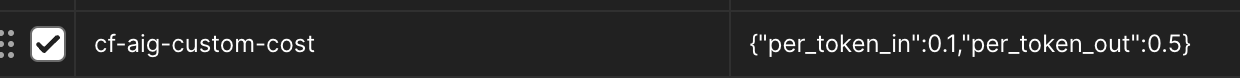
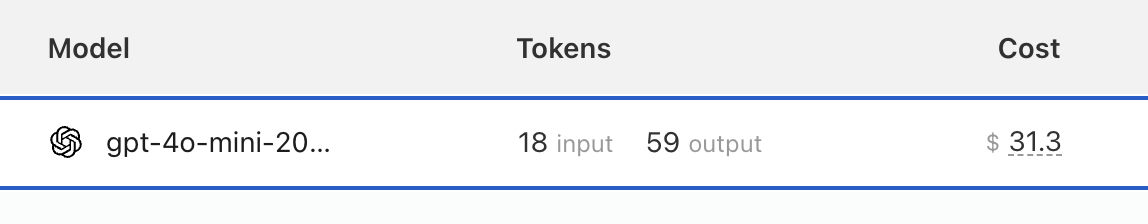
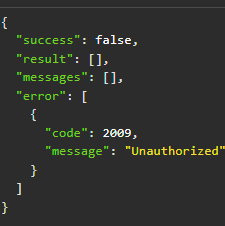
This is super interesting. Thank you for sharing that. From this, and based on the JSON output that
This is super interesting. Thank you for sharing that. From this, and based on the JSON output that was shared... well, I just devised another possible attack which might reveal the encryption keys themselves. It's possible this mitigation technique might create a compromise in its current implementation. Given that discussing it here would be irresponsible, who should I contact, please?