I believe Access with service tokens in headers and jwt validation on the tunnel is the only truly s
I believe Access with service tokens in headers and jwt validation on the tunnel is the only truly secure way
fetchcaches.default and the cache that fetchfetchfetchcaches.default?

-Os?envprocess.env.API_KEY = env.API_KEY in my fetch handler
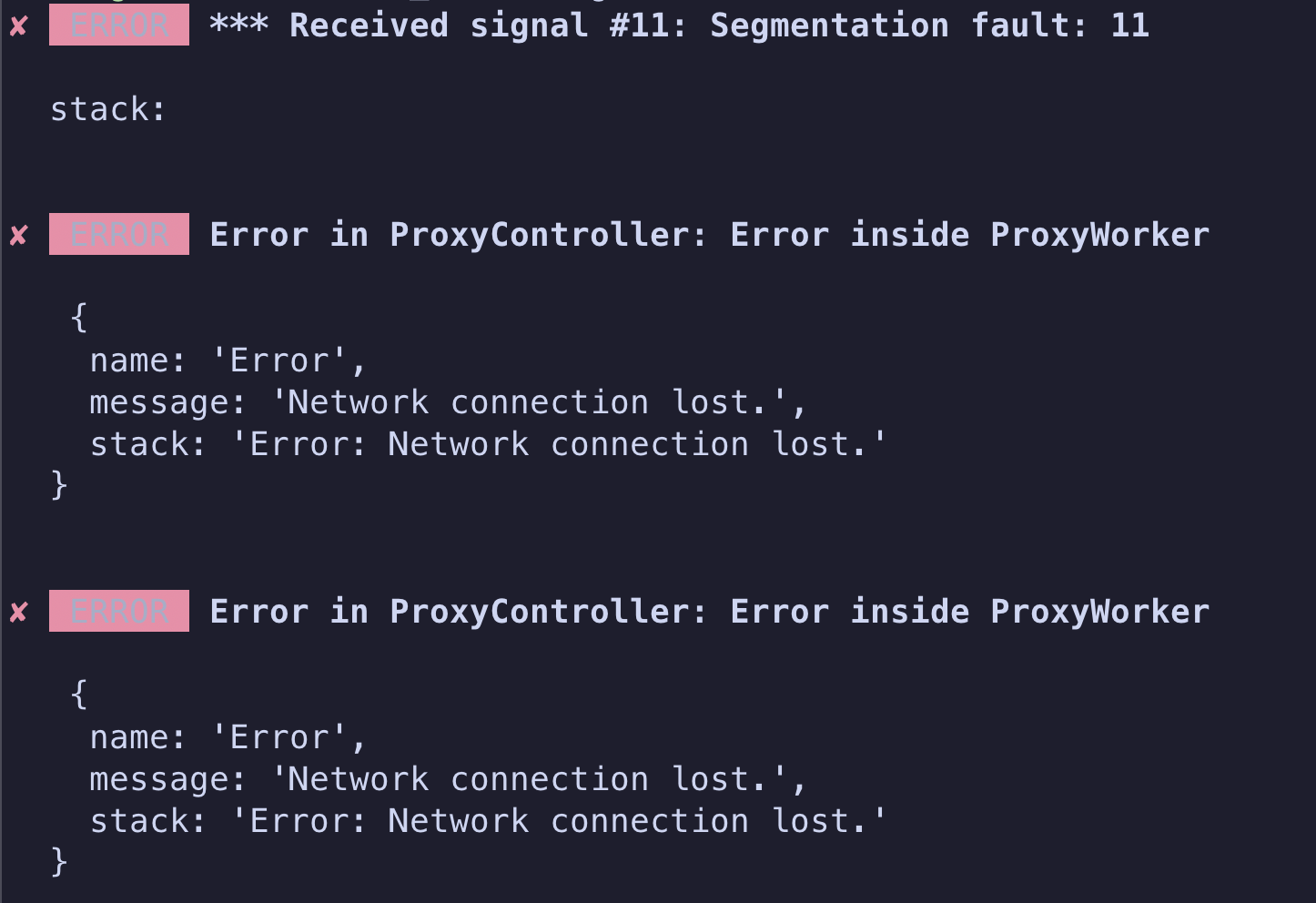
at in them. I know there is a fix PR up but don't remember the number


3.19.0 is my only safe option right?wrangler dev --remote command, but it seems like my DOs aren't updating on the network, that's is intentional? Am I doing something wrong? caches.defaultcaches.default-Osprocess.env.API_KEY = env.API_KEY0_________
"If there is any risk that, pending the hearing of the petition, records may be lost or destroyed, that [object Object]
"If there is any risk that, pending the hearing of the petition, records may be lost or destroyed, that [object Object]
3_________
_________
_________
_________at3.19.0wrangler dev --remote di_output.analyzeResult?.paragraphs?.forEach((paragraph) => {
if(paragraph.content.includes("found the basis for the appointment")) {
console.debug("0_________")
console.debug(paragraph.content)
console.debug(paragraph.content)
console.debug(paragraph.content)
console.debug("1_________")
console.debug("hello?")
}
})
console.debug("3_________")
console.debug("_________")
console.debug("_________")
console.debug("_________")