security question
⚔️Security
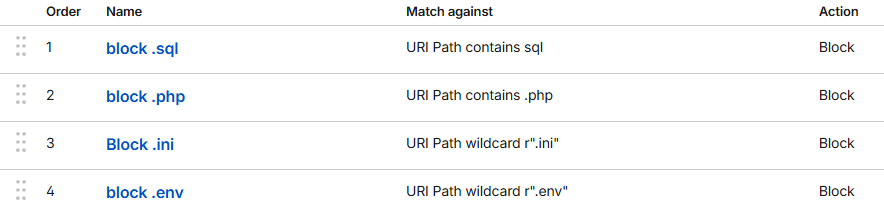
Is this ruleset more or less enough to block bad actors from requesting things?
(I understand that security comes in layers, and as such I have secured the Web App part and the Database part as much as I could, but I need further clarification if these CloudFlare rules are enough or do you use custom ones)
(I understand that security comes in layers, and as such I have secured the Web App part and the Database part as much as I could, but I need further clarification if these CloudFlare rules are enough or do you use custom ones)