No alerts received within the last 24 hours
cscli capi status looks like it's all good. The console (app.crowdsec.net) shows that it has recently authenticated, and the console has received status, but that signals haven't been retrieved for a couple days. Alerts aren't showing up in the console either. Any suggestions to troubleshoot?crowdsec nginx bouncer without IP
sudo cscli bouncers list
See attached image....
Clean up old log parsers / machines
cscli and the console. The log parsers specifically are old LAPI pods. I understand there are options to automatically clean up old agent and bouncer connections though it apparently doesn't apply to LAPI. Is there a way to cause these to be cleaned up automatically? I know I can cscli machine prune but in a kubernetes environment it's expected that pods are ephemeral, so it seems like there should be a function to autodelete or autopru...help configuration bouncer traefik
Haproxy-Spoa captcha always reload and not redirect to site
Multiple Notifications of the same IP Ban
Strungling with Bouncer Middleware in Traefik 3 on kubernetes.
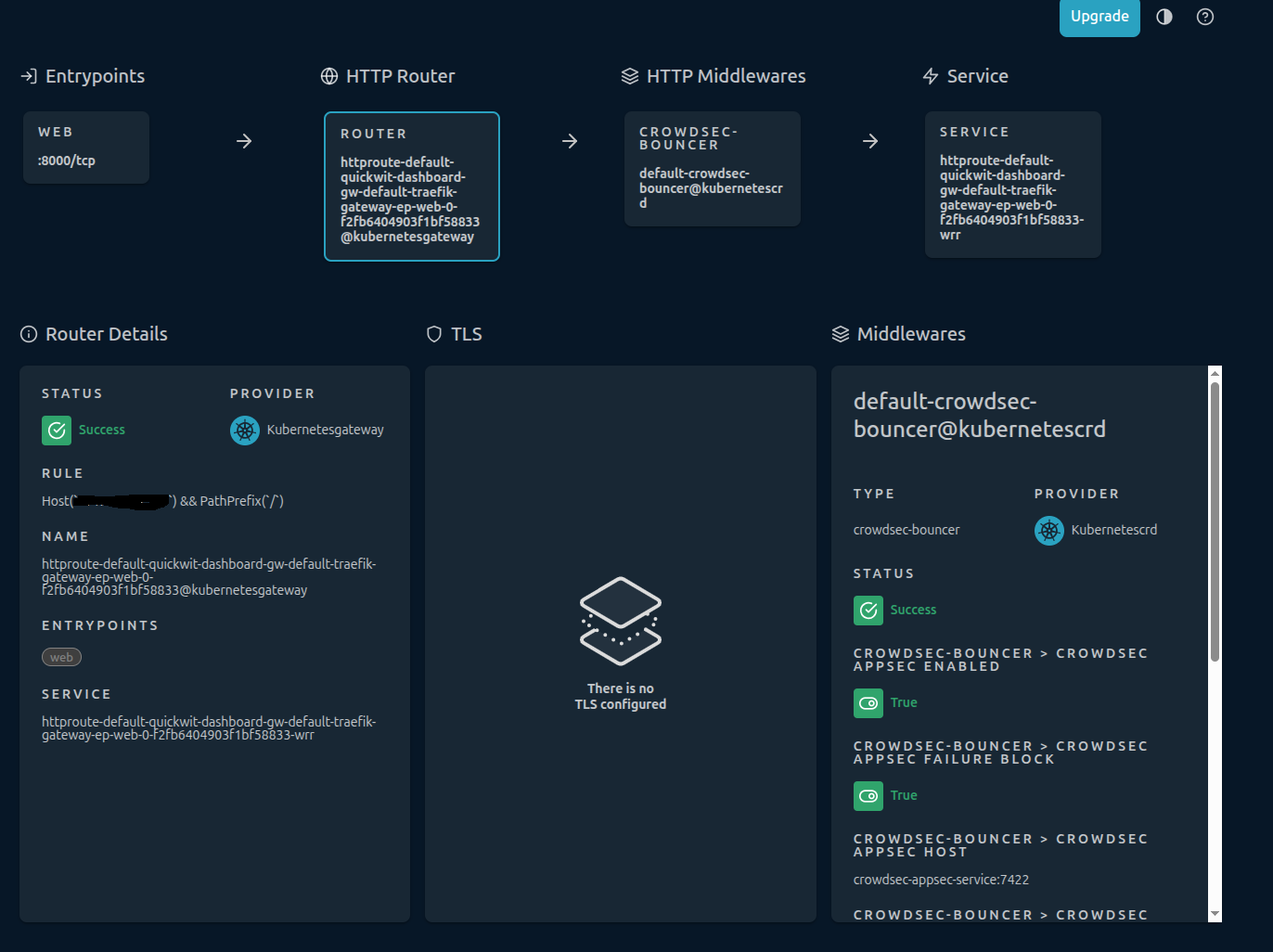
data directive in scenario do not load local file in memory
Remediation components aren't visible
need help with fortigate integration
The recipient server did not accept our requests to connect.mails from gmail blocked by crowdsec
2FA authorization
I sent a support request to support@crowdsec.net on 02.08.25 but haven’t received any reply for over a week.
This completely blocks me from accessing my account....
AppSec ignores X-Crowdsec-Appsec-Ip header from Caddy bouncer, uses connection source IP instead
hslatman/caddy-crowdsec-bouncer, and ruled it out a plugin issue - https://github.com/hslatman/caddy-crowdsec-bouncer/issues/91
Let me know if anyone has a suggestion for where to dig next....Collection Not Banning
LePresidente/overseerr-logs....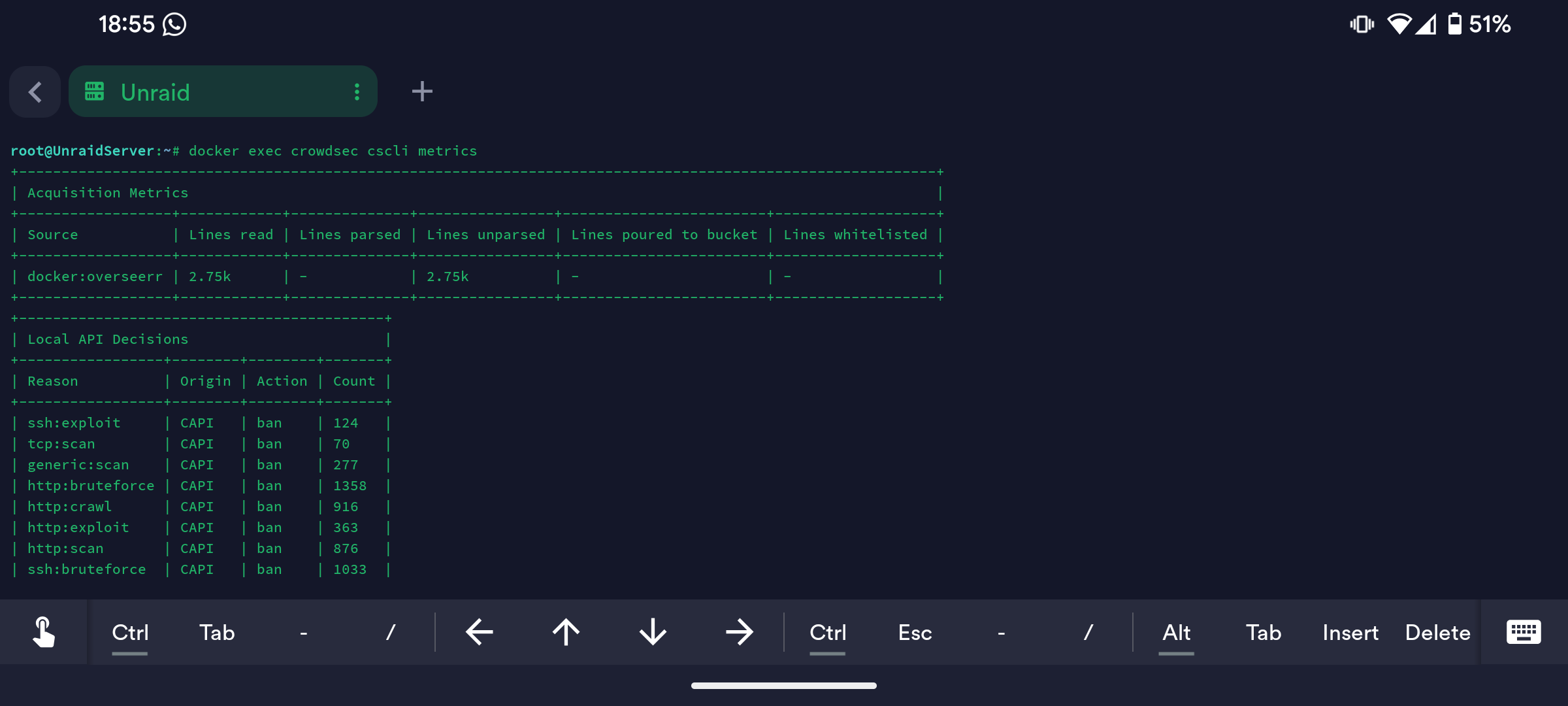
Same IP banned twice 2 hours apart?
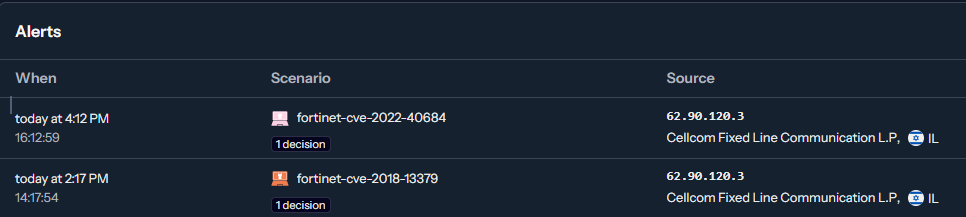
Re: the 6 Aug announcement about updating
prevent notifications for manual add ip/range or use own custom blocklist
Helm chart add allowlist
Openresty bouncer disconnects from CrowdSec
Docker based log parser not connecting to Opnsense running LAPI
sudo cscli lapi register -u http://192.168.20.1:8080 command on my crowdsec docker it says its successful and saves the creds into local_api_credentials.yaml. I then stopped the docker and edit config.yaml in the docker server and disable the server api. On the Opnsense lapi i validate the machine. now whenever trying to start the crowdsec docker it will not start successfully. It gets stuck in a loop of crashing over and over. This can be found in the logs:
...