database?
Like, modify database directly, then trigger a function on server that will send this particular msg from the database to the push service, then push service will distribute the message to registered users?
anyone knows how this is done in real world?
Like say I have a mobile app and I want to send a notif to ALL users because an event will take place on a specific date, what's the process here?
I’ve never used push notifications since they have been, historically, unreliable. And I’ve not read up on the new way to do things so…can’t help you with this one. Sorry 🤷
np
it might be a good idea to open a new post. This one was kind of on two topics anyway, and there's lots of history now, so new folks might not poke their heads in
yeah was thinking the same, will do so
I don't have any experience with push notifications either, beyond knowing you usually use an external service and send them an API request or something. From Epic's lack of answer, I figure the same is true for them
ok, will create a new thread see if there are people who worked with push notif
i've had very limited experience with it
at work, we offload that to some other tools
https://discord.com/channels/436251713830125568/1406615780279455794 in case anyone comes here to answer, please use the new post