But that still doesn’t prevent a malicious actor from just setting the origin header to one of your
But that still doesn’t prevent a malicious actor from just setting the origin header to one of your tenant domains, bypassing the block


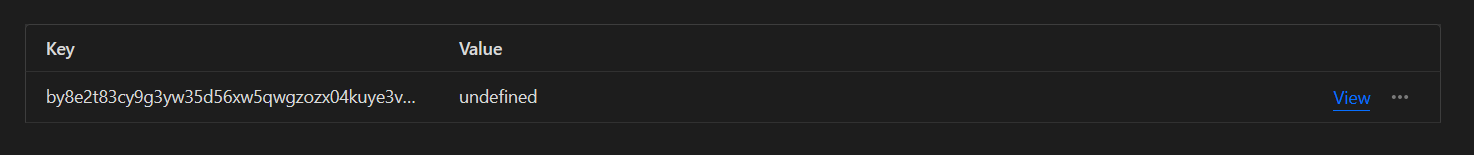
useruser.id, and [ Object ].id is undefinedconsole.log(env) output anything? It should be a map of your bindings.walletID - ?fetch.get is "failing" silently because it's just returning null.itty-router-openapi and what's happening there. If envget should work, as it's a method on the binding type.





user.id[ Object ].idundefinedimport { GetGuid, CheckAuth } from '../../util/Util';export async function CheckAuth(env, walletID){
console.log(walletID)
console.log(env.SESSION.get)
try{
const sid = await env.SESSION.get(walletID)
console.log(sid)
}
catch(ex){
console.log(ex)
}
console.log("SID")
}console.log(env)walletIDconsole.log(env).getnullitty-router-openapigetexport const createSession = async (user: any, databaseConfig: KVNamespace) => {
let absoluteExpiration = 30 * 24 * 60 * 60;
let expiration = new TimeSpan(10, 'd');
const sid = generateRandomString(60, alphabet('a-z', '0-9'));
const SessionBody = {
email: user.email,
email_verified: user.email_verified,
expires_at: expiration,
};
try {
await databaseConfig.put(sid, user.id, { metadata: SessionBody, expirationTtl: absoluteExpiration });
} catch (error) {
throw new Error('Error creating session');
}
return sid;
};