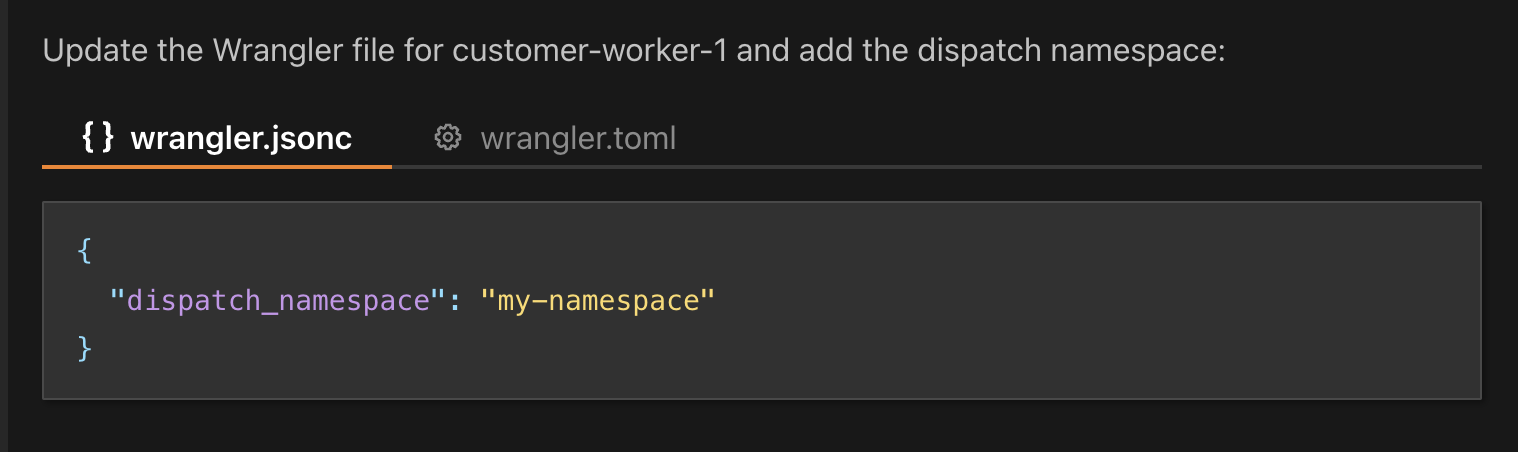
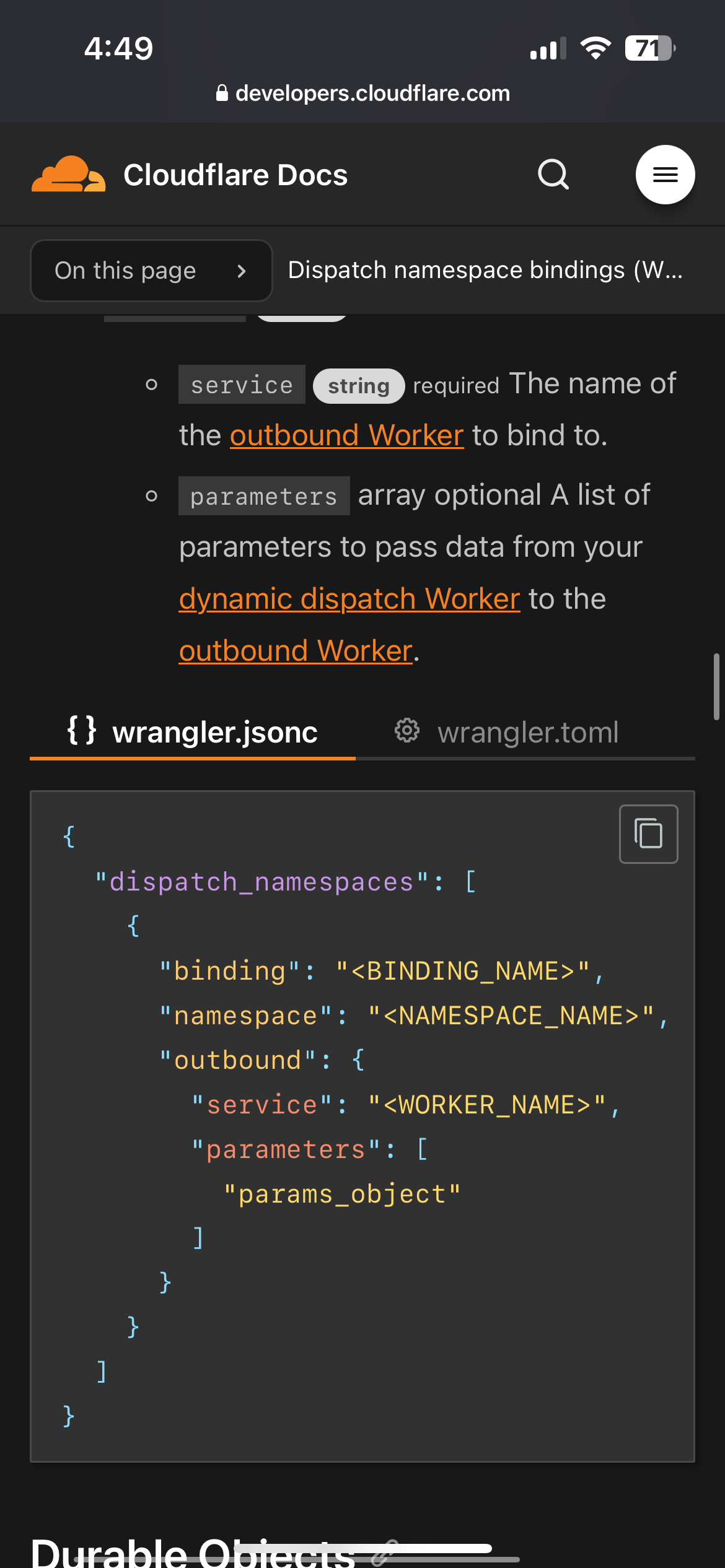
Very interesting question, let's talk through it So, in the case of someone hosting something malic
Very interesting question, let's talk through it
So, in the case of someone hosting something malicious, you'll likely receive a domain. You'll know what customer that domain tracks to.
You also control the upload path so you can log who uploads what and when.
I'd recommend also having analytics/logs for general traffic (Analytics Engine + Workers Logs would be ideal)
Then for a user Worker sending requests maliciously, we have Outbound Workers which again you can use to track analytics + Logs and tie these outbound requests to specific customers
So, in the case of someone hosting something malicious, you'll likely receive a domain. You'll know what customer that domain tracks to.
You also control the upload path so you can log who uploads what and when.
I'd recommend also having analytics/logs for general traffic (Analytics Engine + Workers Logs would be ideal)
Then for a user Worker sending requests maliciously, we have Outbound Workers which again you can use to track analytics + Logs and tie these outbound requests to specific customers