using JS template literals exposes you to SQL injection btw
using JS template literals exposes you to SQL injection btw
queud after a successfully publishing the event, then run a background process that can retry in case of failures.timeFrom or timeTo value is not a number, then ignore the client request on the worker side.bind() makes it safe: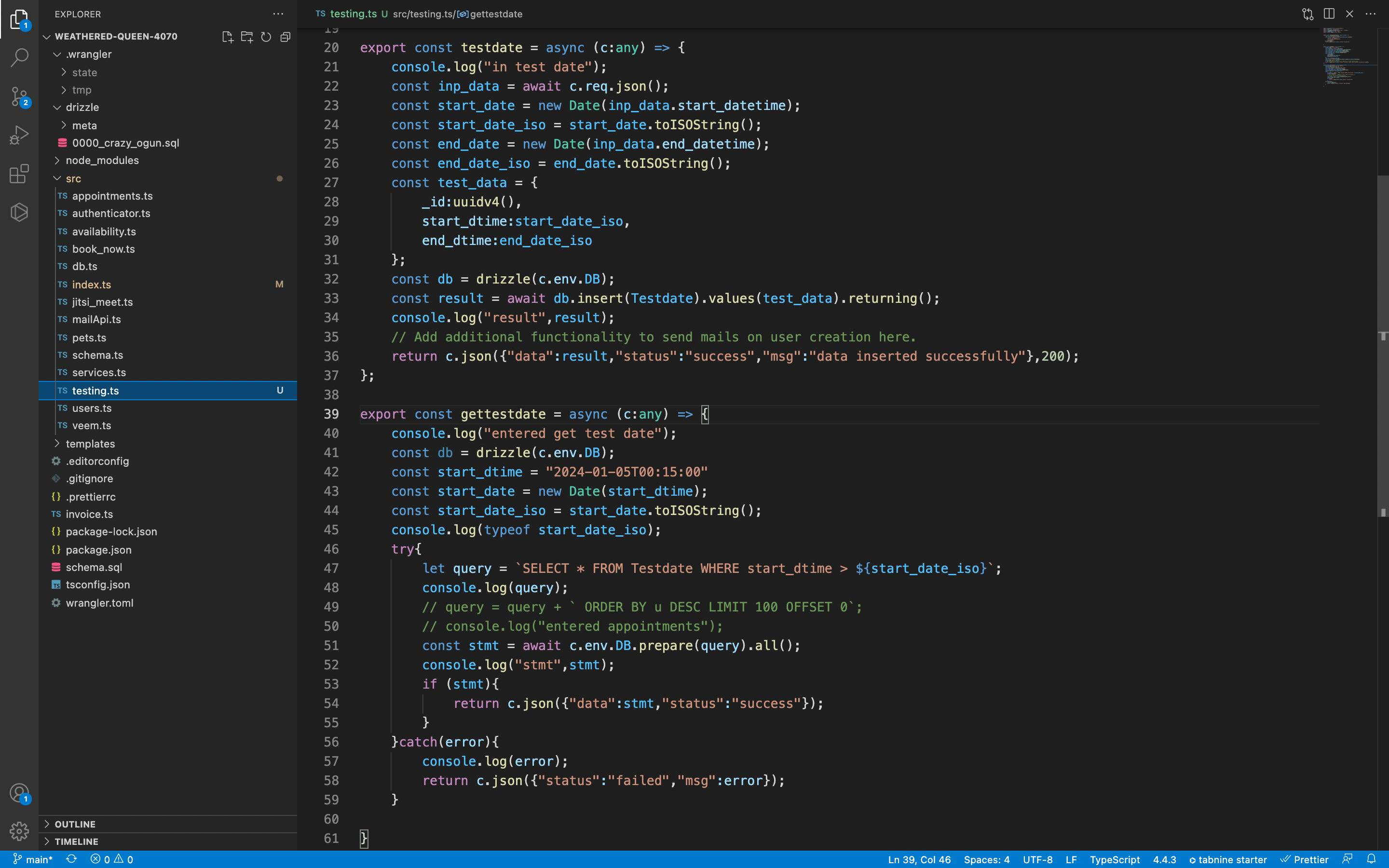
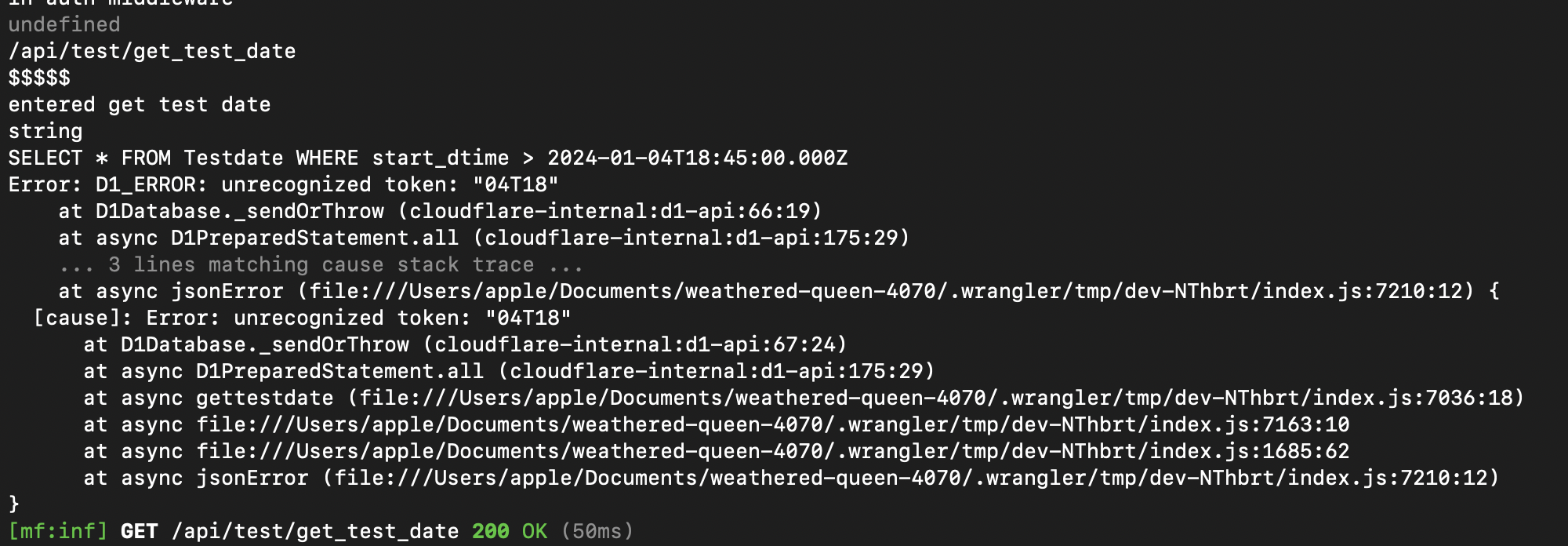
> to compare strings so it wants a number. You should store date time stuff as integers so you can use >. https://atlasforge.gg/wow-classic/population
https://atlasforge.gg/wow-classic/population






queudtimeFromtimeToconst createTable = await env.db.prepare(`
CREATE TABLE IF NOT EXISTS ${tableName} (
id INTEGER PRIMARY KEY AUTOINCREMENT,
blockTs INTEGER,
value TEXT,
INDEX idx_blockTs (blockTs)
)
`).run();.bind()const createTable = await env.db.prepare(`
CREATE TABLE IF NOT EXISTS ?1 (
id INTEGER PRIMARY KEY AUTOINCREMENT,
blockTs INTEGER,
value TEXT,
INDEX idx_blockTs (blockTs)
)
`).bind(tableName).run();Maximum database size 2 GB (Workers Paid) beta / 500 MB (Free)
Maximum storage per account 50 GB (Workers Paid) beta / 5 GB (Free)[[d1_databases]]
binding = "db" # i.e. available in your Worker on env.DB
database_name = "d1"
database_id = "#####################">>