Restrict
POSTPUTfw-test.kian.org.uk to a Content-Length less than 4096 (and block any that don't include it at all, will accept 0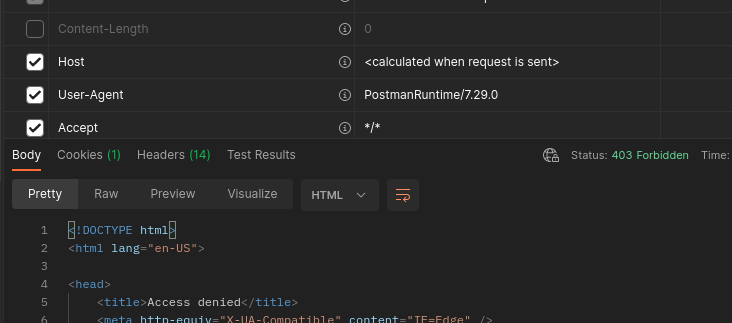
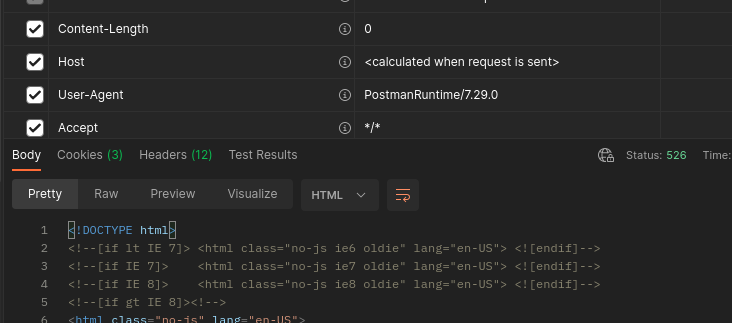
Example POST - (domain goes nowhere, expected a 526)
I believe you can just do
Edit: I am confusing myself
any(http.request.headers["content-length"][*] > 4194304). If there is no Content-Length header - because the body is empty - the expression will evaluate to false.Edit: I am confusing myself

Probably - ruleset engine hurts my brain
Well, yes, don't do ruleset when tired haha
What’s the worst that’s gonna happen, find another input validation vuln?

I wish the firewall rules highlighted which condition you met - but that’s another story
Thursday night VULN discovery = Friday afternoon incident. So yes, that might just be the worst thing that can happen 

Pls no
@beelzabub (sorry for the ping) I don't think the S3 terraform is going to work. AWS uses STS for auth. When I try I get
error configuring Terraform AWS Provider: error validating provider credentials: error calling sts:GetCallerIdentity: operation error STS: GetCallerIdentity, https response error StatusCode: 403, RequestID: aec3d1d9-a733-499a-a35f-ab954b462626, api error InvalidClientTokenId: The security token included in the request is invalid.It doesn't like no object lock.
error creating S3 Bucket (my-tf-test-bucket): NotImplemented: Header 'x-amz-bucket-object-lock-enabled' with value 'false' not implementedYeah, we're pretty strict about headers to avoid having to worry about problems as we add features
Which operation is
x-amz-bucket-object-lock-enabled on?I'll add a carve-out for supporting
falseIt was just on trying to create the bucket
kk. I put up a PR. It's small so it should be merged & included in the next release which will be either Friday or Tuesday
Right. I forgot about that piece. I've been living inside the bubble that is the R2 worker too long :). We'll need to allow people to turn off the buffering at some point so that Workers fronting R2 can handle larger bodies.
@beelzabub are you able to say...
- If/when SHA-256 checksums will be supported in S3 CompleteMultipartUpload operations
(https://docs.aws.amazon.com/AmazonS3/latest/API/API_CompleteMultipartUpload.html#API_CompleteMultipartUpload_RequestSyntax)? - If/when SHA-256 checksums will be supported in bindings with
env.R2.put(body, {sha256: '<checksum>'})?
X-Amz-Content-Sha256 header), so I assume it would be relatively easy to implement it for bindings as well. I don't think the same can be said for calculating the checksum of multipart uploads though.Pages indeed doesn't support R2 yet

wym @derfrisson ? 

- I wouldn't hold my breath
- No immediate plans but I can add it to the backlog
I kinda doubt it? Even S3 has deprecated them as of 2020.
But who knows, I don't speak for the R2 team
SigV2 hasn't been supported on any AWS regions launched after 2013
I don't think it's on the way personally
2013, whew.
The Europe (Frankfurt), US East (Ohio), Canada (Central), Europe (London), Asia Pacific (Seoul), Asia Pacific (Mumbai), Europe (Paris), China (Ningxia), Europe (Stockholm), Asia Pacific (Osaka Local), AWS GovCloud (US-East), and Asia Pacific (Hong Kong) Regions were launched after 2013, and support SigV4 but not SigV2. If you have code that accesses S3 buckets in that region, it is already making exclusive use of SigV4.

It do be oldddddd
What about v3? 

The HyperText Transfer Protocol (HTTP) 411 Length Required client error response code indicates that the server refuses to accept the request without a defined Content-Length header.
R2 requires a
Content-Length header for uploadsIt'll work on S3 when using MP uploads iirc but that's about it